On December 10th, 2025, we received a submission for a Privilege Escalation vulnerability in Advanced Custom Fields: Extended, a WordPress plugin with more than 100,000+ active installations. This vulnerability makes it possible for an unauthenticated attacker to grant themselves administrative privileges by updating the user role on a user action form where a role can be selected.
Props to andrea bocchetti who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $975.00 for this discovery. Our mission is to secure WordPress through defense in depth, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure through the detection and prevention of vulnerabilities, which is a critical element to our multi-layered approach to security.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on December 11, 2025. Sites using the free version of Wordfence received the same protection 30 days later on January 10, 2026.
We provided full disclosure details to the ACF Extended team instantly through our Wordfence Vulnerability Management Portal on December 11, 2025. The vendor acknowledged the report and released the patch on December 14, 2025. We would like to commend the ACF Extended team for their prompt response and timely patch.
We urge users to update their sites with the latest patched version of Advanced Custom Fields: Extended, version 0.9.2.2 at the time of this publication, as soon as possible.
📢 Did you know Wordfence runs a Bug Bounty Program for all WordPress plugin and themes at no cost to vendors? Researchers can earn up to $31,200 per vulnerability, for all in-scope vulnerabilities submitted to our Bug Bounty Program! Find a vulnerability, submit the details directly to us, and we handle all the rest.
Vulnerability Summary from Wordfence Intelligence
Technical Analysis
Advanced Custom Fields: Extended is an addon WordPress plugin for the Advanced Custom Fields plugin, which adds fields, a form manager and much more.
Examination of the code reveals that the plugin uses the insert_user() function in the acfe_module_form_action_user class to handle the insert user form action.
function insert_user($form, $action){
$args = array();
$save = $action['save'];
$user_id = (int) acf_extract_var($save, 'target');
// update user
if($action['type'] === 'update_user'){
// stop action
if(!$user_id){
return false;
}
// set user to update
$args['ID'] = $user_id;
}
// construct user arguments
foreach($save as $user_field => $value){
// name, slug, taxonomy, parent etc...
if(in_array($user_field, $this->fields) && !acf_is_empty($value)){
$args[ $user_field ] = $value;
}
}
// filters
$args = apply_filters("acfe/form/submit_user_args", $args, $form, $action);
$args = apply_filters("acfe/form/submit_user_args/form={$form['name']}", $args, $form, $action);
$args = apply_filters("acfe/form/submit_user_args/action={$action['name']}", $args, $form, $action);
// bail early
if($args === false){
return false;
}
// switch action type
switch($action['type']){
// insert user
case 'insert_user':{
// fallback for empty password
// this should exist, but can be manually deleted within filter above
// and throw a notice
if(!isset($args['user_pass'])){
$args['user_pass'] = '';
}
// insert user
$user_id = wp_insert_user($args);
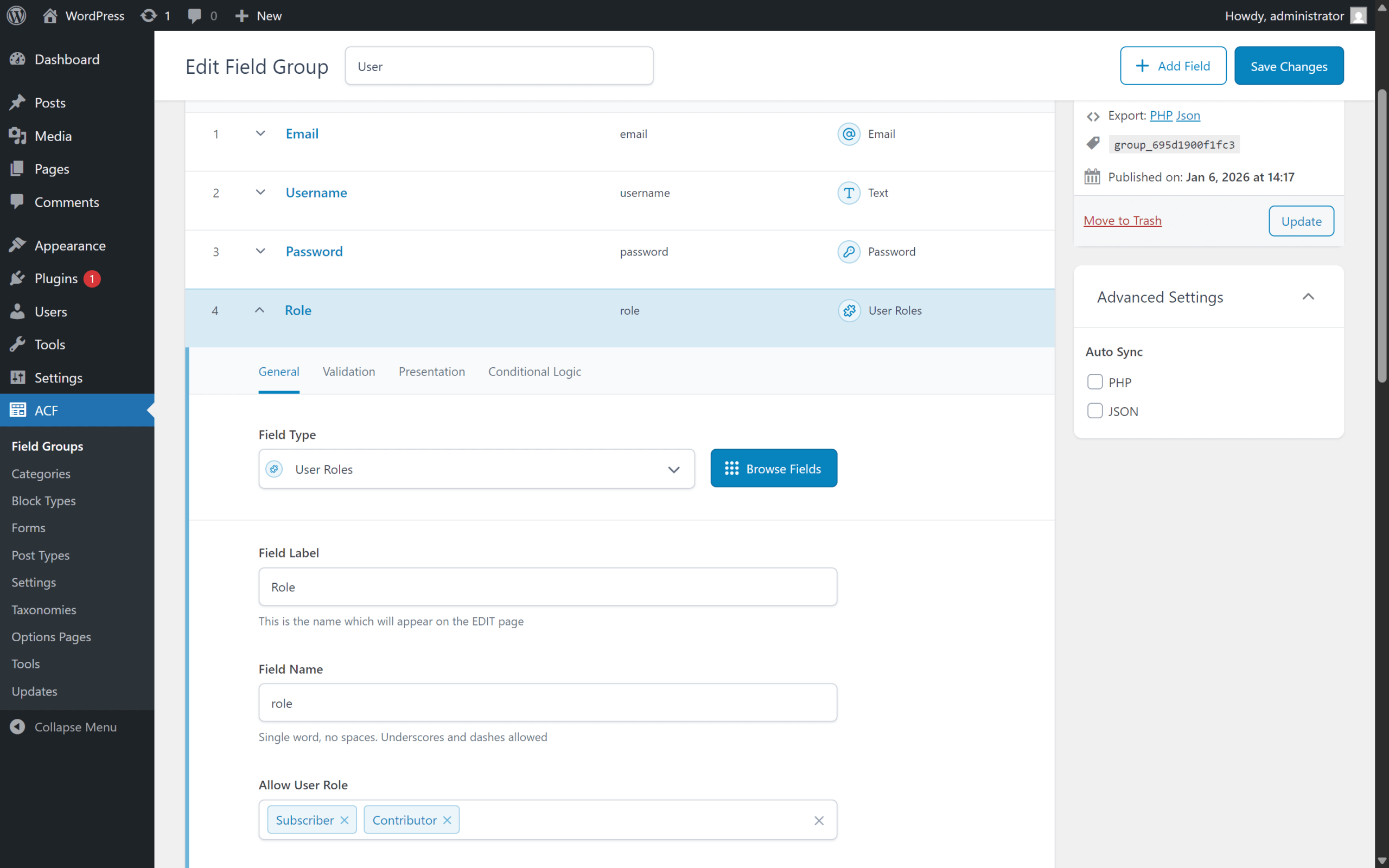
The website owner can add a field group, which contains fields for user data, for example: email, username, password, and role. The role field can be restricted with the “Allow User Role” setting.
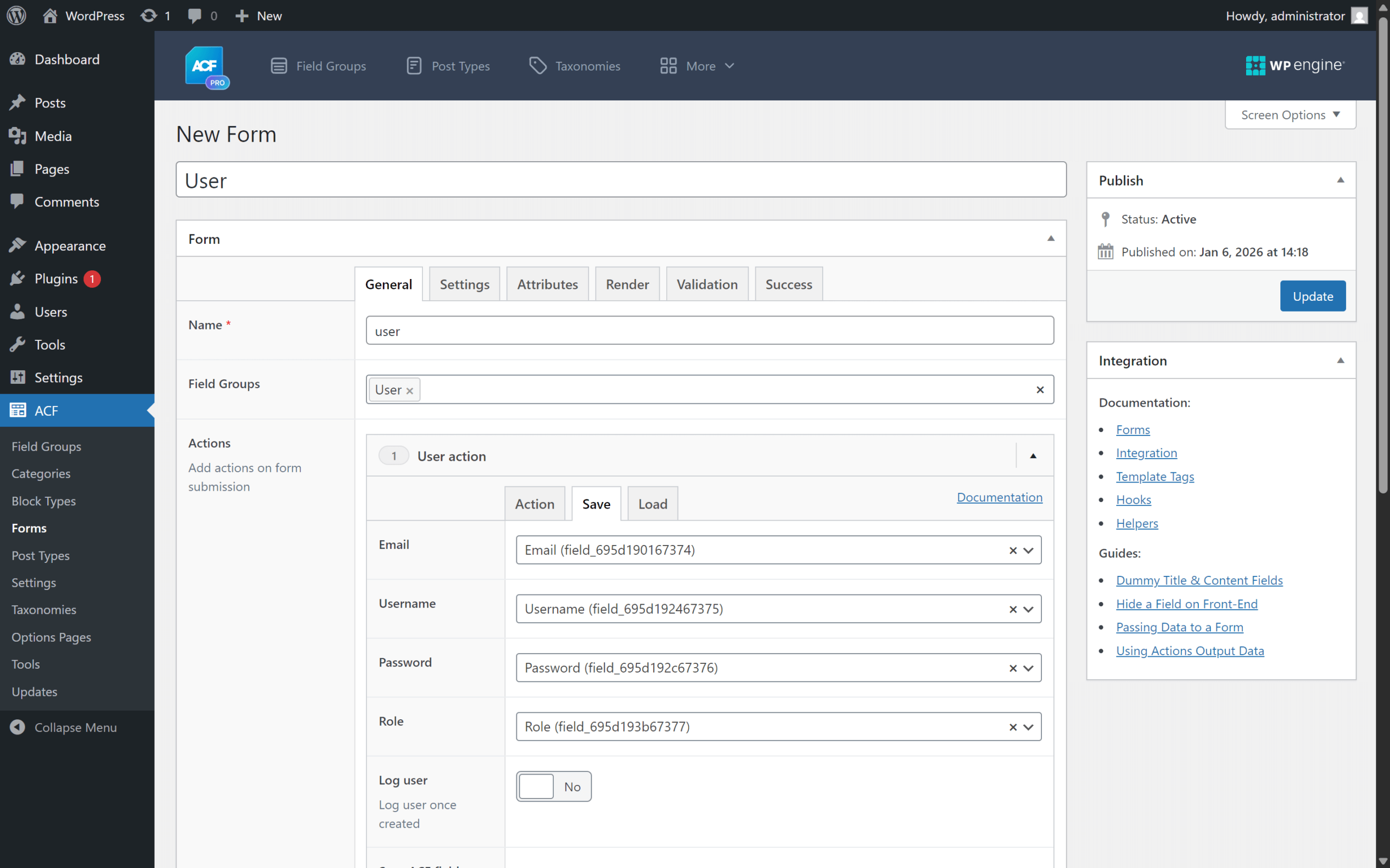
After that, it is possible to add a form with a “Create user” form action, which can be used to create, for example, a registration form with the fields from the previously added field group.
The fields can be mapped to the action.
Due to the fact that the field group contains a restriction option setting for the role field, for example “Allow User Role”, it would be logical and expected for the form to also apply this restriction. Unfortunately, in the vulnerable version, there are no restrictions for form fields, so the user’s role can be set arbitrarily, even to “administrator”, regardless of the field settings, if there is a role field added to the form.
As with any Privilege Escalation vulnerability, this can be used for complete site compromise. Once an attacker has gained administrative user access to a WordPress site they can then manipulate anything on the targeted site as a normal administrator would. This includes the ability to upload plugin and theme files, which can be malicious zip files containing backdoors, and modify posts and pages which can be leveraged to redirect site users to other malicious sites or inject spam content.
This vulnerability only critically affects site owners who have added a “Create user” or “Update user” action form with a role field to their website, which is likely rare.
Disclosure Timeline
December 10, 2025 – We received the submission for the Privilege Escalation vulnerability in Advanced Custom Fields: Extended via the Wordfence Bug Bounty Program.
December 11, 2025 – We validated the report and confirmed the proof-of-concept exploit.
December 11, 2025 – Wordfence Premium, Care, and Response users received a firewall rule to provide added protection against any exploits that may target this vulnerability.
December 11, 2025 – Full disclosure details were sent instantly to the vendor through the Wordfence Vulnerability Management Portal.
December 14, 2025 – The vendor acknowledged the report and began working on a fix.
December 14, 2025 – The fully patched version of the plugin, 0.9.2.2, was released.
January 10, 2026 – Wordfence Free users received the same protection.
Conclusion
In this blog post, we detailed a Privilege Escalation vulnerability within the Advanced Custom Fields: Extended plugin affecting versions 0.9.2.1 and earlier. This vulnerability allows unauthenticated threat actors to gain elevated privileges. The vulnerability has been addressed in version 0.9.2.2 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Advanced Custom Fields: Extended as soon as possible considering the critical nature of this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on December 11, 2025. Sites using the free version of Wordfence received the same protection 30 days later on January 10, 2026.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post 100,000 WordPress Sites Affected by Privilege Escalation Vulnerability in Advanced Custom Fields: Extended WordPress Plugin appeared first on Wordfence.