On September 25th, 2025, we received a submission for a Privilege Escalation vulnerability in WP Freeio, a WordPress plugin bundled in the Freeio premium theme with more than 1,700 sales. This vulnerability makes it possible for an unauthenticated attacker to grant themselves administrative privileges by specifying user role during registration. The vendor released the patched version on October 9th, 2025, and we originally disclosed this vulnerability in the Wordfence Intelligence vulnerability database on October 10th, 2025. Our records indicate that attackers started exploiting the issue on the same day, on October 10th, 2025. The Wordfence Firewall has already blocked over 33,200 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on October 8, 2025. Sites using the free version of Wordfence will receive the same protection after the standard 30-day delay on November 7, 2025.
Considering this vulnerability is under active attack, we urge users to ensure their sites are updated with the latest patched version of WP Freeio, version 1.2.22 at the time of this writing, as soon as possible.
📢 Calling all Vulnerability Researchers and Bug Bounty Hunters! 📢
🚀 Operation: Maximum Impact Challenge! Now through November 10, 2025, earn 2X bounty rewards for all in-scope submissions in software with at least 5,000 active installs and fewer than 5 million active installs. Bounties up to $31,200 per vulnerability. Submit bold. Earn big!
📁 The LFInder Challenge: Refine your LFI hunting skills with an expanded scope. Now through November 24, 2025, all LFI vulnerabilities in software with at least 25 active installs are considered in-scope for all researchers, regardless of researcher tier, AND earn a 30% bonus on all Local File Inclusion vulnerability submissions not already increased by another promotion.
Vulnerability Summary from Wordfence Intelligence
Vulnerability Details
Examining the code reveals that the plugin uses the process_register() function in the WP_Freeio_User class to handle registration.
public static function process_register() {
global $reg_errors;
$do_check = true;
if ( isset($_POST['role']) && $_POST['role'] == 'wp_freeio_employer' ) {
$do_check = check_ajax_referer( 'ajax-register-employer-nonce', 'security_register_employer', false );
$prefix = WP_FREEIO_EMPLOYER_PREFIX;
} elseif ( isset($_POST['role']) && $_POST['role'] == 'wp_freeio_freelancer' ) {
$do_check = check_ajax_referer( 'ajax-register-freelancer-nonce', 'security_register_freelancer', false );
$prefix = WP_FREEIO_FREELANCER_PREFIX;
}
if ( $do_check == false ) {
$return = array( 'status' => false, 'msg' => esc_html__('Security check failed, this could be because of your browser cache. Please clear the cache and check it again.', 'wp-freeio') );
wp_send_json( $json );
}
self::registration_validation( $_POST['email'], $_POST['password'], $_POST['confirmpassword'] );
do_action( 'wp-freeio-registration-validation-after', $prefix );
if ( 1 > count( $reg_errors->get_error_messages() ) ) {
$email = $_POST['email'];
$usernames = explode('@', $email);
$username = sanitize_user( str_replace(' ', '_', strtolower($usernames[0])) );
if (username_exists($username)) {
$username .= '_' . rand(10000, 99999);
if (username_exists($username)) {
$username .= '_' . rand(10000, 99999);
}
}
$userdata = array(
'user_login' => sanitize_user( $username ),
'user_email' => sanitize_email( $email ),
'user_pass' => $_POST['password'],
);
if ( isset($_POST['role']) ) {
$userdata['role'] = $_POST['role'];
}
$userdata = apply_filters( 'wp-freeio-register-user-userdata', $userdata);
$user_id = wp_insert_user( $userdata );
Unfortunately, this function was implemented insecurely, allowing unauthenticated attackers to specify their role without any restrictions, which means they could grant themselves the administrator role.
As with any Privilege Escalation vulnerability, this vulnerability can be used for a complete site compromise. Once an attacker has gained administrative user access to a WordPress site, they can then manipulate anything on the targeted site as a normal administrator would. This includes the ability to upload plugin and theme files, which can be malicious zip files containing backdoors. Additionally, they could modify posts and pages which can be leveraged to redirect site users to other malicious sites or inject spam content.
A Closer Look at the Attack Data
The following data highlights actual exploit attempts from threat actors targeting this vulnerability.
Example attack request
POST /?wpfi-ajax=wp_freeio_ajax_register&action=wp_freeio_ajax_register HTTP/1.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded role=administrator&email=[redacted]@gmail.com&password=[redacted]&confirmpassword=[redacted]
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
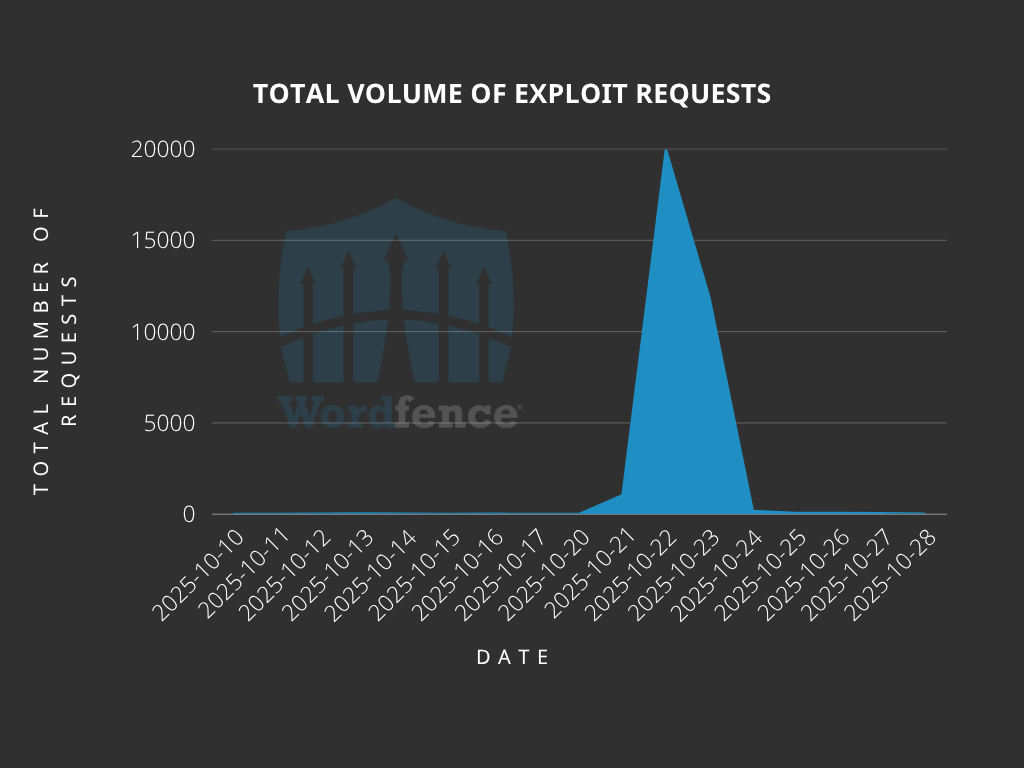
Total Number of Exploits Blocked
The Wordfence Firewall has blocked over 33,200 exploit attempts since the vulnerability was publicly disclosed.
According to our data, attackers started targeting websites the same day the vulnerability was disclosed, on October 10th. We also detected and blocked a large number of exploit attempts from October 21st to 23rd, indicating that attackers may have been getting familiar with the vulnerability prior to launching a mass campaign.
Top Offending IP Addresses
The following IP Addresses are currently the most actively engaged IP addresses targeting the WP Freeio plugin registration function:
- 35.178.249.28
- Over 1500 blocked requests.
- 35.178.250.18
- Over 1400 blocked requests.
- 13.239.253.194
- Over 1300 blocked requests.
- 3.25.204.16
- Over 1300 blocked requests.
- 18.220.143.136
- Over 1300 blocked requests.
- 13.40.54.54
- Over 1200 blocked requests.
- 35.177.84.254
- Over 1200 blocked requests.
- 3.148.213.82
- Over 1200 blocked requests.
- 3.8.127.16
- Over 1200 blocked requests.
- 18.118.154.234
- Over 1200 blocked requests.
Indicators of Compromise
One obvious sign of infection is if a site has a newly added malicious administrator account.
We also recommend reviewing log files for any requests originating from the following IP addresses:
- 35.178.249.28
- 35.178.250.18
- 13.239.253.194
- 3.25.204.16
- 18.220.143.136
- 13.40.54.54
- 35.177.84.254
- 3.148.213.82
- 3.8.127.16
- 18.118.154.234
The absence of any such log entries does not guarantee that your website has not been compromised. We recommend doing a thorough review if you see any abnormal activity or accounts on your site, and you are running a vulnerable version of the software.
Conclusion
In today’s article, we covered the attack data for a critical-severity vulnerability in the WP Freeio plugin that allows unauthenticated attackers to grant themselves administrative privileges by specifying user role during registration. Our threat intelligence indicates that attackers may have started actively targeting this vulnerability as early as October 10th, 2025 with mass exploitation starting on October 21st, 2025. The Wordfence firewall has already blocked over 33,200 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on October 8, 2025. Sites using the free version of Wordfence will receive the same protection after the standard 30-day delay on November 7, 2025.
Even if you have already received a firewall rule for this issue we urge you to ensure that your site is updated to at least version 1.2.22 in order to maintain normal functionality. If you have friends or colleagues running WP Freeio, be sure to forward this advisory to them, as thousands of sites could still be unprotected and unpatched.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
The post Attackers Actively Exploiting Critical Vulnerability in WP Freeio Plugin appeared first on Wordfence.