📢 In case you missed it, Wordfence just published its annual WordPress security report for 2024. Read it now to learn more about the evolving risk landscape of WordPress so you can keep your sites protected in 2025 and beyond.
On April 6th, 2025, we received a submission for an Arbitrary File Read vulnerability in Eventin, a WordPress plugin with more than 10,000 active installations. This vulnerability makes it possible for an unauthenticated attacker to read arbitrary files on the server, which can contain sensitive information.
Props to mikemyers who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $155.00 for this discovery. Our mission is to secure WordPress through defense in depth, which is why we are investing in quality vulnerability research and collaborating with researchers of this caliber through our Bug Bounty Program. We are committed to making the WordPress ecosystem more secure through the detection and prevention of vulnerabilities, which is a critical element to the multi-layered approach to security.
All Wordfence Premium, Wordfence Care, and Wordfence Response customers, as well as those using the free version of our plugin, are protected against any exploits targeting this vulnerability by the Wordfence firewall’s built-in Local File Inclusion protection.
We provided the full disclosure details to the ThemeWinter team on April 7, 2025. The developer released the fully patched version on April 30, 2025. We would like to commend the ThemeWinter team for their prompt response.
We urge users to update their sites with the latest patched version of Eventin, version 4.0.27 at the time of this writing, as soon as possible.
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: Event Manager, Events Calendar, Tickets, Registrations – Eventin
Plugin Slug: wp-event-solution
Affected Versions:
CVE ID: CVE-2025-3419
CVSS Score: 7.5 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
Researcher/s: mikemyers
Fully Patched Version: 4.0.27
Bounty Award: $155.00
The Event Manager, Events Calendar, Tickets, Registrations – Eventin plugin for WordPress is vulnerable to arbitrary file read in all versions up to, and including, 4.0.26 via the proxy_image() function. This makes it possible for unauthenticated attackers to read the contents of arbitrary files on the server, which can contain sensitive information.
Technical Analysis
Eventin is a WordPress event management plugin for organizing and managing events with many features and a user-friendly interface.
Examining the code reveals that the plugin uses the proxy_image() function in the Hooks class to fetch an image from a given URL and serve it to the user, acting as a proxy.
public function proxy_image() {
$action = isset( $_GET['action'] ) ? $_GET['action'] : '';
if ( $action !== 'proxy_image' ) {
return;
}
ob_start();
if ( $_SERVER['REQUEST_METHOD'] === 'OPTIONS' ) {
http_response_code(200);
ob_end_flush();
exit;
}
$imageUrl = isset( $_GET['url'] ) ? $_GET['url'] : null;
if ( $imageUrl ) {
$imageContent = file_get_contents( $imageUrl );
if ( $imageContent !== false ) {
$finfo = finfo_open( FILEINFO_MIME_TYPE );
$mimeType = finfo_buffer( $finfo, $imageContent );
finfo_close( $finfo );
header("Content-Type: $mimeType");
$tempStream = fopen('php://temp', 'r+');
fwrite( $tempStream, $imageContent );
rewind( $tempStream );
fpassthru( $tempStream );
fclose( $tempStream );
} else {
http_response_code(404);
}
} else {
http_response_code(400);
}
ob_end_flush(); // End output buffering
}
Unfortunately, this function does not include any file type or extension checks in the vulnerable version. This means that not only image files can be read, but it is also possible to read .php files.
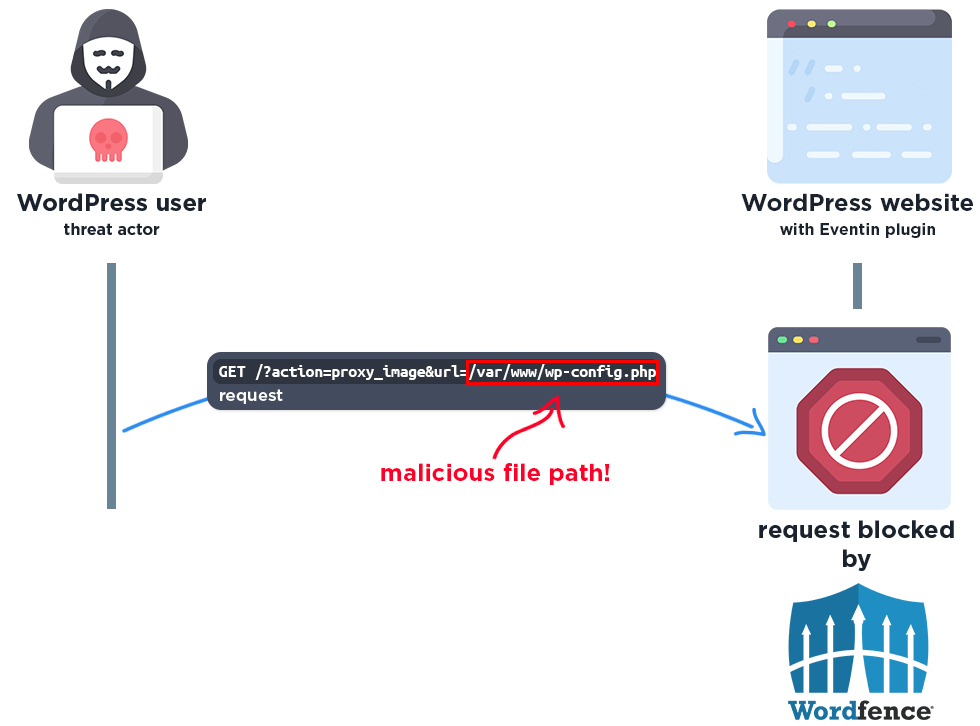
This makes it possible for unauthenticated attackers to read any arbitrary file on the server, including the site’s wp-config.php file, which contains the database settings and authentication unique keys and salts.
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
Disclosure Timeline
April 6, 2025 – We received the submission for the Arbitrary File Read vulnerability in Eventin via the Wordfence Bug Bounty Program.
April 7, 2025 – We validated the report and confirmed the proof-of-concept exploit.
April 7, 2025 – We sent over the full disclosure details to the vendor. The vendor acknowledged the report and began working on a fix.
April 30, 2025 – The fully patched version of the plugin, 4.0.27, was released.
Conclusion
In this blog post, we detailed an Arbitrary File Read vulnerability within the Eventin plugin affecting versions 4.0.26 and earlier. This vulnerability allows unauthenticated threat actors to read arbitrary files, which can contain sensitive information. The vulnerability has been addressed in version 4.0.27 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of Eventin as soon as possible considering the critical nature of this vulnerability.
All Wordfence users, including those running Wordfence Premium, Wordfence Care, and Wordfence Response, as well as sites running the free version of Wordfence, are fully protected against this vulnerability.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
The post 10,000 WordPress Sites Affected by Arbitrary File Read Vulnerability in Eventin WordPress Plugin appeared first on Wordfence.