On April 8th, 2024, we released our 2024 Annual WordPress Security Report, highlighting key trends and insights across the evolving landscape of WordPress security. Today, we want to shine a spotlight on Wordfence’s contributions through our Bug Bounty Program, and reaffirm our commitment to high-quality vulnerability research, respectful and responsible disclosure, and free, high-impact vulnerability intelligence all shared openly via our API and webhooks and integrated into the Wordfence plugin.
Today, we’re examining Wordfence’s vulnerability data for 2024 and 2025, and comparing it to other WordPress Certified Numbering Authorities (CNAs) and vulnerability data providers. This report will demonstrate why Wordfence is the undisputed leader in WordPress vulnerability intelligence and WordPress security.
While we continue to prioritize meaningful, actionable research, we’ve observed a concerning trend among other WordPress CNAs who focus on quantity over quality, using inflated vulnerability counts to claim “leadership.” What we’ve found is that this emphasis on quantity often results in low-quality validation, poor disclosure practices, increased vulnerability noise, and misused resources across the ecosystem, from researchers and software developers to the WordPress.org Plugins Team.
Wordfence believes that true leadership and value in the field of vulnerability intelligence is not measured by the total number of vulnerabilities or CVEs assigned and processed. Instead, it’s demonstrated through the quality, integrity, impact, and responsibility of the vulnerabilities managed through your company. Value lies in attracting and responsibly disclosing high-quality vulnerabilities, and high-impact, actionable threat intelligence is a true measure of leadership.
That’s why our Bug Bounty Program and vulnerability disclosure process are designed with a quality-first mindset, to drive meaningful improvements in WordPress security, empower developers and security researchers, and protect the wider community. This is exactly how we stand out from other WordPress CNAs and why we are the number one provider of actionable WordPress vulnerability intelligence.
TL;DR: Highlights From The Report
- 8,233 distinct new WordPress vulnerabilities published in 2024 were added to the Wordfence Intelligence Vulnerability Database. Wordfence processed 41.7% of the total.
- 4,534 distinct new WordPress vulnerabilities already added in 2025, as of April 28th. Wordfence processed 29% of the total.
- Wordfence processed 65.8% of all vulnerabilities disclosed in software with at least 50,000 active installs in 2024 and 47.5% of all vulnerabilities disclosed in software with at least 1,000 active installations
- Wordfence has already processed 68.2% of those in software with at least 50,000 active installations, and 49.8% of those with at least 1,000 active installations so far in 2025.
- Wordfence processed 45.2% of all High Threat Vulnerabilities in 2024, 66.7% of all high threat vulnerabilities in software with at least 50,000 active installations and 63.6% of all high threat vulnerabilities in software with at least 1,000 active installations.
- Wordfence has already processed 66.5% of the total in 2025, 73.3% of those in software with at least 50,000 active installations, and 83% of those with at least 1,000 active installations so far in 2025.
- Wordfence processed 46% of all Common and Dangerous Vulnerabilities in 2024, 85.5% of all common and dangerous vulnerabilities in software with at least 50,000 active installations and 57.9% of all common and dangerous vulnerabilities in software with at least 1,000 active installations.
- Wordfence has already processed 41.5% of the total in 2025, 82.6% of those in software with at least 50,000 active installations, and 75.4% of those with at least 1,000 active installations so far in 2025.
- Other WordPress CNAs excel at processing and disclosing low-impact vulnerabilities that creates significant noise in the WordPress space.
- 73.8% of one CNA’s 3,016 vulnerabilities (by software affected) disclosed in 2025 are in software with fewer than 1,000 active installations, and 30% of the 3,016 are in software with fewer than 100 active installations.
- The other CNA has only published 217 vulnerabilities this year, and 85.7% of them are low-risk, unlikely to be targeted in mass vulnerabilities.
- Wordfence maintains the highest patched to unpatched publication ratio in both 2024 and 2025, with one CNA maintaining an exceedingly high unpatched publication rate of 69.6%.
- Wordfence maintains one of the lowest rates of low risk vulnerability disclosures in both 2024 and 2025.
- Two major concerns among other WordPress CNAs is a drastically increased rate of disclosures in software with fewer than 1,000 active installations, and more specifically 100 active installations, and a drastic increase in the number of unpatched vulnerabilities being disclosed.
- 69.6% of all vulnerabilities published by Patchstack are still unpatched at the time of creating this report, and 73.8% of all the vulnerabilities published by Patchstack this year are in software with fewer than 1,000 active installs. A clear sign of volume prioritization over remediation and risk prioritization.
- Wordfence expects our rate of vulnerability disclosures to decrease over 2025 while our ratio of high impact high threat issues continues to increase as we hone in our mission to secure the WordPress ecosystem through quality vulnerability research.
- Wordfence is not just the leading WordPress vulnerability intelligence provider based on the data. We are also the clear leader because we provide the information back to the community completely for free, have a very comprehensive data set, are founder owned and operated, ISO27001 certified, and our threat intelligence department is operated by a highly skilled and credentialed team of researchers and analysts.
Our data shows Wordfence is the world’s leading source of actionable vulnerability intelligence. Wordfence isn’t just publishing vulnerabilities, we’re publishing the ones that matter. Relying on Wordfence as a vulnerability intelligence data source ensures that you’ll be the first to know about the most impactful and highest threat vulnerabilities. Other vulnerability providers will notify you first about issues that likely won’t affect the majority of your users, while delaying notification on the most impactful and highest threat vulnerabilities that come from Wordfence.
By utilizing Wordfence’s completely free Wordfence Intelligence API or Webhook integration, or Wordfence plugin’s Web Application Firewall (WAF) and vulnerability scanner, you’ll be the first to know and the first to be protected against vulnerabilities that will likely impact the sites you protect.
While this means you might have a slight delay on the low-risk vulnerability data procured by other database providers, we are certain that is a much better risk tradeoff than having a delay on the protection and notification of vulnerabilities that are more likely to affect your site.
Brief Overview of Vulnerabilities Published in 2024 & 2025
To provide some background, there are three core Certified Numbering Authorities (CNAs) providers for WordPress vulnerabilities: Wordfence, Patchstack, and WPScan. All three providers are able to assign CVE IDs to vulnerabilities in WordPress as CNAs, so nearly all WordPress vulnerabilities discovered in the ecosystem will go through one of these three providers for a CVE. There are some other CNAs that are also authorized to assign CVEs to WordPress software as needed, however, it’s far less common for them to assign CVEs.
Wordfence is the leading provider of actionable and valuable vulnerability intelligence, while Patchstack focuses on high-volume vulnerability reporting, and WPScan primarily finds vulnerabilities internally. All three organizations have Bug Bounty Programs, but only Wordfence and Patchstack offer programs that are fully public and open to everyone.
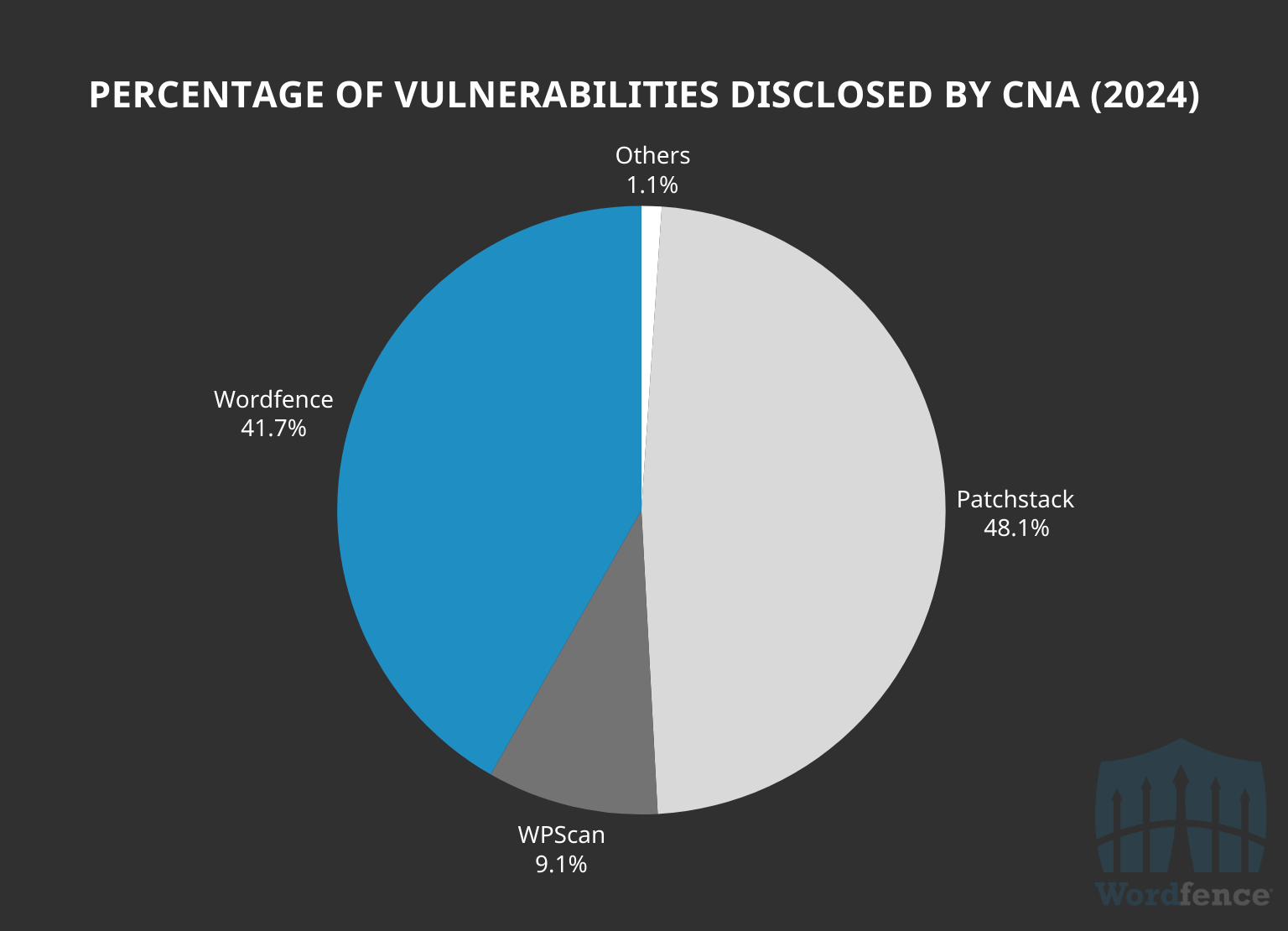
In 2024, Wordfence added 8,233 distinct new WordPress vulnerabilities to the Wordfence Intelligence Vulnerability Database, with a total of 8,427 vulnerabilities if counting by distinct pieces of software affected.
Wordfence assigned 41.7% of all CVEs (3,437), while Patchstack assigned 48.1% (3,958), WPScan assigned 9.1% (750), and other CNAs accounted for the remaining 1.1% (91). All vulnerabilities, regardless of their source, were added to the Wordfence Intelligence Vulnerability Database, highlighting our comprehensive coverage.
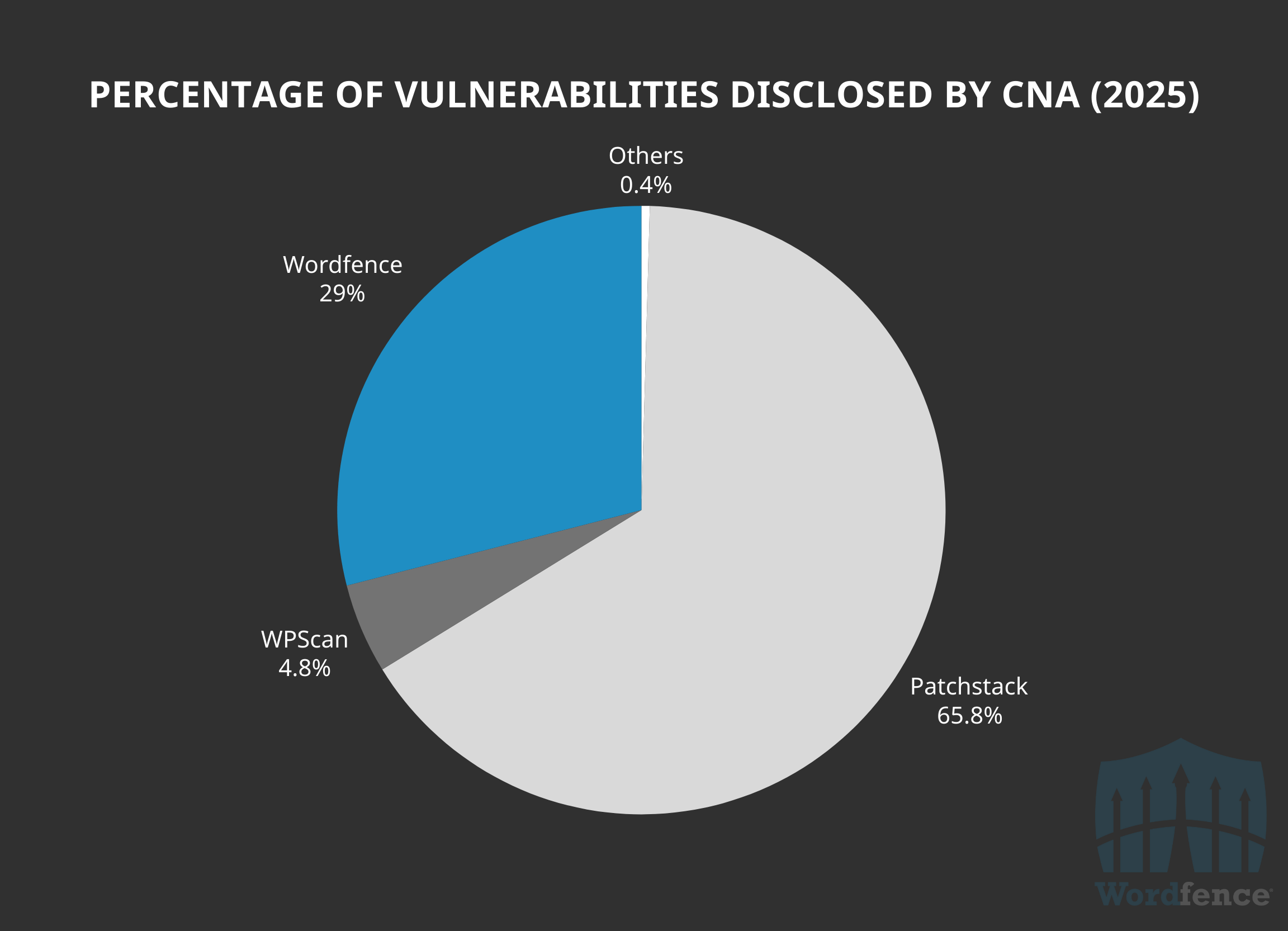
So far in 2025, Wordfence has already added 4,534 new WordPress vulnerabilities to the Wordfence Intelligence Vulnerability Database.
Out of those, Wordfence has assigned 29% of all the CVEs (1,314). Patchstack has assigned 65.8% of all the CVEs (2,982) and WPScan has assigned 4.8% of all of the CVEs (217).
While it may initially seem like Wordfence doesn’t lead the pack in vulnerability intelligence simply based on volume of CVEs assigned, what you’ll find in this report highlights how we lead the pack in vulnerability intelligence based on the value of the vulnerabilities we attract and process. Wordfence isn’t just trying to remediate the most vulnerabilities, we’re trying to remediate the most vulnerabilities that matter and fostering an environment through our Bug Bounty Program that drives that goal.
This year we expect that we won’t lead on volume as we continue to hone in our mission of providing the highest quality vulnerability intelligence. Instead we will continue being the industry leader in vulnerability intelligence on quality and value based on impact and real-world threat. We have taken proactive measures this year to discourage bulk bounty hunting through our Bug Bounty Program, enabling us to focus on critical issues. This strategic shift explains the decrease in our disclosures, while other WordPress CNAs may experience an increase as they work to expand their scope and further boost their number of reports, regardless of real world threat.
Wordfence isn’t just publishing vulnerabilities—we’re publishing the ones that matter. Whether you’re a site owner, developer, or security professional, the data shows that Wordfence delivers deeper, more targeted, and more actionable vulnerability intelligence than any other CNA in the WordPress space. That is why you should rely on Wordfence Intelligence as a vulnerability data provider, and Wordfence security for the best and fastest WordPress protection and detection in the industry.
Wordfence: The Leader in Impactful Vulnerability Intelligence
One way we measure the quality of our vulnerability intelligence is impact. This means how many site owners are affected by a vulnerability in a plugin or theme that we secure each time we work with a security researcher and vendor to patch a vulnerability.
Generally, the most impactful vulnerabilities are in software with at least 50,000 installs because that affects the most number of sites, however, anything with greater than 1,000 active installs still has a considerable impact.
We consider anything with fewer than 1,000 active installations to be extremely low impact. This is due to the fact that there would be very few targets containing any discovered vulnerabilities when there is such a small user base. Even though WordPress powers over 40% of the internet, the odds are not in the favor of an attacker when a plugin has somewhere between 0 and 1,000 active installs compared to a plugin with an install base like 50,000. This makes vulnerabilities with low install counts a far less attractive target for attackers.
In addition, a fair amount of the vulnerabilities found in software with fewer than 1,000 active installations are in abandoned software with a developer that no longer plans to maintain the software, so instead of actually securing software it’s also just creating noise in the space and resulting in a bunch of unpatched vulnerabilities that does nothing to actually help protect sites. We generally discourage research through our program in software with fewer than 1,000 active installs, unless it’s a high risk issue that could still see active exploitation despite the low install count.
The bounties we award in our Bug Bounty Program scale with the number of active installs a piece of software has in hopes that we direct researcher’s focus on larger install count software that has a greater impact. This is one example of how we designed our Bug Bounty Program with quality in mind, and we are seeing the results.
Why do we measure the quality of vulnerability intelligence based on impact?
The number of sites impacted by a vulnerability directly determines how widespread the risk is, and how attractive that target becomes for attackers.
When considering potential targets, attackers will typically prioritize widely-used plugins over those with limited installations. A plugin with 50,000 installations presents a considerably more attractive target than one with only 100 installations, due to the potential for widespread impact. Vulnerabilities in widely-used plugins not only increase the possibility of mass exploitation but also pose a more significant risk to the entire WordPress ecosystem.
Attackers are opportunistic. They want maximum return for minimal effort. Writing a single exploit that can compromise 50,000 sites is far more appealing than writing 500 separate exploits for obscure plugins with little reach and even less payoff.
That’s why at Wordfence, we don’t just count vulnerabilities, we focus on the ones that matter. Our mission is to deliver high-impact intelligence that defenders can act on, and that attackers are most likely to weaponize. This is exactly why it’s critical to choose a vulnerability intelligence provider and security solution, like Wordfence, that prioritizes quality over quantity. It ensures you’re detecting the threats that truly matter to your site and the ones you protect, and that you’re among the first to be protected when vulnerabilities that are likely to be targeted are disclosed.
Wordfence Responsibly Disclosed the Most Vulnerabilities that Affected the Most Sites in 2024
In 2024, there were roughly 1,734 vulnerabilities published that affected WordPress software with at least 50,000 active installations, this is approximately 21% of all vulnerabilities disclosed.
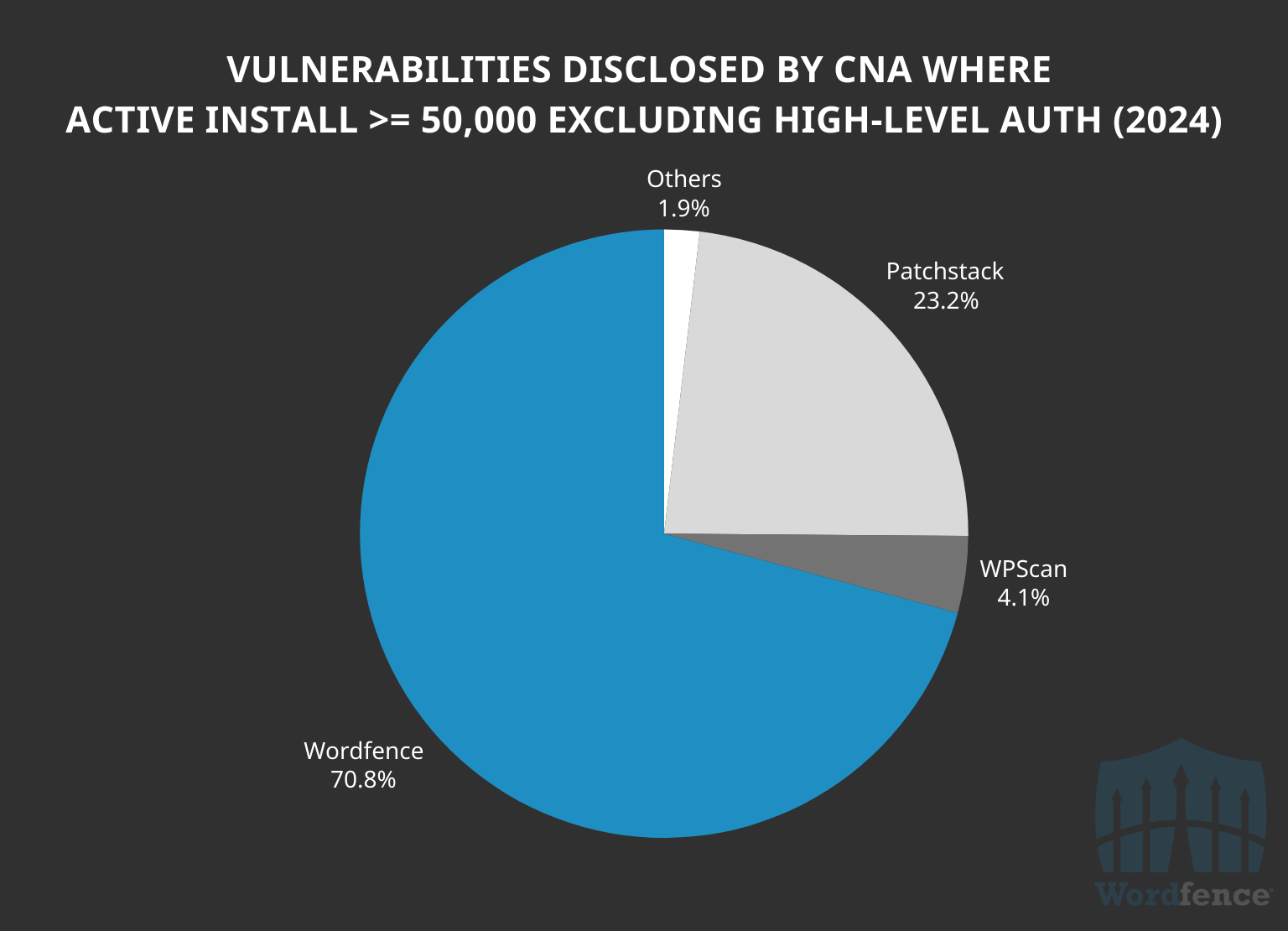
Wordfence published 65.8% of all the vulnerabilities in software with at least 50,000 active installs. Further, if we exclude high-level authentication required vulnerabilities, (i.e. Administrators, Editors, Shop Managers) then the percentage of vulnerabilities published and remediated by Wordfence increases to 70.8% out of the 1,493 in this install range. This is substantially more than all other WordPress CNAs, even when combined. This demonstrates how we attract, and are the first to protect and disclose, vulnerabilities that impact the greatest number of sites.
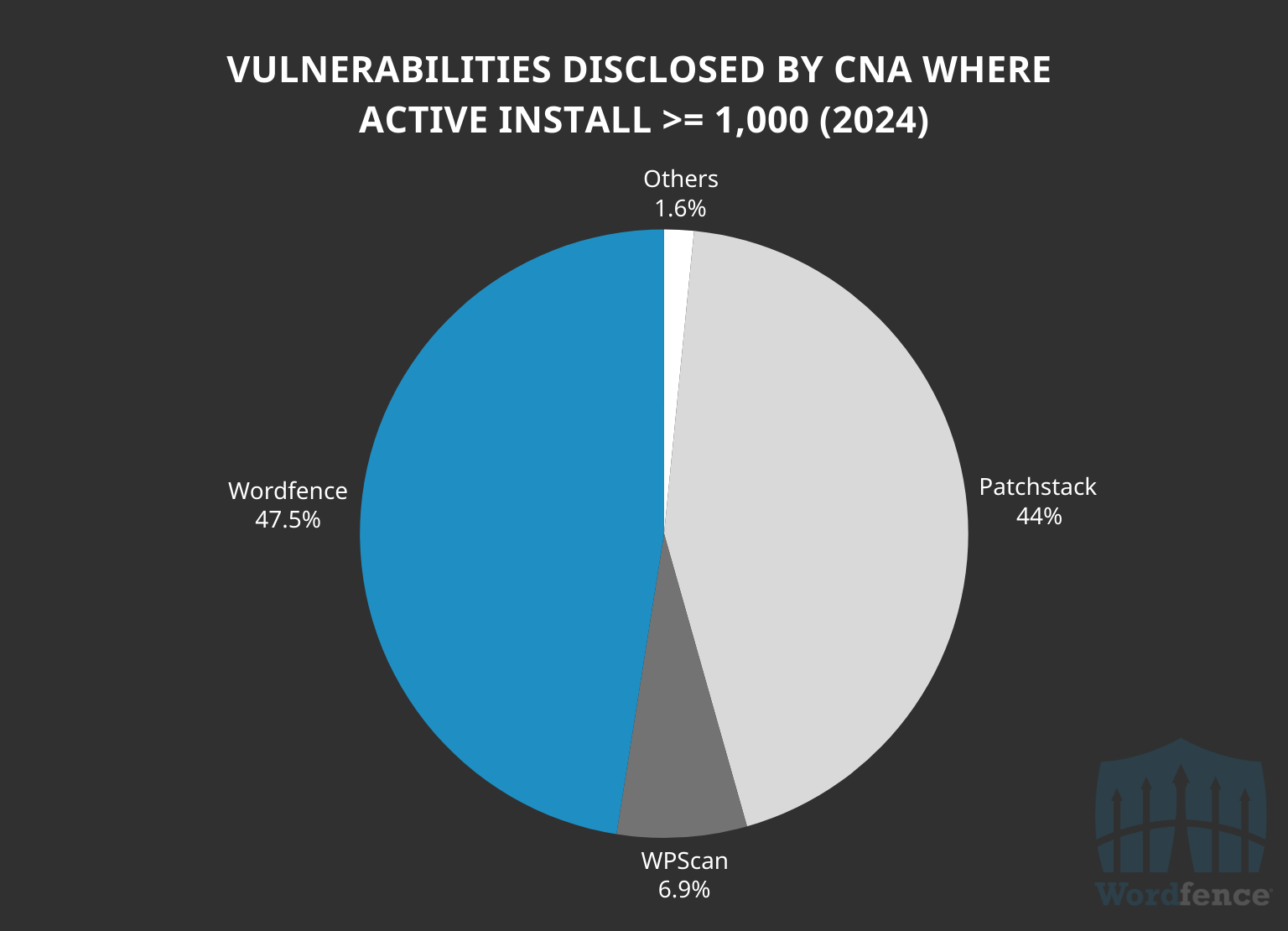
In addition, Wordfence processed and disclosed 47.5% of the 5,912 vulnerabilities affecting software with at least 1,000 active installations in 2024. Wordfence led the industry in this area, again demonstrating our ability to attract, prioritize and address vulnerabilities that pose the greatest risk to the WordPress ecosystem as whole.
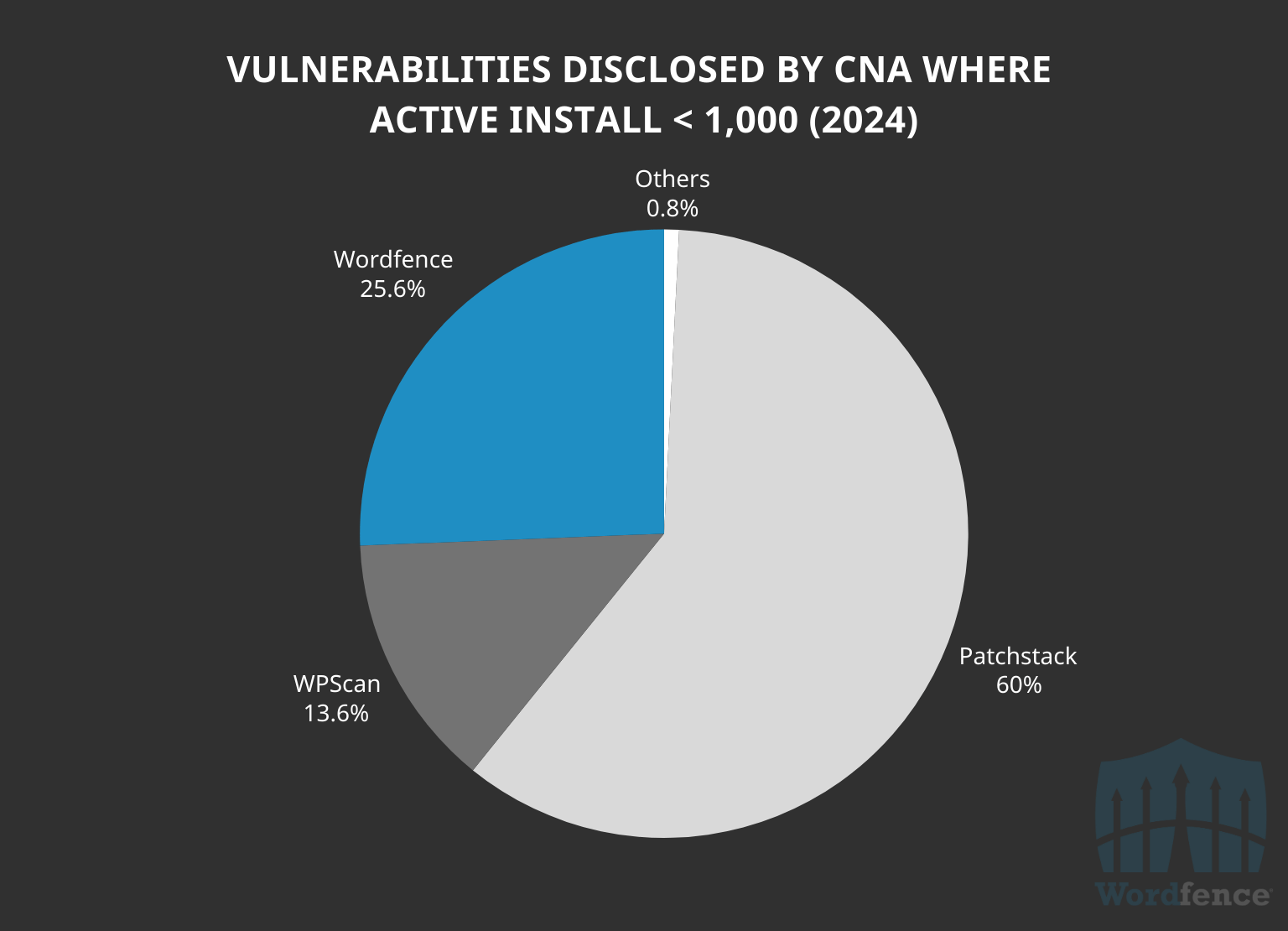
Out of the 2,152 vulnerabilities in software with fewer than 1,000 active installations, Wordfence only processed about 25.6% of the total. Conversely, Patchstack processed 60% of all the vulnerabilities in this software. This highlights how Wordfence is the clear leader in high-impact vulnerabilities, while other WordPress CNAs lead in low-impact vulnerabilities.
Wordfence Continues to Attract and Disclose the Most Impactful Research that Affects the Most Sites in 2025
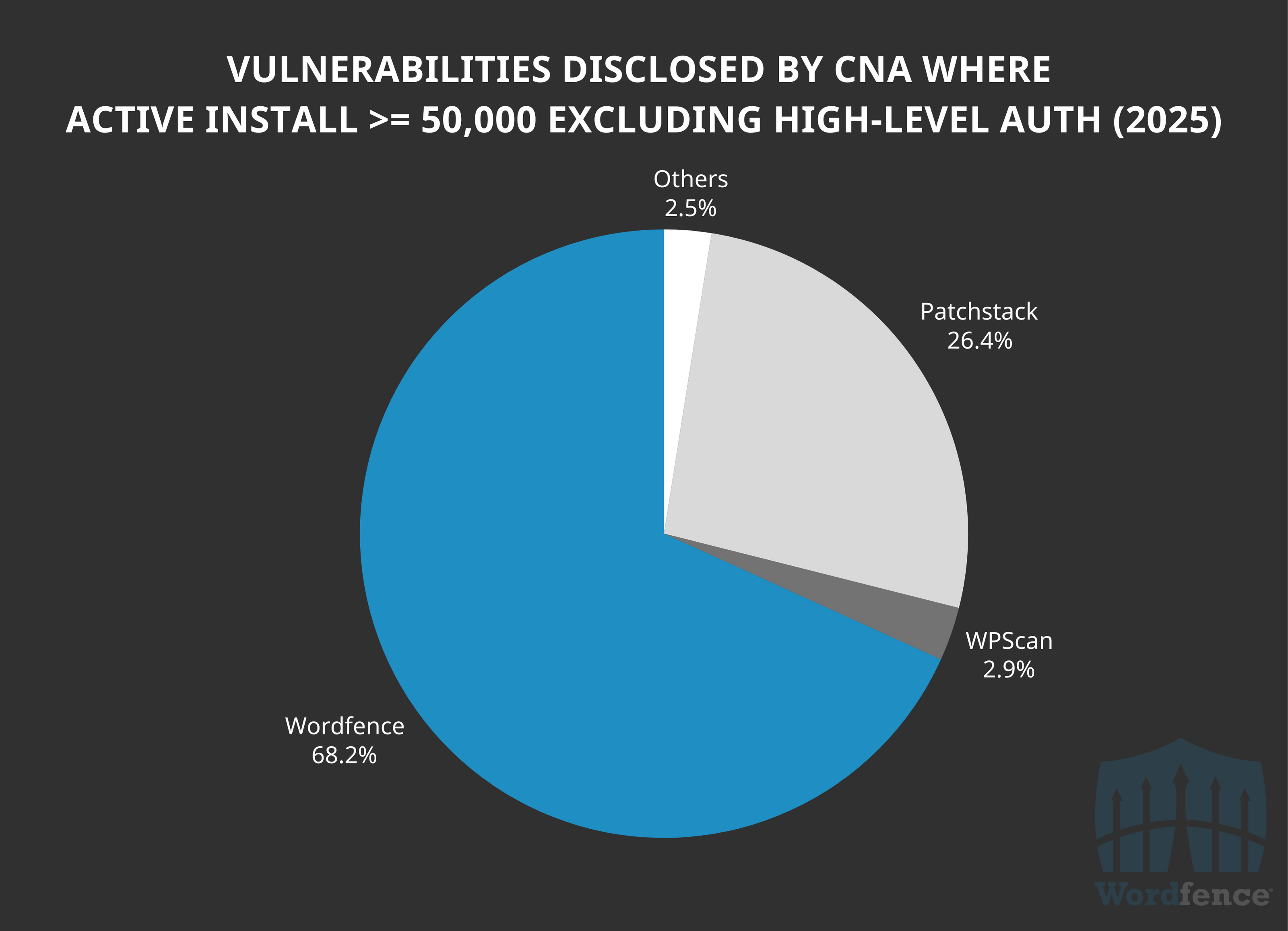
Wordfence is still leading the pack in 2025 for vulnerabilities disclosed in software with at least 50,000 active installations. Wordfence has already published 61.6% of all 357 CVEs assigned in this install count range in 2025, and 68.2% of all 280 vulnerabilities in the install count range, when excluding high-level authentication required vulnerabilities.
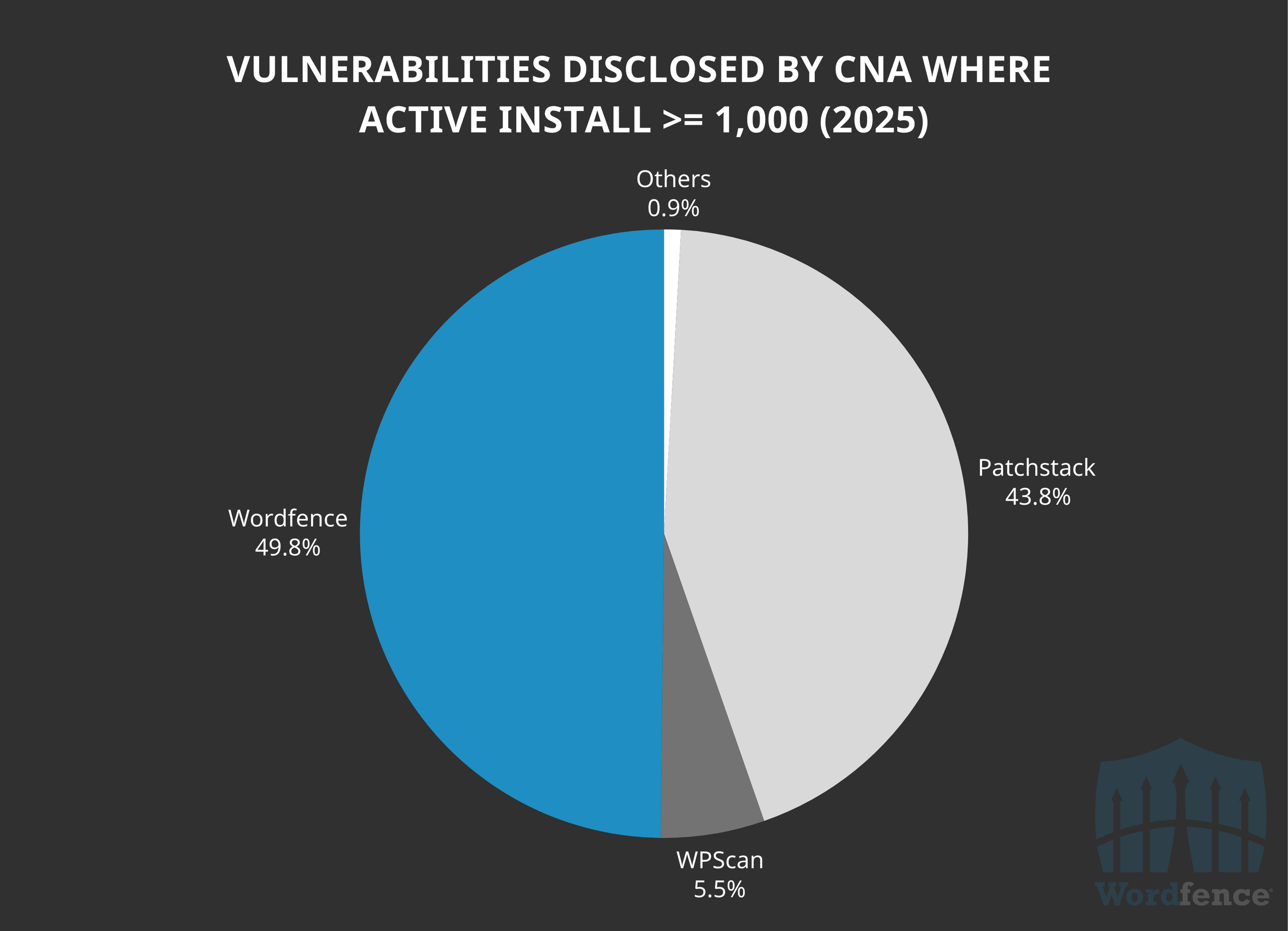
Further, Wordfence is still leading the charge on processing and remediating vulnerabilities in software with at least 1,000 active installations, with Wordfence processing and diclosing 49.8% of all 1,666 vulnerabilities in this install count bracket.
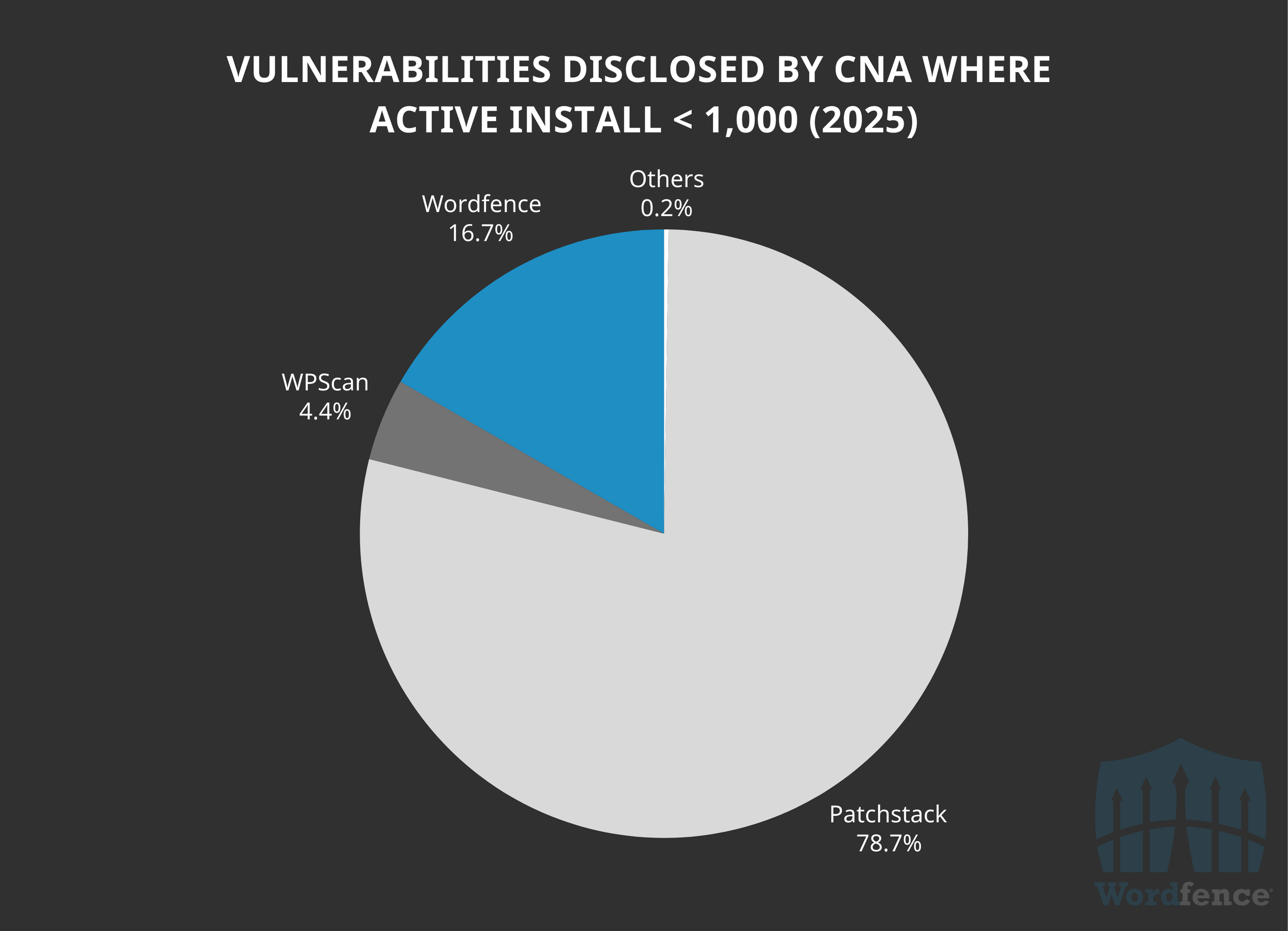
Other WordPress CNAs continue to beat us on software with very low impact – fewer than 1,000 active installations, however, at a far more substantial rate so far this year. Patchstack has processed and disclosed 78.7% of all 2,830 vulnerabilities where the affected software has fewer than 1,000 active installations.
More interestingly, 73.8% of all the vulnerabilities assigned and disclosed by Patchstack are in software with fewer than 1,000 active installations. A clear sign that Patchstack’s attention to volume over quality is creating a lot of vulnerability noise for low-impact issues that likely won’t impact the majority of real-world sites.
The same goes for WPScan where 56.9% of their vulnerabilities processed only affect software with fewer than 1,000 active installations.
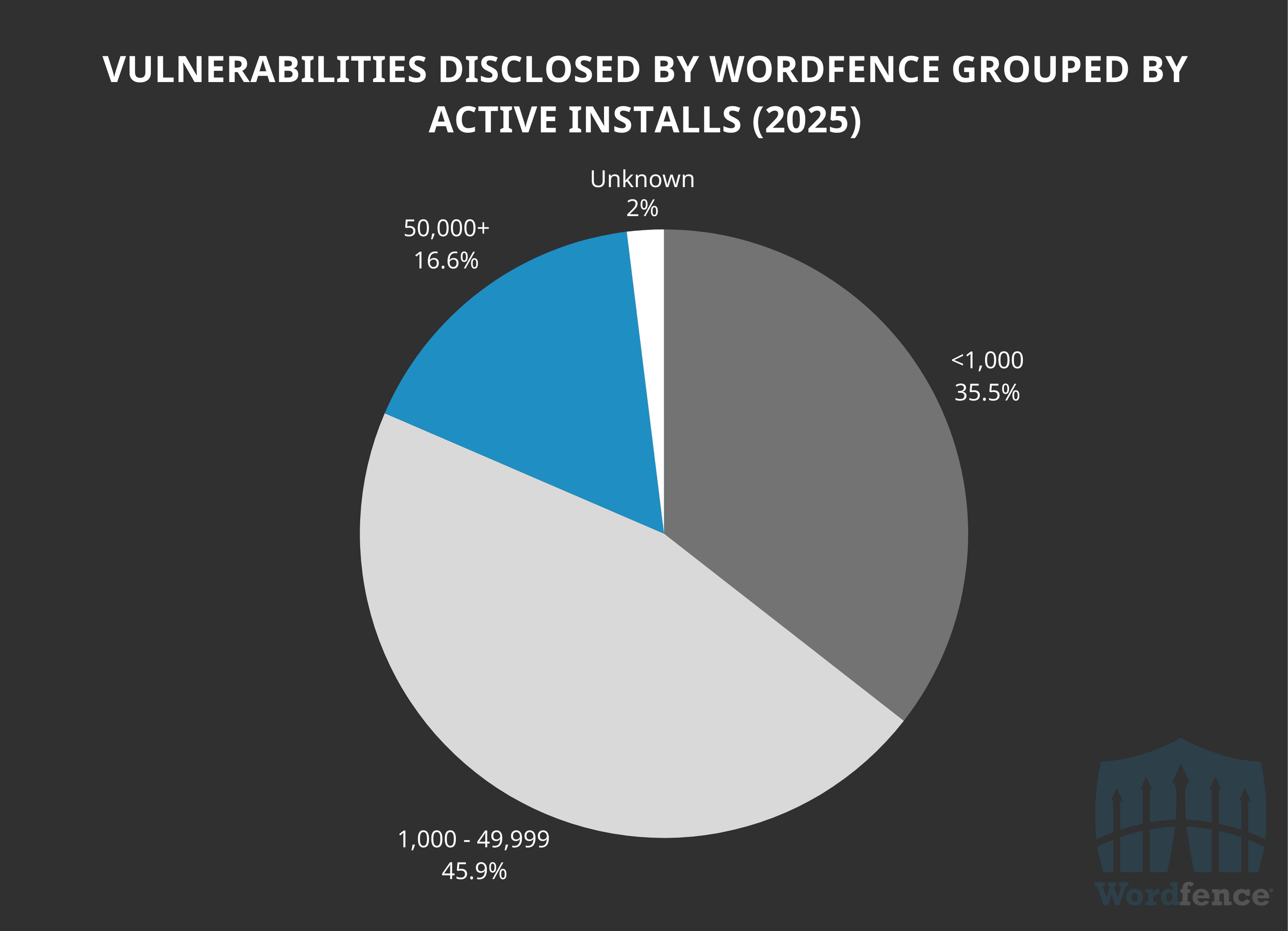
Wordfence shows quite the opposite, with a well distributed percentage across install counts. Only 35.5% of wordfence’s vulnerability disclosures so far this year are in software with fewer than 1,000 active installations.
Wordfence Leads on Directing Researcher Attention to More Impactful Install Bases
As just highlighted, an interesting trend in 2025 is that the majority of vulnerabilities being disclosed by other WordPress CNAs is in software with fewer than 1,000 active installations. This means that instead of attracting higher quality, more impactful research, they’re doing quite the opposite and attracting more low impact research that is also of low risk.
Around 35.5% of our vulnerabilities disclosed this year are in software with fewer than 1,000 active installations. This is higher than we prefer, but it’s due to our end of year initiative from 2024, where we temporarily expanded our Bug Bounty scope to include plugins with 50-999 active installations that were updated in the last 2 years. This initiative aimed to educate up and coming developers and provide new WordPress researchers a wider hunting ground to develop their skills.
We expect this percentage to decrease as researchers submit more vulnerabilities in high install count software within our standard program scope.
We believe that it is still beneficial to discover and responsibly disclose vulnerabilities in software with smaller active installation counts, however, we don’t believe that it should be what defines an industry leading vulnerability database provider.
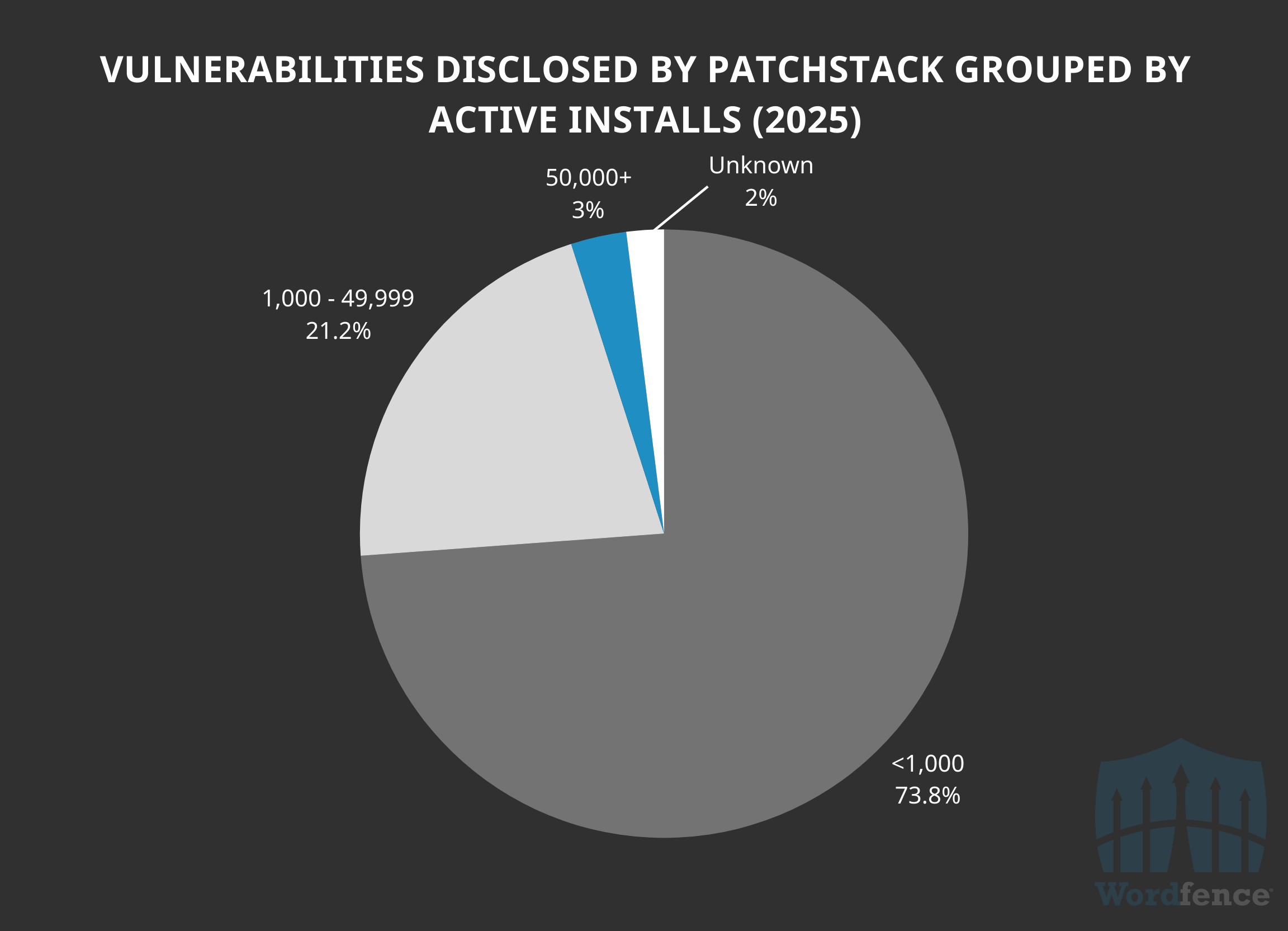
In contrast, over 73.8% of the 3,016 vulnerabilities (by software record affected) Patchstack has disclosed is in software that affects fewer than 1,000 active installations. This means that the vast majority of vulnerabilities disclosed by Patchstack have minimal impact on real-world sites or the WordPress ecosystem. Out of those 2,227 vulnerability reports in software with fewer than 1,000 active installations, 902 are for software with fewer than 100 active installations. That is 40.5% of all vulnerabilities disclosed by Patchstack with less than 1,000 active installations, and 30% of all their vulnerabilities disclosed so far this year.
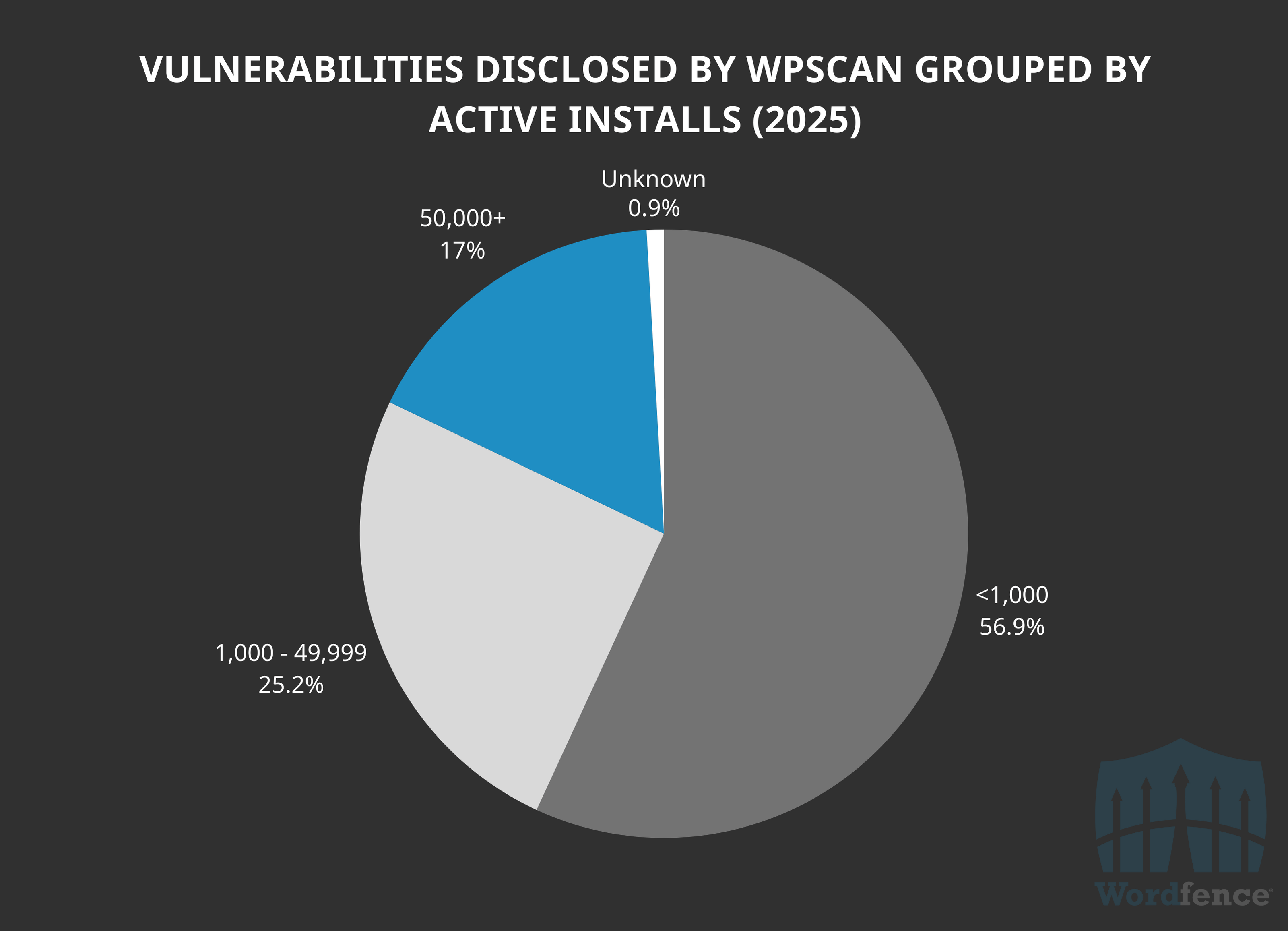
WPScan is in a similar position, with 56.9% of all of their 218 vulnerabilities published in software with less than 1,000 active installs. Out of those 124 vulnerabilities, 86 or 69.4%, of the total are in software with less than 100 active installations. This means 39.4% of all vulnerabilities published by WPScan are in software with fewer than 100 active installations.
Ultimately, this means that relying on a vulnerability provider other than Wordfence as a vulnerability intelligence data source means you’ll be the first to know about issues that likely won’t affect the majority of your users, while paying for a delay on the source of the most impactful vulnerabilities.
By utilizing Wordfence’s completely free Wordfence Intelligence API or Webhook integration, or Wordfence’s WAF, you’ll be the first to know and the first to be protected against vulnerabilities that will likely impact the sites you protect.
Wordfence: The Leader in High Threat Vulnerability Intelligence
Another way we measure the quality of our vulnerability intelligence is the types of vulnerabilities we attract to our Bug Bounty Program and are the first to disclose in our vulnerability database.
We put a strong emphasis on awarding the highest bounties for unauthenticated vulnerabilities and low-level authenticated vulnerabilities since these are the most likely to be targeted by attackers, and we have a wide scope that awards the best bounties for vulnerabilities likely to lead to a full site compromise. Wordfence tracks billions of malicious exploit attempts every year, so we know exactly what vulnerabilities attackers are targeting.
In other words, we strive to remediate the most high threat vulnerabilities that will likely be targeted by attackers.
We generally define ‘high threat’ vulnerabilities as anything that can lead to a complete site compromise with relatively low effort and can easily be replicated across environments. This means they will be a prime and likely target for attackers targeting WordPress.
In addition, many of these vulnerability types often require custom WordPress firewall rules for adequate protection because they won’t be caught by standard or generic WAF rules that cover more basic vulnerabilities like Cross-Site Scripting, SQL injection, and more. Ensuring we attract the most of these vulnerabilities through our program, ensures we’re the first to provide protection through the Wordfence firewall before the vulnerability is even disclosed.
Though our Bug Bounty Program, we define high threat vulnerabilities as any of the following that can be exploited by unauthenticated or low-level authenticated users:
- Arbitrary PHP File Upload or Read
- Arbitrary PHP File Deletion
- Arbitrary Options Update
- Remote Code Execution
- Authentication Bypass to Admin
- Privilege Escalation to Admin
These are in scope for all of our researchers as long as the software has 25 active installations. While we consider software with lower than 1,000 active installs relatively low impact, we still consider high threat issues to pose a risk and therefore like to reward the researchers for discovering these types of vulnerabilities so we can work to get the vulnerability patched, and educate the developers to prevent these vulnerabilities in the future as their install base grows. The bounties we award at this small install count range is substantially lower compared to something in a high install range so we still encourage more impactful research over low impact research, even when it’s a high threat vulnerability type.
Why do we measure the quality of vulnerability intelligence based on potential threat?
Because not all vulnerabilities are created equal. High threat vulnerabilities, like those that enable full site compromise with little or no authentication, are the ones attackers actively seek out. They’re easy to weaponize, hard to detect, and can cause serious damage fast.
By prioritizing the remediation, protection, and detection of these types of threats, we’re focusing on the vulnerabilities that matter most, the ones that are not only exploitable, but likely to be exploited. This makes our intelligence not just informative, but truly actionable.
At Wordfence, our emphasis on high-threat vulnerabilities ensures you’re protected where it counts: against the most dangerous vulnerabilities, before attackers can take advantage of them.
Wordfence Disclosed the Most Impactful High Threat Vulnerabilities in 2024
Last year, these vulnerabilities were in-scope for all researchers participating in our Bug Bounty Program as long as the software had 1,000 active installations. It’s worth noting that at the start of 2024 these vulnerability types were only in-scope for 1337 researchers (i.e. researchers with a proven track record and dedication to quality research) in the 1,000 – 50,000 range, however, we expanded this scope to all researchers in July of 2024 which directed more research of this kind our way half way into the year.
This year we updated our program scope so that any high threat vulnerability in software with at least 25 active installs will be in-scope for all researchers so we can try to remediate as many of these vulnerabilities from the repository as possible.
In 2024, there were 434 high threat vulnerabilities, as defined by the Bug Bounty Program, and Wordfence was responsible for coordinating and remediating 45.2% of the total.
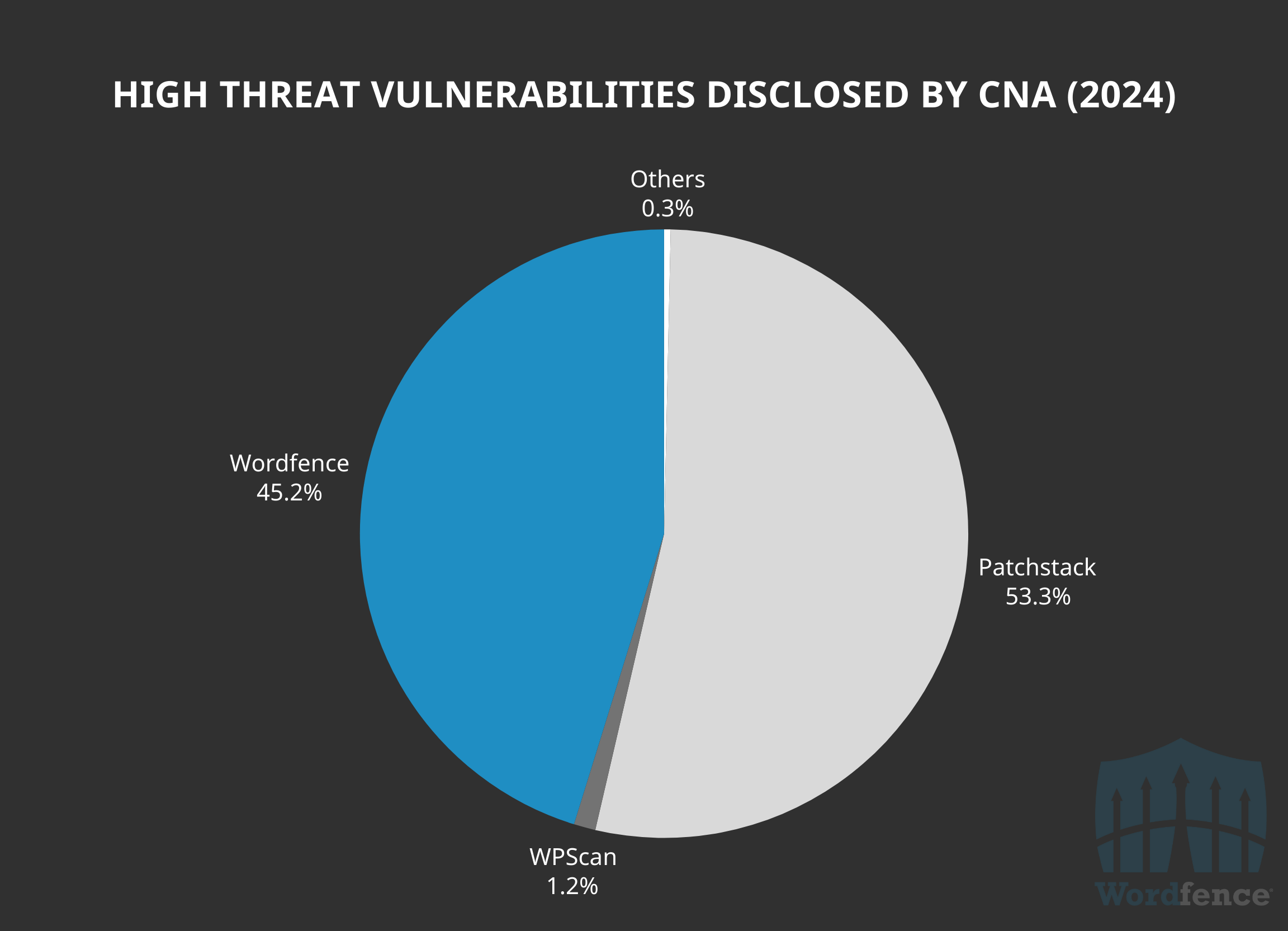
In 2024, there were only 36 high threat vulnerabilities in software with at least 50,000 active installations, and Wordfence was responsible for remediating 66.7% of these. This demonstrates our ability to get first look and provide first protection against vulnerabilities that affect the most sites and pose the greatest risk before the vulnerability is even patched or made public, ensuring Wordfence users are protected first where it matters most.
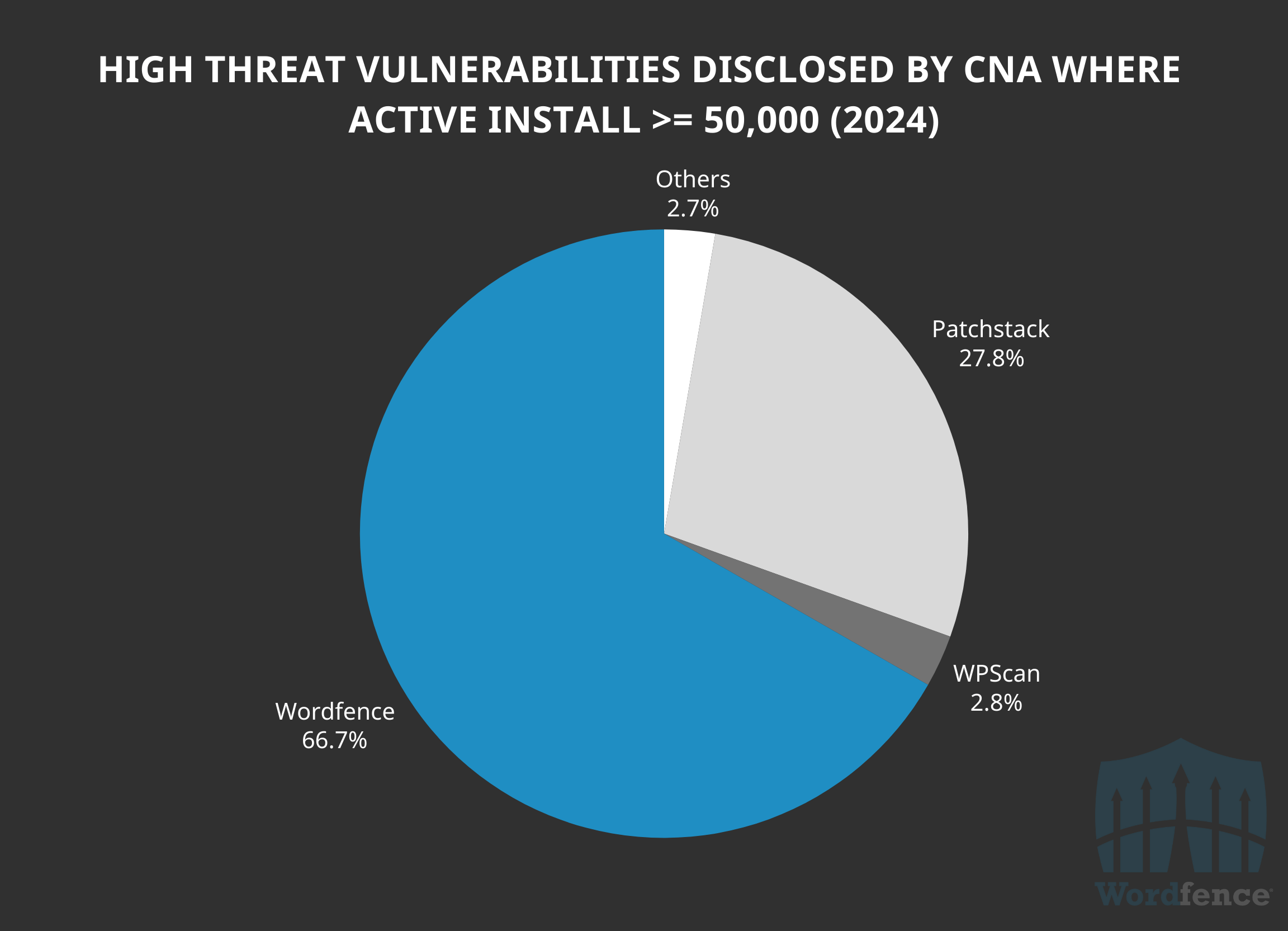
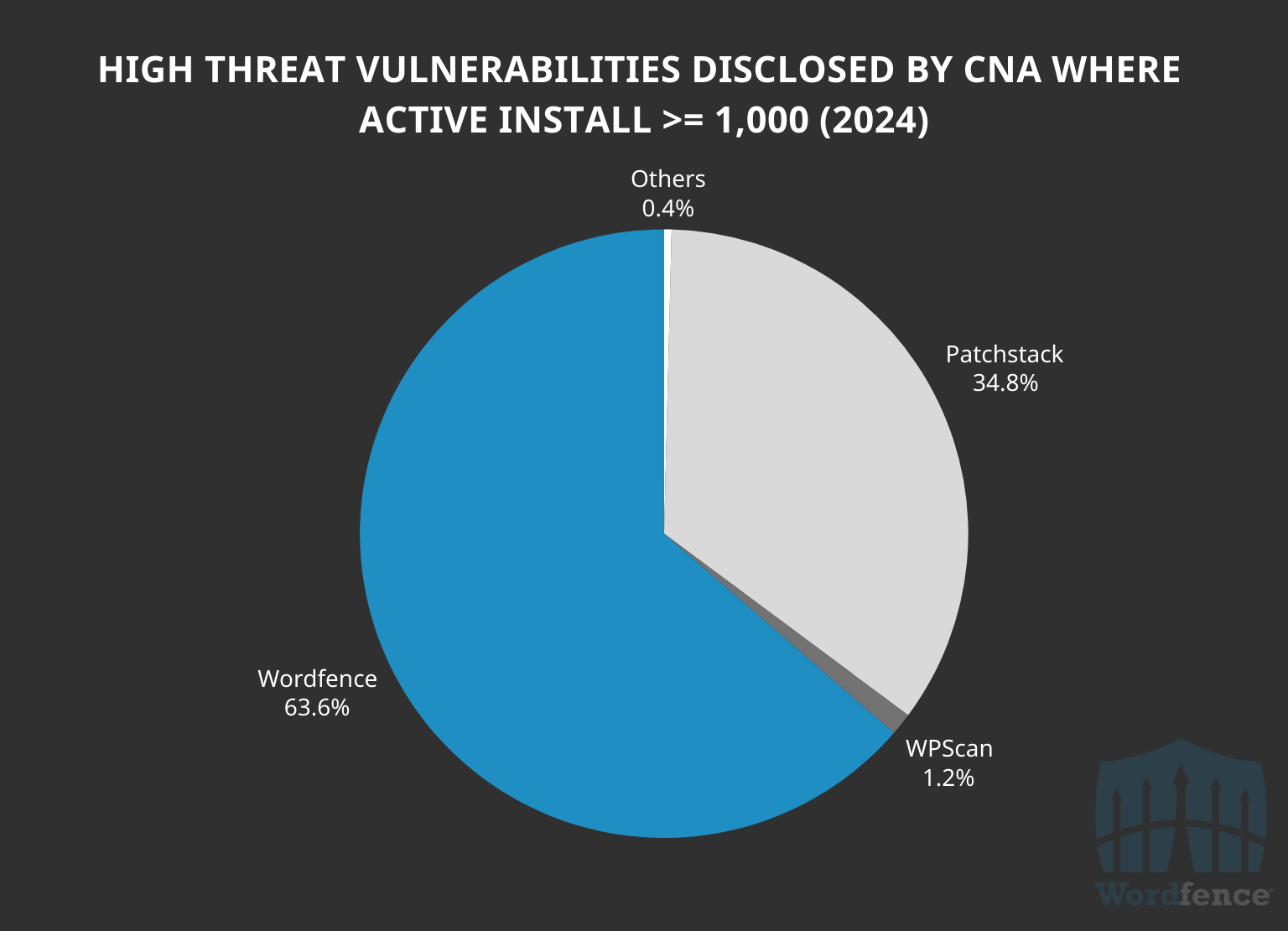
In addition, there were 253 vulnerabilities published in software with at least 1,000 active installations and Wordfence was responsible for 63.6% of these. This again highlights how we dominate on impact, and more specifically impact on high threat vulnerabilities.
Other WordPress CNA’s data is quite the opposite. Instead of dominating at high impact high threat vulnerabilities, they dominate in low impact high threat vulnerabilities in comparison. One of the other WordPress CNAs accounted for the majority of high threat vulnerabilities in software with less than 1,000 active installs, with 74.9% of the 187 vulnerabilities published in this range.
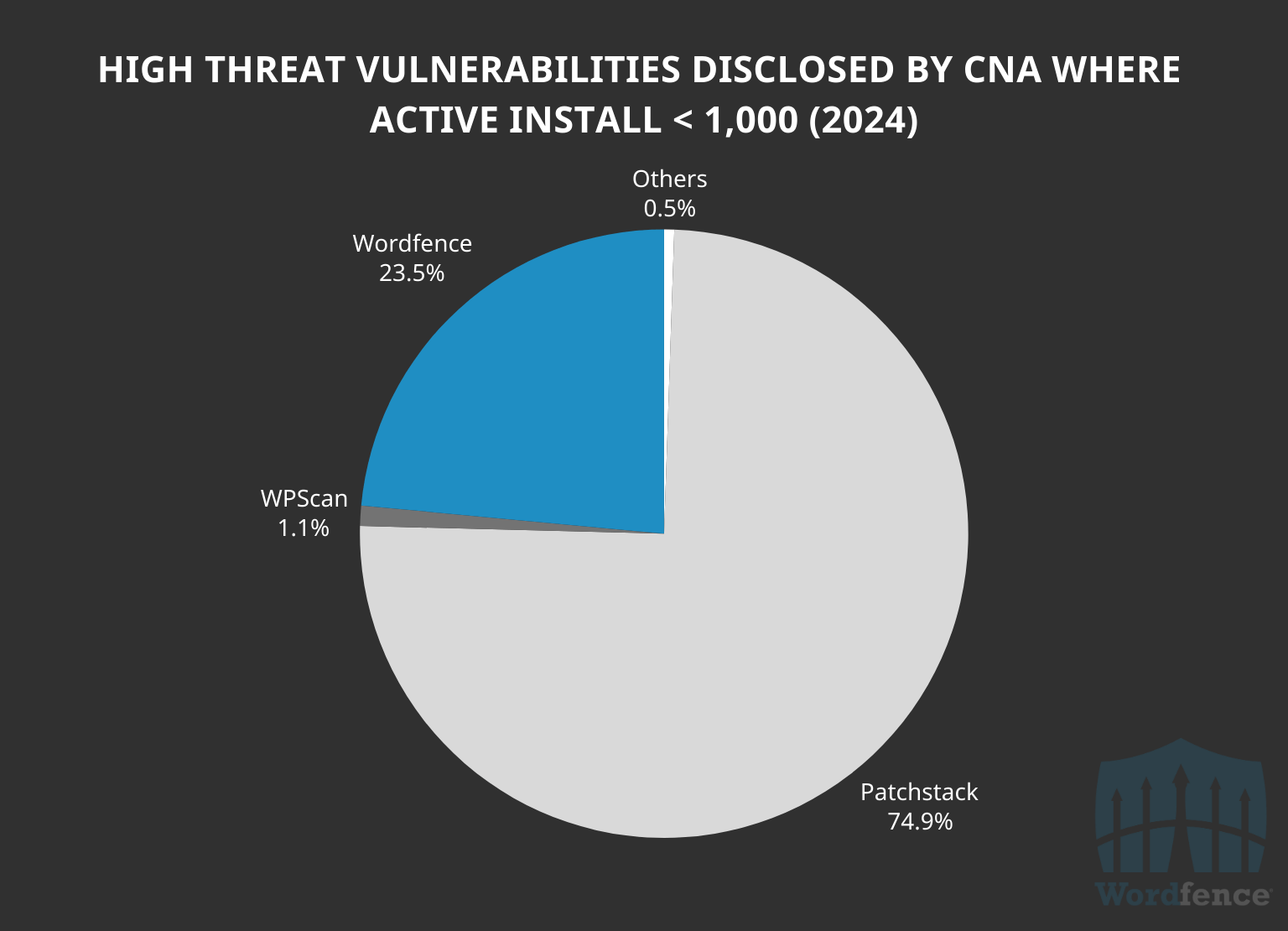
More interestingly, out of those plugins with fewer than 1,000 active installations by the CNA, 73% of them, or 102, were in software with fewer than 100 active installations. In other words, 44% of all high threat vulnerabilities disclosed by this CNA in 2024 was in software with fewer than 100 active installs, meaning they’ll likely never be a target for attackers nor will they affect many real-world sites.
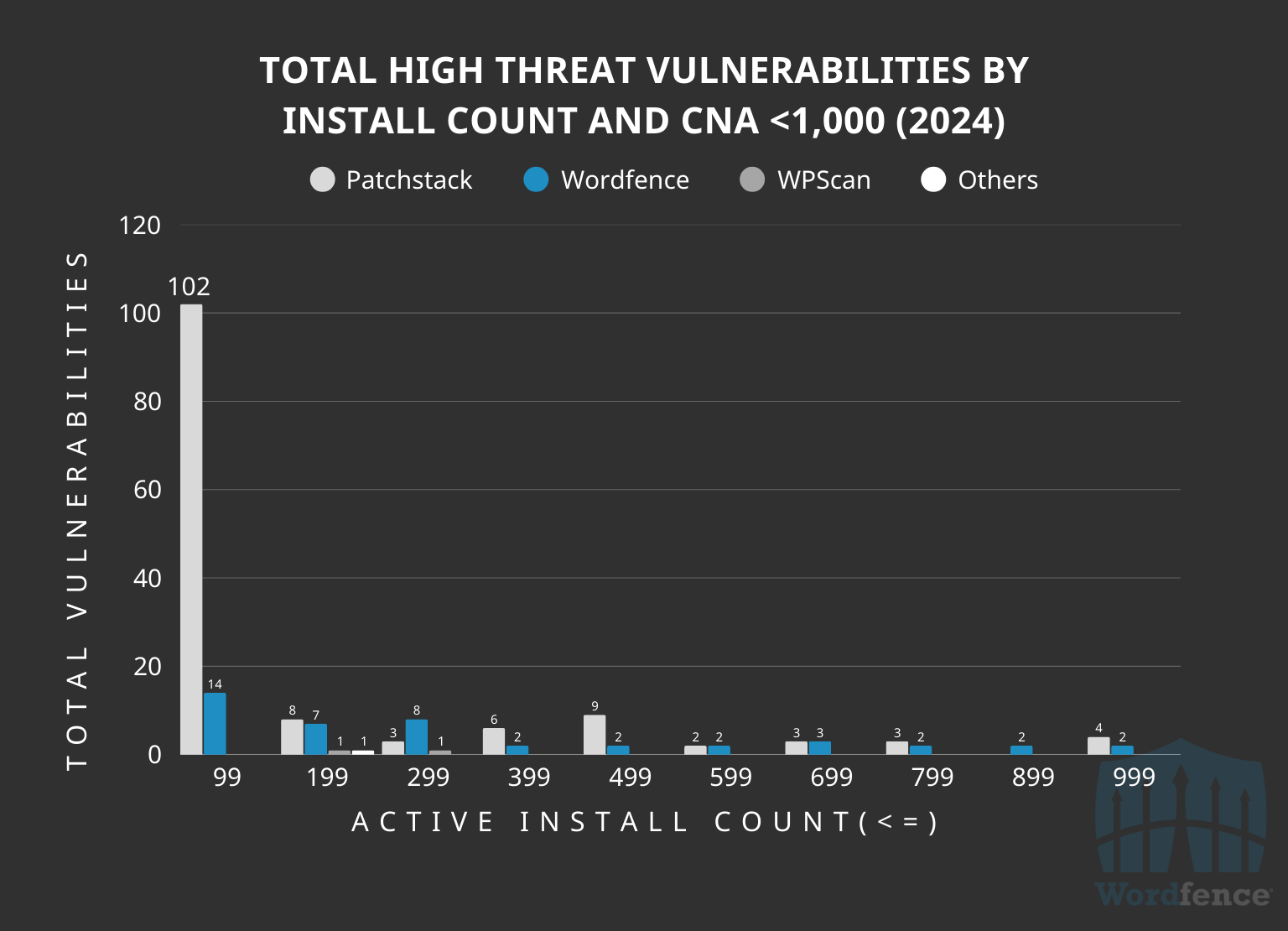
Conversely, only 21.4% of the high threat vulnerabilities Wordfence processed and remediated were in software with fewer than 1,000 active installations and only 31.8% of those were in software with less than 100 active installations.

In other words, only 6.8% of all high threat vulnerabilities disclosed by us was in software with fewer than 100 active installs. A stark comparison to the 44% as seen by one of the other CNAs, highlighting the quality of our vulnerability intelligence based on impact and threat over other WordPress CNAs.
If we were to recreate the chart at the beginning, excluding anything with less than 100 active installations, there would be quite a difference. Wordfence becomes the clear leader on high threat vulnerabilities with a meaningful impact, disclosing 58.5% of all 299 high threat vulnerabilities in software with more than 100 active installations. The percentage of ownership only goes up for Wordfence as the number of active installations increases, a clear sign of leadership.

Despite disclosing a slightly smaller percentage of high threat vulnerabilities compared to other CNAs in 2024, our contributions and vulnerability intelligence clearly have a far greater positive impact on the ecosystem as a whole.
Wordfence Continues to Disclose the Most High Threat Vulnerabilities in 2025 while Continuing to Attract Impactful High Threat Issues
Wordfence is already outperforming 2024 moving into 2025. This year we are responsible for 66.5% of all 233 high threat vulnerabilities published thus far in 2025. This is exciting growth demonstrating how our Bug Bounty Program attracts the very best vulnerability research, and in turn makes it so we can provide the very best protection and detection for our users.
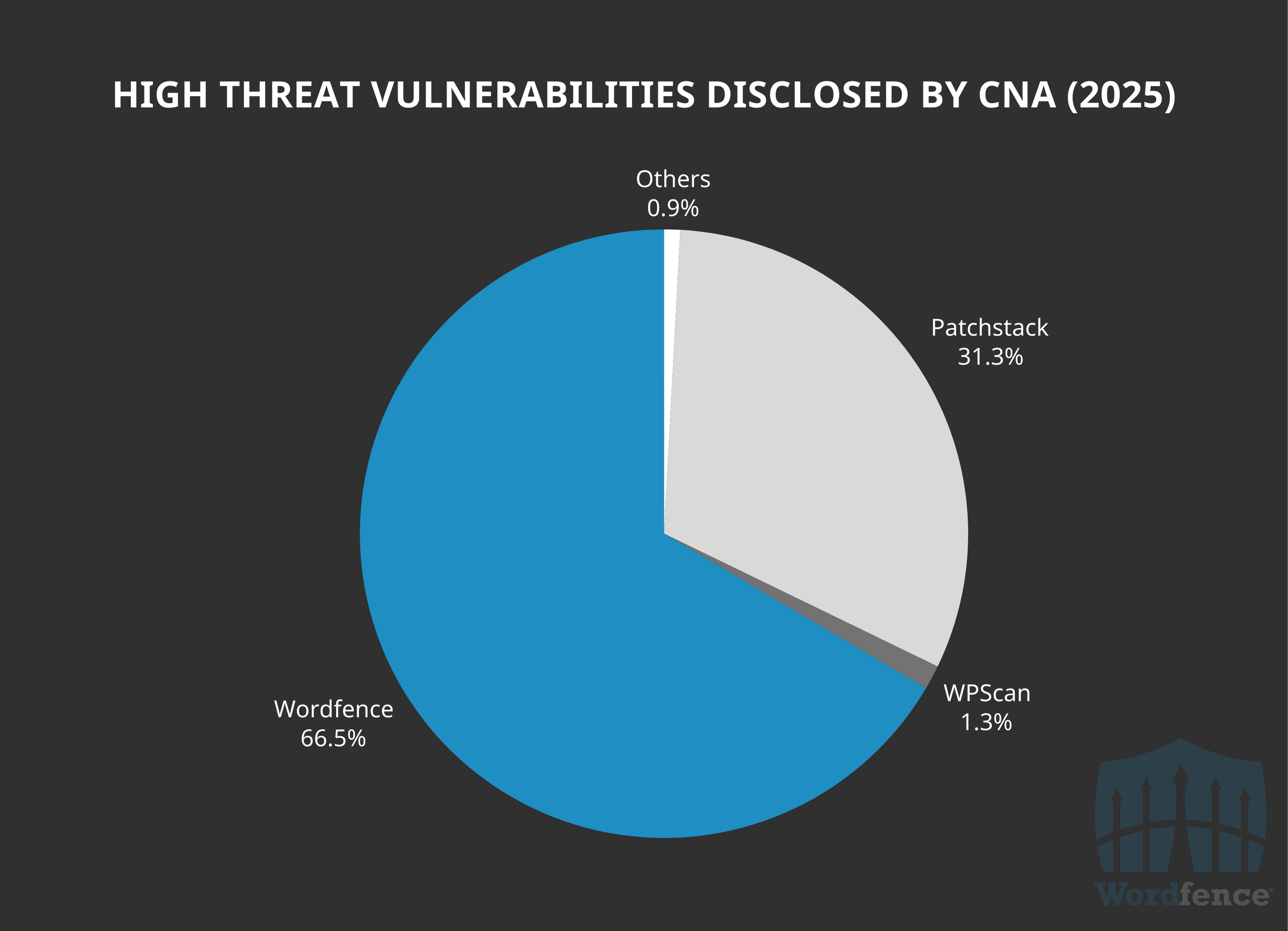
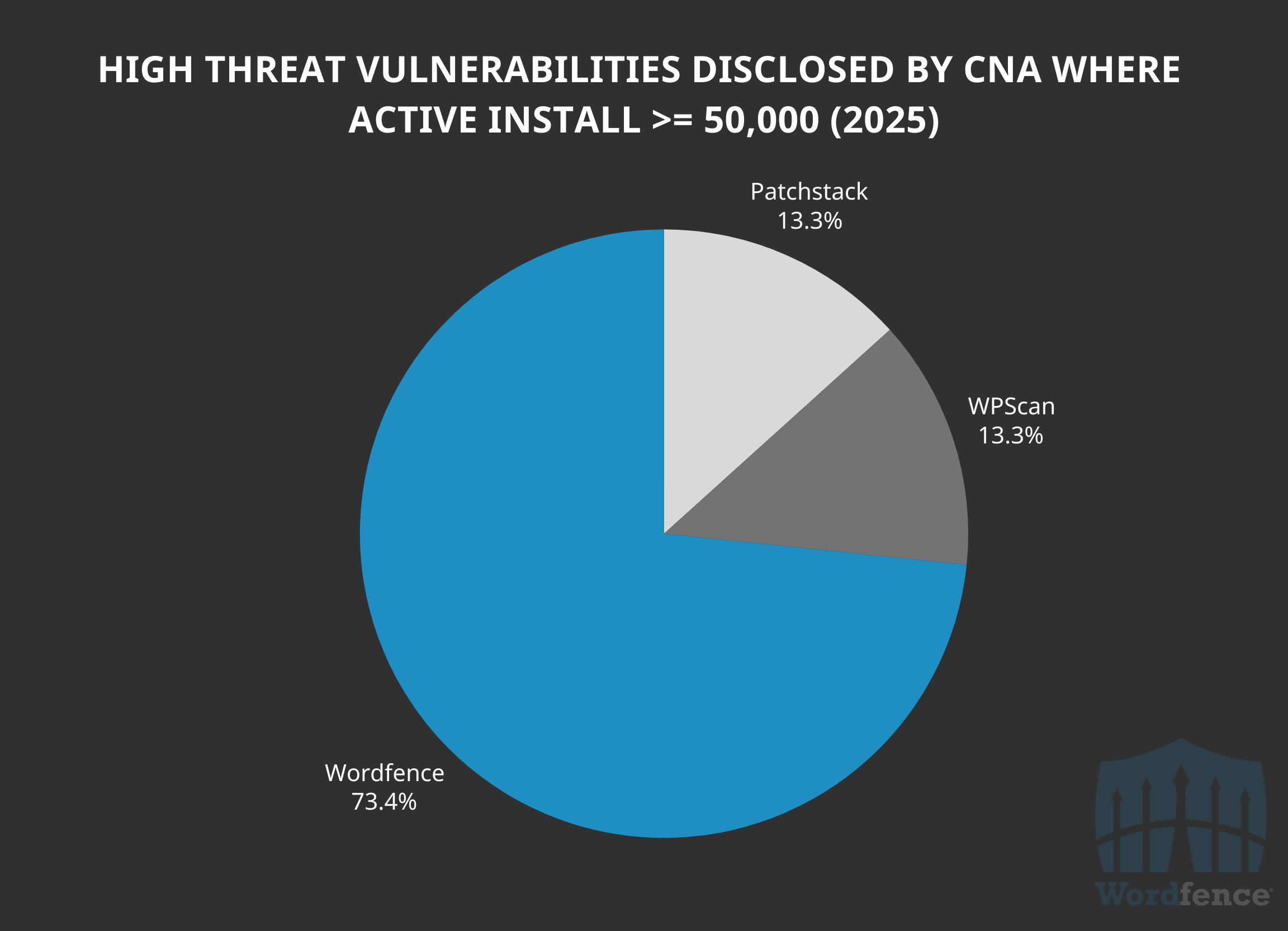
We also continue to dominate on high threat vulnerabilities with at least 50,000 active installations, having processed and remediated 73.4% of all 15 vulnerabilities in this range.
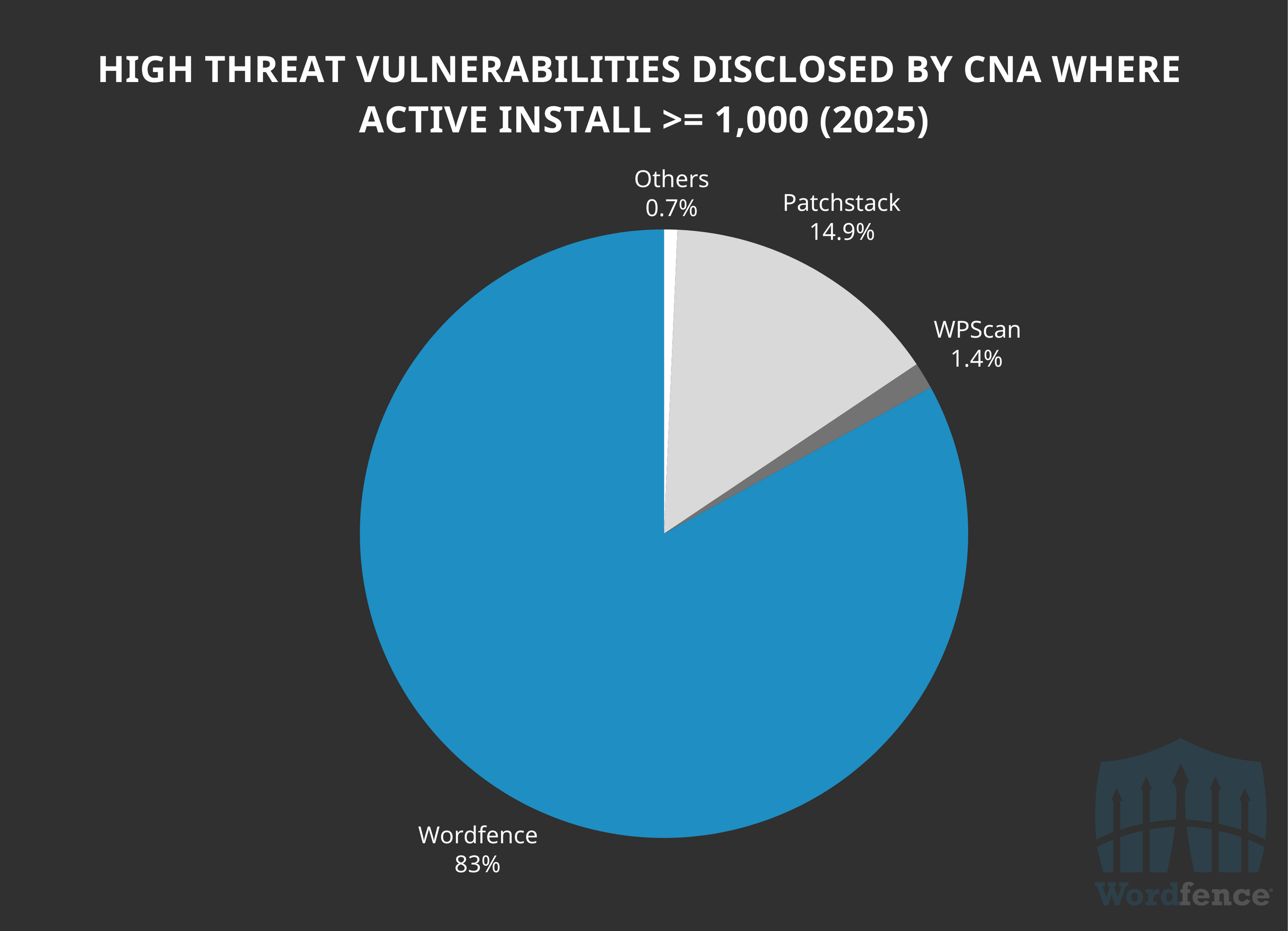
Our strength continues to grow for all high threat vulnerabilities with at least 1,000 active installations, with Wordfence having processed and remediated 83% of all 141 vulnerabilities in this range so far in 2025.
Patchstack continues to lead high threat vulnerabilities with fewer than 1,000 active installations accounting for 57.6% of the 92 vulnerabilities in this range, though we expect that to change over the year with our expanded Bug Bounty Scope. We aim to be the provider with the first look at all high threat issues, regardless of install count and expect to reach that goal this year. 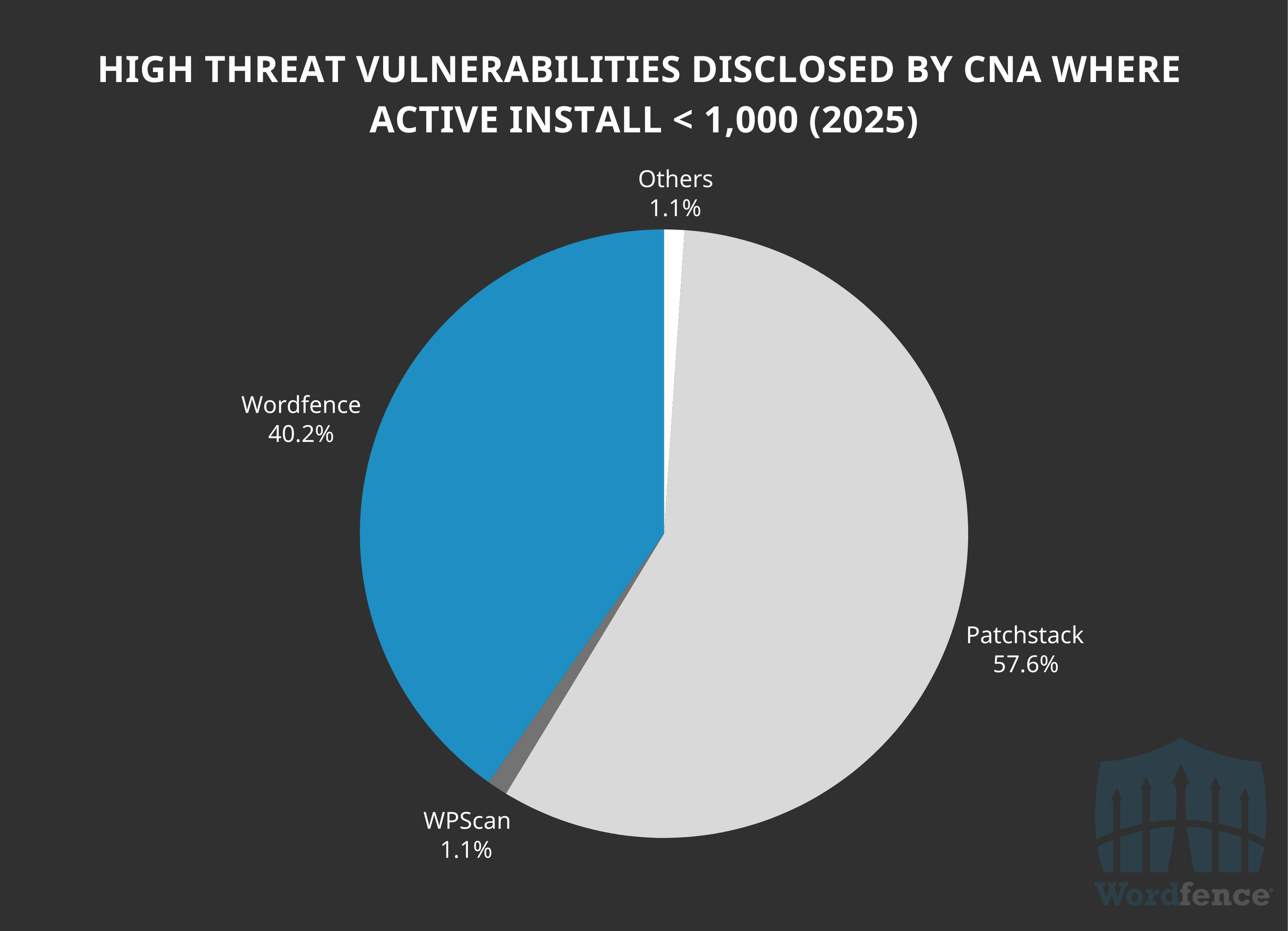
So far in 2025, only 23.9% of the 155 high threat vulnerabilities Wordfence was responsible for were in software with fewer than 1,000 active installs. In contrast, 71.6% of Patchstack’s 74 published vulnerabilities and 33% of WPScan’s 3 published vulnerabilities fell into this category.
We maintain the lowest percentage of low impact high threat vulnerabilities, while also maintaining the highest volume and highest impact of all high threat vulnerabilities. This is a clear indication how we excel at attracting the highest threat and highest impact vulnerabilities, and how we are a clear leader in vulnerability intelligence that matters most.
Wordfence: The Leader in Common and Dangerous Vulnerabilities
In 2025, Wordfence introduced a new category to our Bug Bounty Program scope called “Common and Dangerous” vulnerabilities. This category includes Stored Cross-Site Scripting and SQL Injection vulnerabilities that are exploitable by unauthenticated users or those with low-level permissions, such as subscribers. To be considered in-scope, the affected software must have at least 500 active installations.
These vulnerabilities are prevalent in the WordPress ecosystem due to the many ways user input is collected and handled. Despite their frequency, they remain significant threats. Attackers continue to target these types of vulnerabilities because, when successfully exploited, they can lead to serious consequences for the affected sites. This is precisely why we classify them as “Common and Dangerous.”
While generic web application firewall (WAF) rules often provide some level of protection against these vulnerabilities, our decision to include them in-scope is rooted in our commitment to security education and impact. This category gives researchers the opportunity to hone their skills on real-world vulnerabilities, while also encouraging developers, especially those newer to secure coding practice, to learn the importance of proper input handling, sanitization, and output escaping. This also ensures that we are the first to alert site owners when one of these vulnerabilities are present so they can quickly remediate the vulnerability on their sites.
By remediating more of these common and dangerous vulnerabilities, we not only reduce immediate risk across the ecosystem but also contribute to long-term security improvements by helping developers avoid similar issues as their software reaches larger audiences.
Wordfence Disclosed the Most Common and Dangerous Vulnerabilities in 2024
In 2024, Wordfence disclosed and processed 204 of the 444 vulnerabilities classified as “Common and Dangerous”, accounting for 46% of the total. This is more than other CNAs.
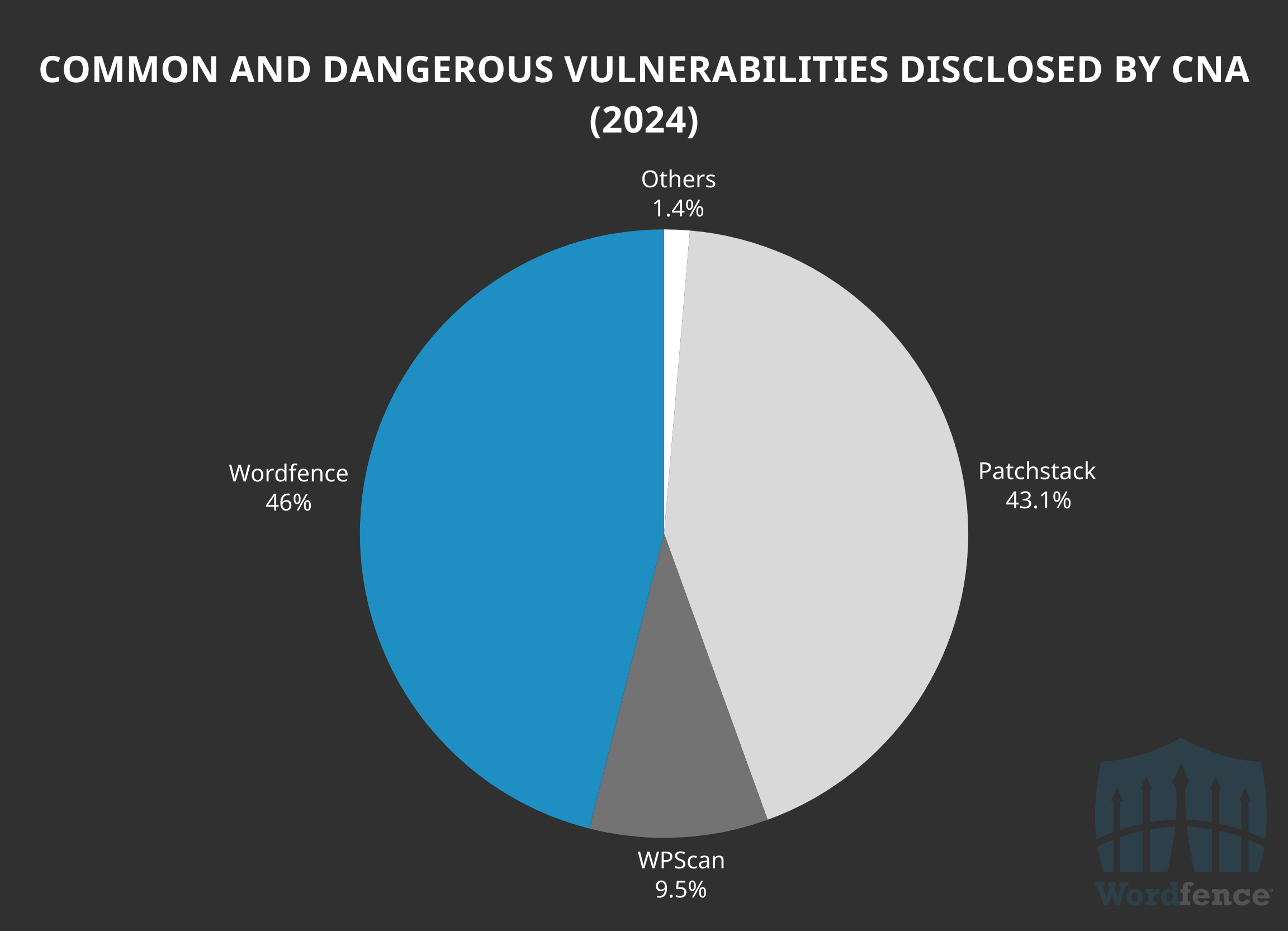
In a landslide, Wordfence assigned and disclosed 85.5% of all 76 common and dangerous vulnerabilities in software with at least 50,000 active installations, indicating leadership in high impact common and dangerous vulnerabilities.

Wordfence also assigned 57.9% of all 321 vulnerabilities with at least 1,000 active installations, further demonstrating our leadership on high impact vulnerabilities that matter most.
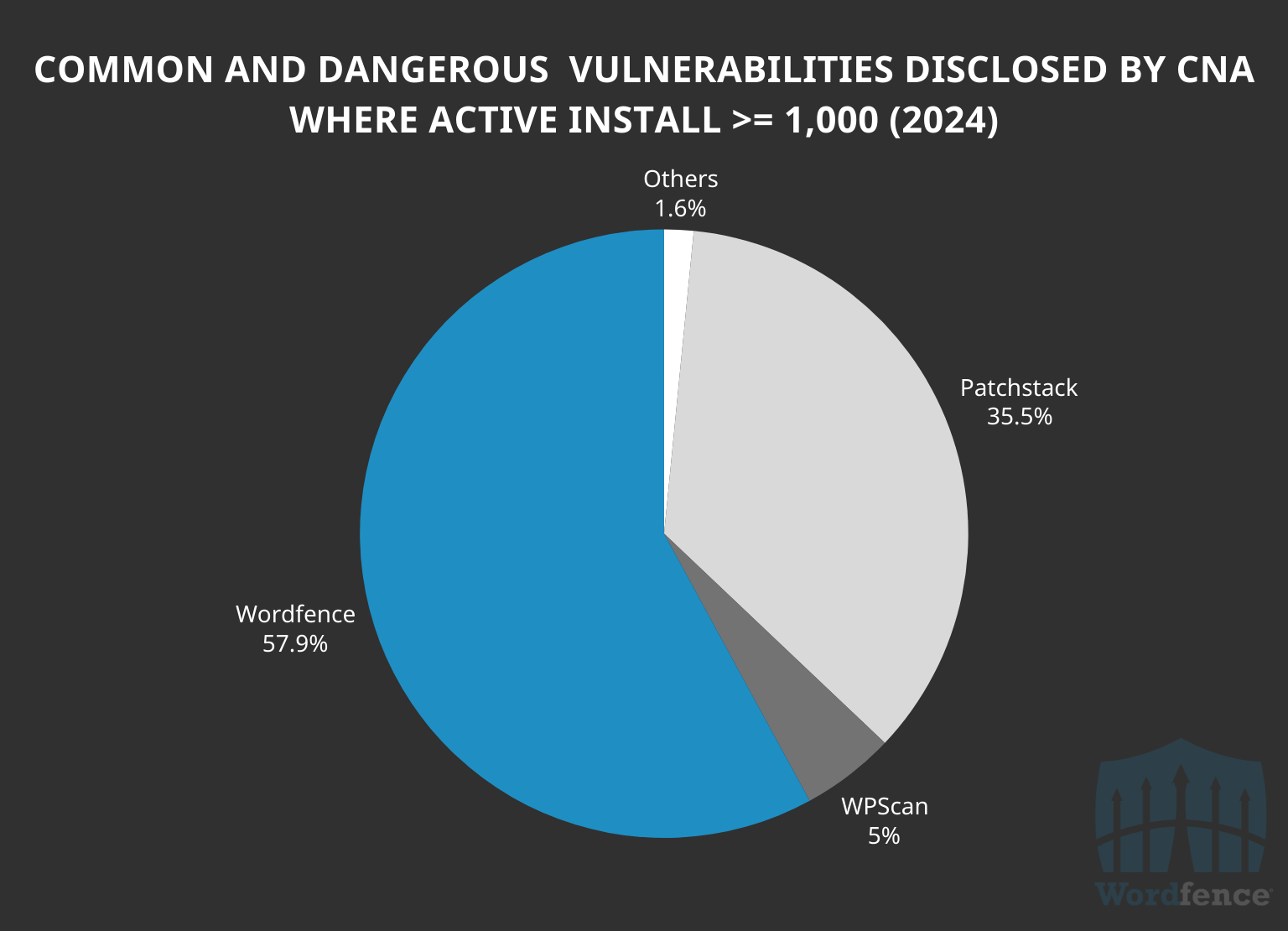
Just like with our overall vulnerabilities and High Threat vulnerabilities, Wordfence reported fewer of these vulnerabilities in software with less than 1,000 active installations, where Patchstack assigned the most CVEs in this range, with 64.4% of the total.

Similar to the high threat vulnerabilities, 56.8% of the 74 vulnerabilities Patchstack was responsible for in software with fewer than 1,000 active installations actually accounted for software with only 100 active installations or fewer. This means that around 22% of the total of all of Patchstack’s ‘Common and Dangerous’ vulnerability disclosures for 2024 were in software with less than 100 active installations. Conversely, only around 2% of Wordfence’s were.
This clearly highlights how Wordfence not only led in the number of ‘Common and Dangerous’ vulnerabilities disclosed in 2024, but also how we led in high impact and meaningful research that impacted the most sites.
Wordfence Disclosed the Most Impactful Common and Dangerous Vulnerabilities in 2025
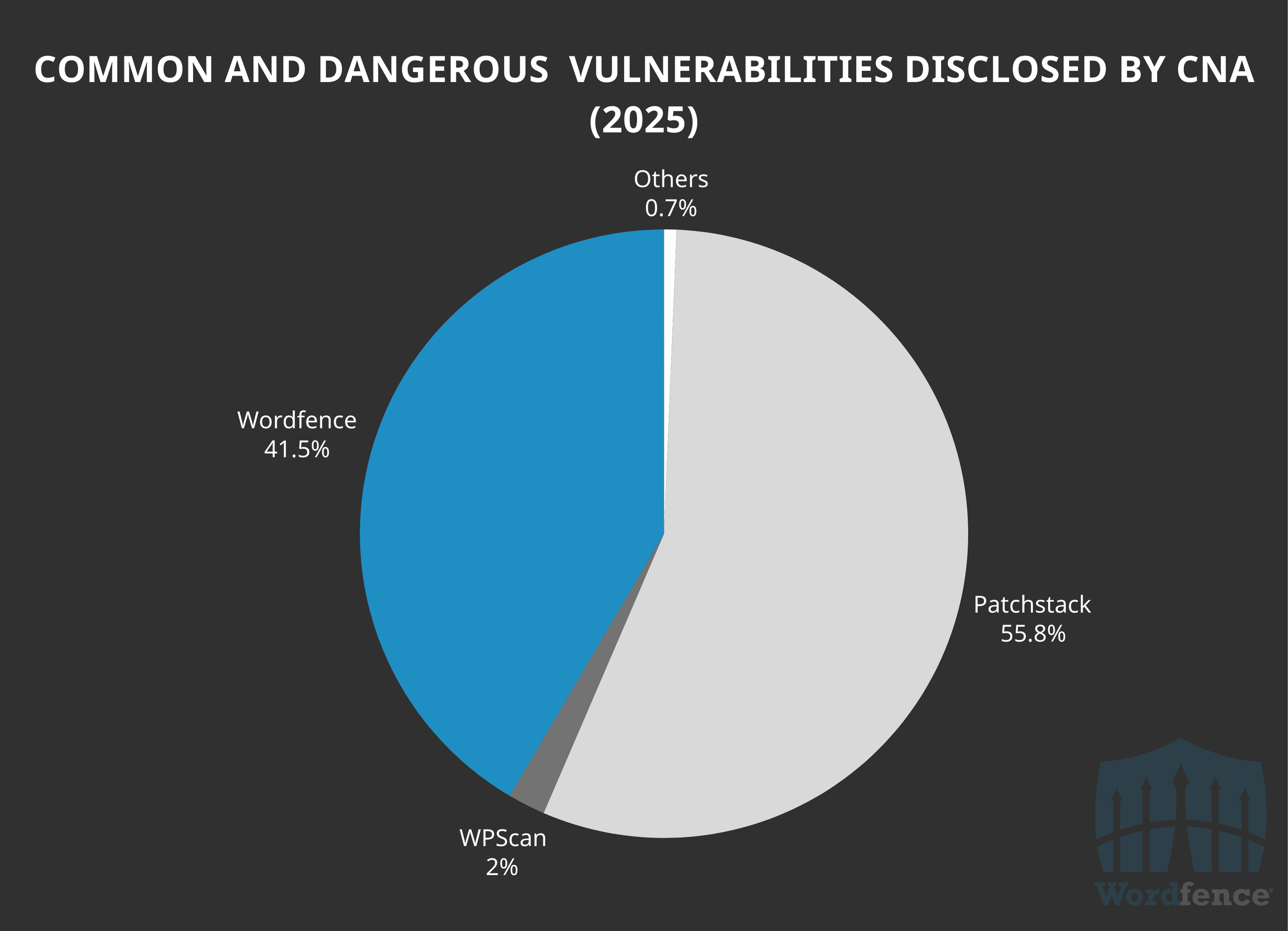
This year so far, Wordfence has not disclosed the most common and dangerous vulnerabilities, though we have disclosed the most impactful common and dangerous vulnerabilities.
Wordfence has processed and remediated 41.5% of the 301 common and dangerous vulnerabilities that have been published, just a slightly lower percentage than other WordPress CNAs.
However, we have disclosed 82.6% of the 23 vulnerabilities with at least 50,000 active installations in this category.
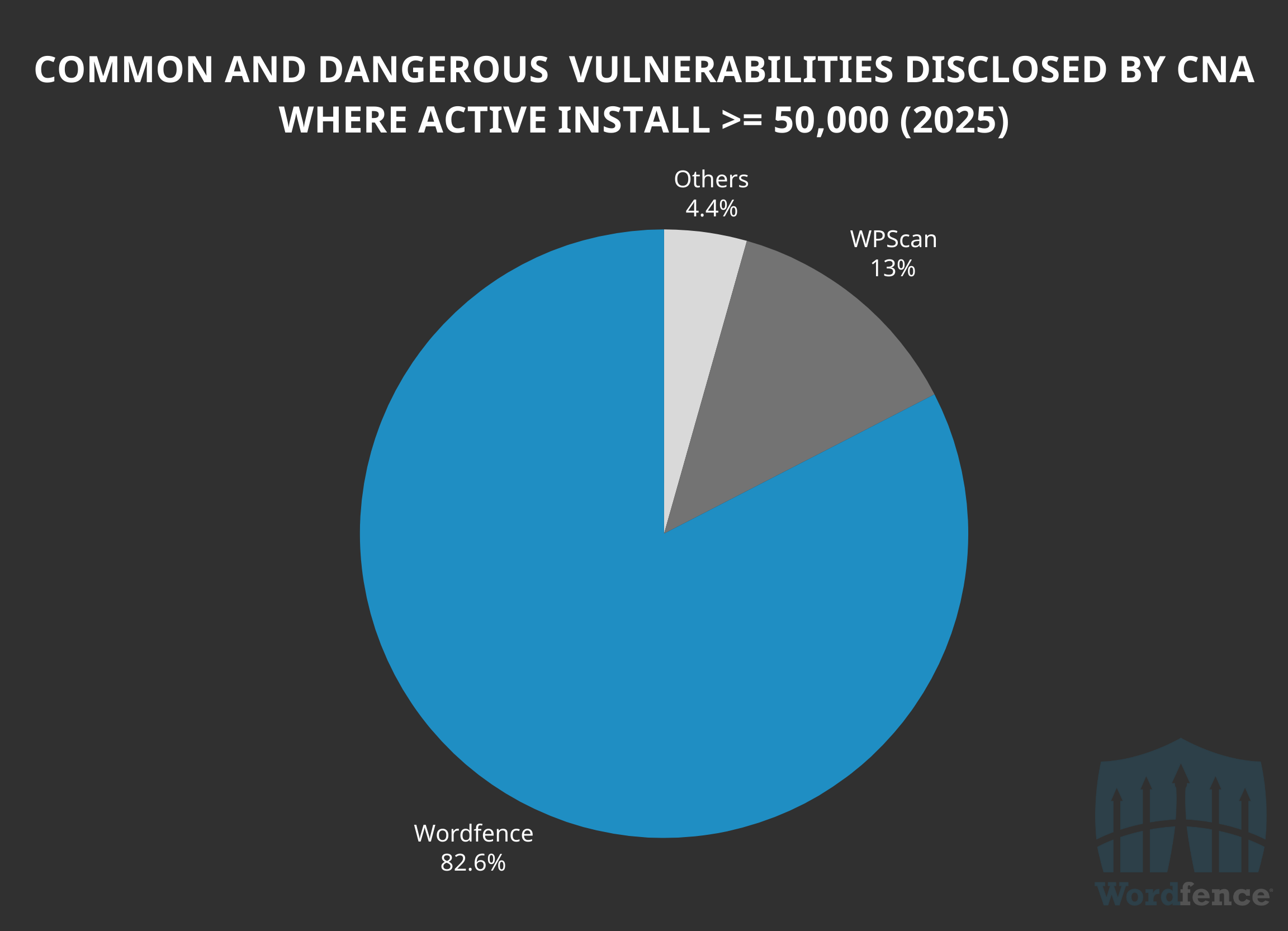
In addition, we’ve disclosed 75.4% of all the 126 common and dangerous vulnerabilities with at least 1,000 active installations. A clear indication again on how we exceed in attracting high impact and meaningful research.
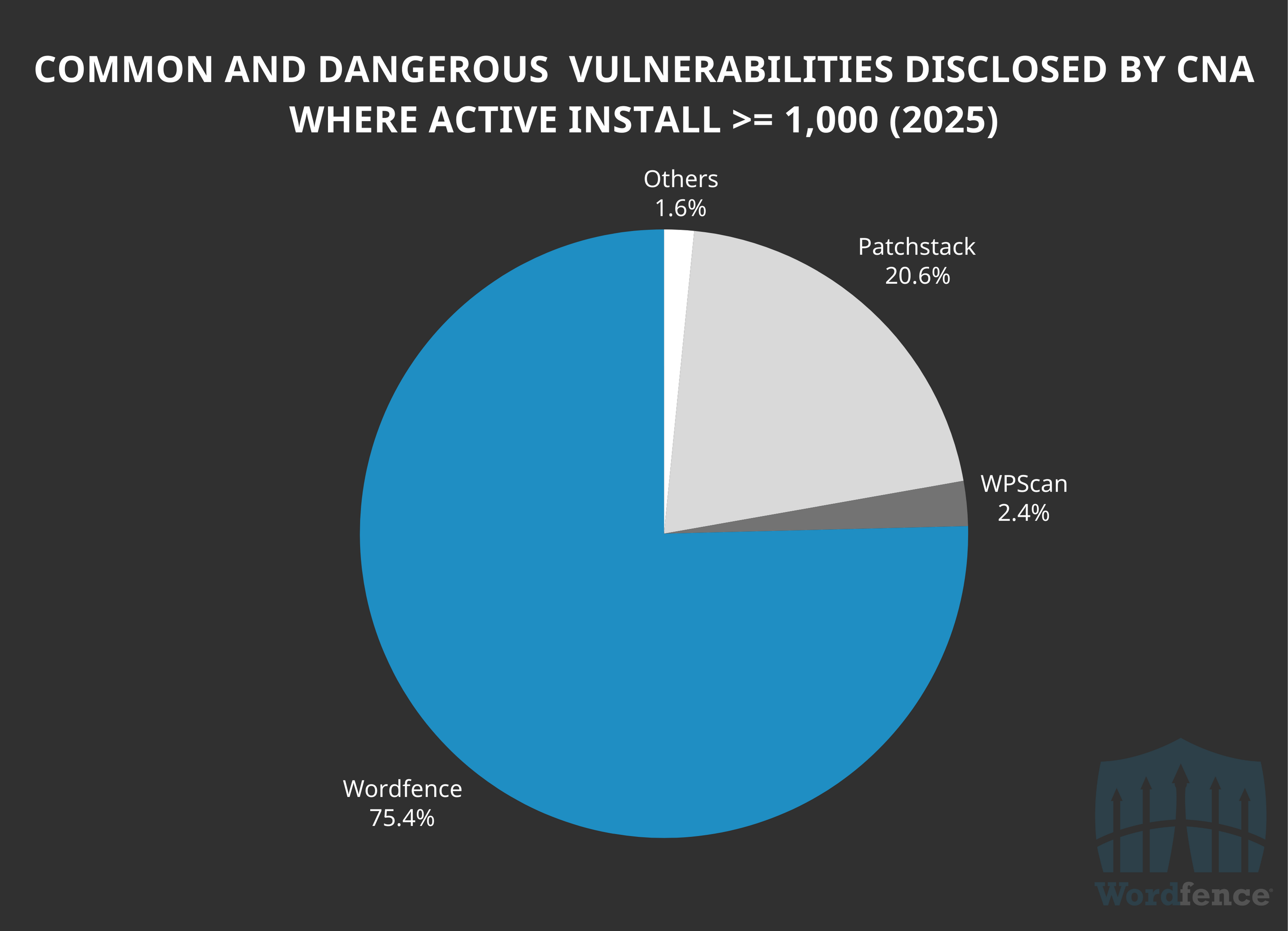
Yet again, we find that Patchstack excels at disclosing common and dangerous vulnerabilities in software with less than 1,000 active installations having accounted for 78.9% of the 180 vulnerabilities in this range.
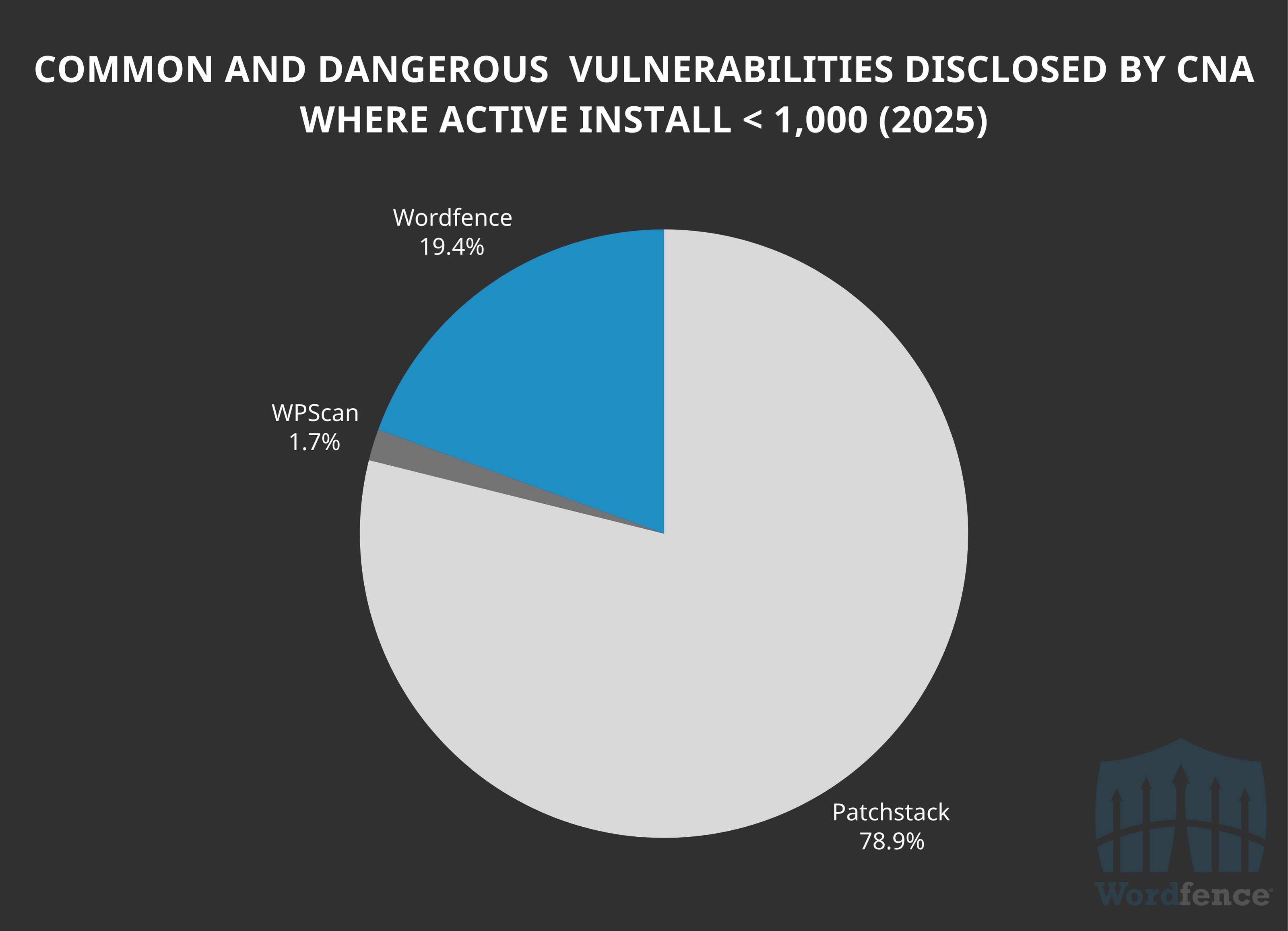
This means that 84.5% of all the 168 common and dangerous vulnerabilities that Patchstack has disclosed this year are in software with less than 1,000 active installations, conversely only 28% of the vulnerabilities disclosed by Wordfence have this minimum of an impact. While we are not leading in volume, we are clearly leading in impact.
Again, a fair amount (36.6%) of the vulnerabilities disclosed by Patchstack in software with under 1,000 active installations have 100 or fewer active installations. This equates to 31% of all common and dangerous vulnerabilities disclosed by Patchstack so far this year. Only 20% of Wordfence’s common and dangerous vulnerabilities have fewer than 100 active installations.
While we might not be leading on the volume of common and dangerous vulnerabilities disclosed so far this year, we are clearly leading on disclosing the ones that truly matter and impact the most WordPress sites. This is because our program does not cover common and dangerous vulnerabilities with under 500 active installations, leading to more impactful research that is ultimately added into our free vulnerability database.
Wordfence: The Leader in Responsible Disclosure Practices
Every time a new vulnerability gets discovered and reported to a Bug Bounty Program like the Wordfence Bug Bounty Program, it needs to go through the responsible disclosure process. This means that we need to find contact information for a vendor, reach out to them to confirm an appropriate security contact, and then send the vulnerability details to them. We do this while maintaining communication with the developer and guiding them through the patching process and reviewing the patch before or after it has been released.
Once the vulnerability has been patched, that is when we publicly disclose the issue and add it to our vulnerability database. In some cases, where a vendor is unresponsive, or we can not find contact information, we may escalate the vulnerability to the hosting repository such as WordPress.org so they can attempt to reach the vendor or take other actions as they see fit.
This is a crucial part of the vulnerability discovery process as it ensures site owners are getting patches to be able to remediate any vulnerabilities in the software installed on their site.
Why do we measure the quality of our vulnerability intelligence based on responsible disclosure?
Uncovering a vulnerability is only part of the equation—what happens next is just as important. A vendor focused solely on boosting their vulnerability count may fall short when it comes to the critical work of responsible disclosure. Last year during some of our promotions, we experienced the unsustainable level of work that is required when you’re processing and disclosing hundreds of vulnerabilities every month. It’s safe to assume that an organization processing that level of vulnerabilities every month is likely cutting corners to help speed up their processes and process more vulnerabilities.
At Wordfence, we don’t just collect vulnerabilities. We do our best to work directly with developers to get them patched. Generally, we take all steps to prevent publishing unpatched vulnerabilities in our database by taking multiple steps in the disclosure process before escalating an issue. We don’t want to just disclose more vulnerabilities, we want to remediate more vulnerabilities than other WordPress CNAs. This is also why we offer bonuses like our ‘Affects Multiple Functions’ bonus that incentives researchers to do more thorough code reviews to find all affected functions and maximize their earnings.
This process ensures that vulnerabilities are not only discovered, but meaningfully resolved, reducing risk for millions of WordPress users. Responsible disclosure isn’t a box to check, it’s a cornerstone of quality vulnerability intelligence. And it’s why we measure success not by volume, but by the real-world protection we help deliver through patched vulnerabilities.
Wordfence Disclosures Result in More Patches
One of the highlights of 2024 for Wordfence is that our disclosures resulted in the most patched vulnerabilities publicly disclosed, with 46.3% of all patched vulnerabilities being reported by Wordfence. We also had fewer unpatched vulnerabilities and closed software in 2024 compared to patched vulnerabilities.
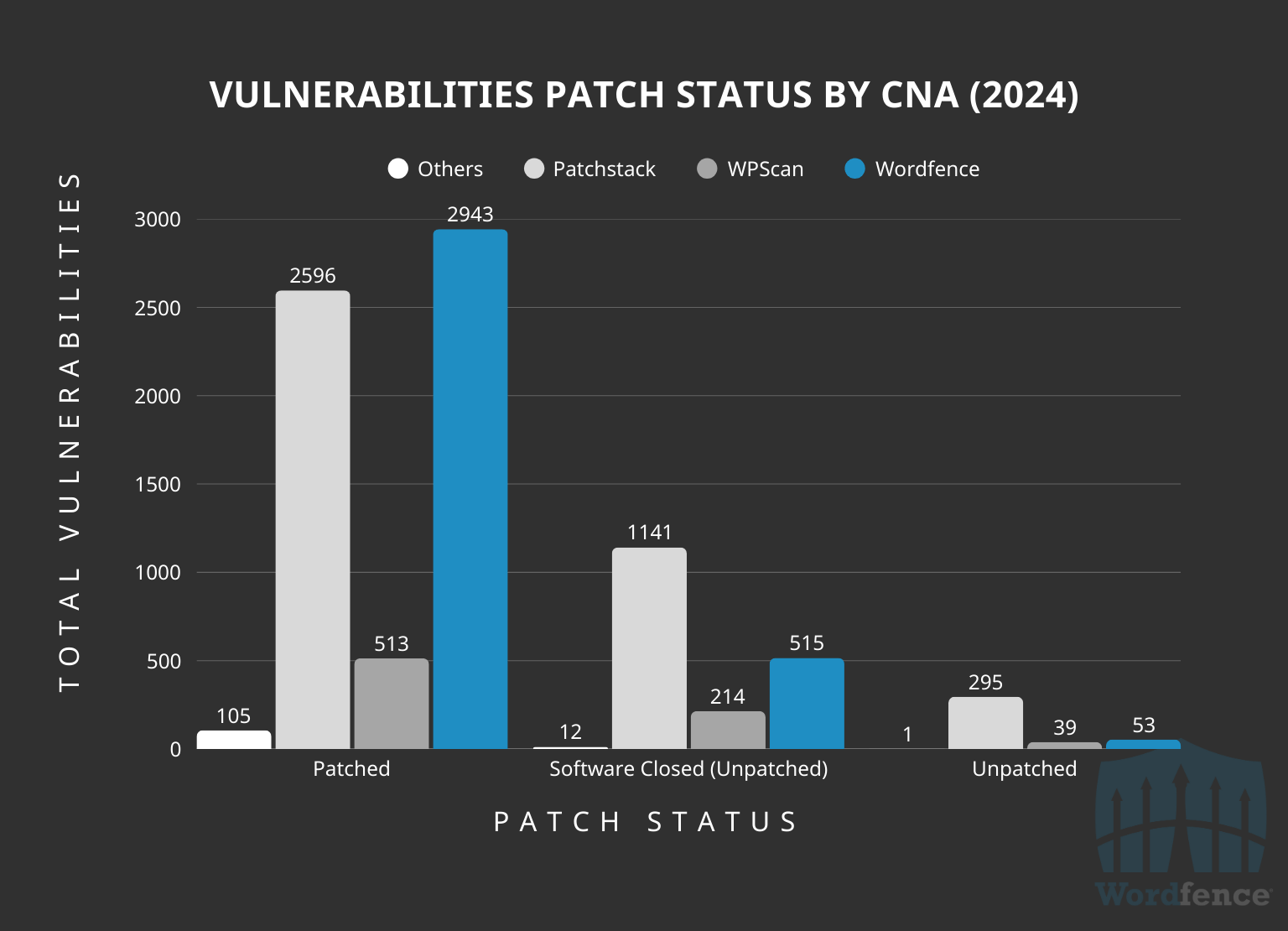
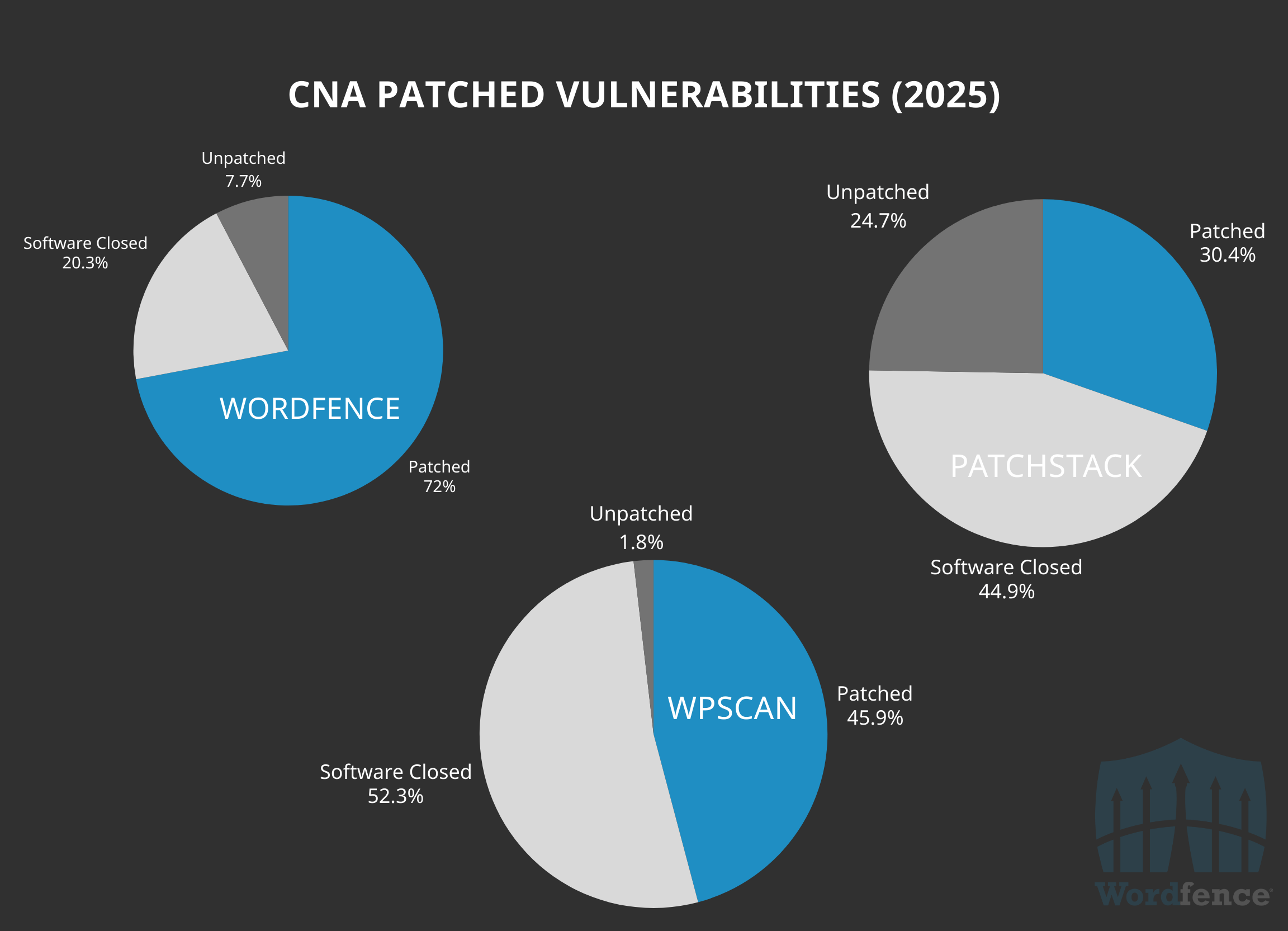
We also maintained the highest ratio of patched vulnerabilities to unpatched vulnerabilities in 2024. 83.8% of all 3,511 vulnerabilities (by software affected) we published are considered patched at the time of this writing. Conversely, only 64.4% of Patchstack’s 4,032 vulnerabilities are considered patched, and 67% of WPScan’s vulnerabilities are considered patched.
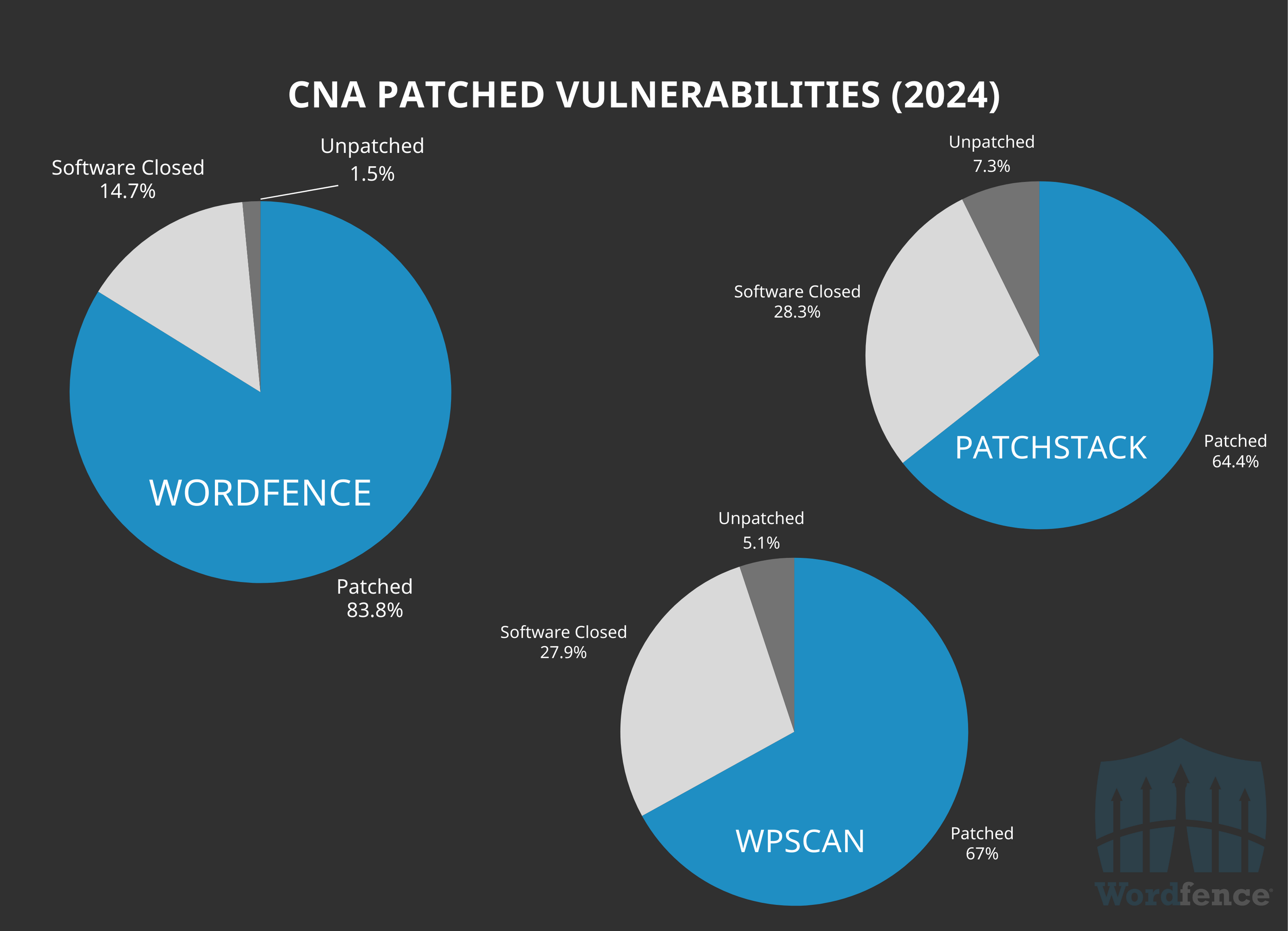
This trend continues into 2025, with Wordfence not only disclosing the most patched vulnerabilities, but also maintaining a substantially higher ratio of patched vulnerabilities to unpatched vulnerabilities. Despite having disclosed fewer vulnerabilities in 2025 so far, Wordfence has surpassed all other WordPress CNAs in the total number of patched vulnerabilities published. Please note this data is subject to change quickly as patches are released over the next several days and weeks post public disclosure.
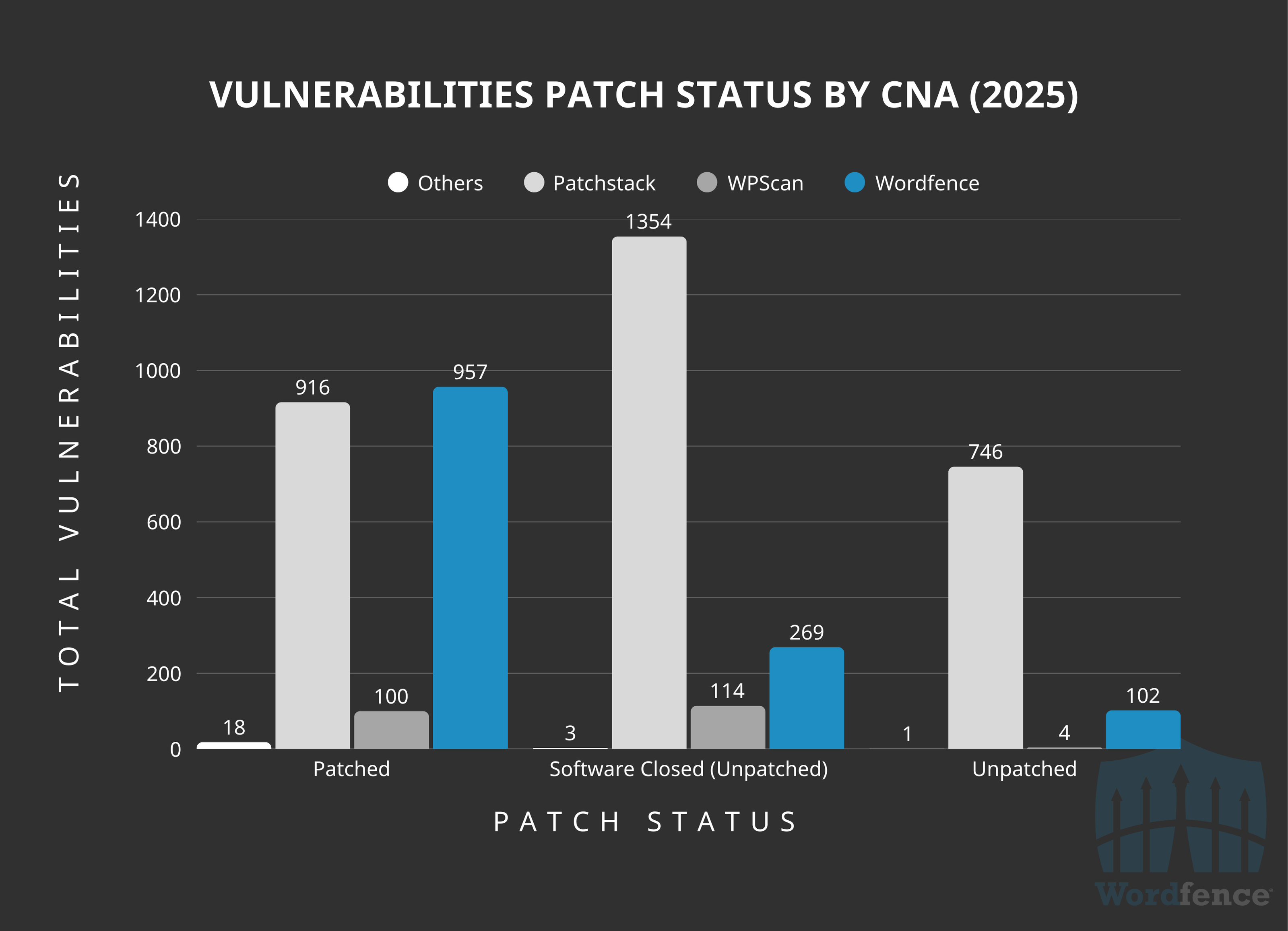
In addition we continue to maintain the highest patch rate among all other WordPress CNAs. Only around 28% of our vulnerabilities are currently still published as unpatched. This is a stark comparison to Patchstack who has 69.6% of all of their disclosed vulnerabilities still markedas unpatched, and WPScan who has 54.1% of all their vulnerabilities still published as unpatched.
This emphasizes a critical point: when it comes to the sensitive issue of vulnerabilities, trust should be placed in organizations that have a proven track record of effectively addressing and resolving these issues. These are the entities that prioritize the remediation of vulnerabilities to ensure the security and integrity of systems. Conversely, organizations that prioritize the disclosure of unpatched vulnerabilities, potentially exposing users and systems to risk, should not be the primary focus of trust.
The act of disclosing vulnerabilities without providing adequate time or solutions for patching can create unnecessary risks and potentially cause significant harm. Therefore, the emphasis should be on supporting and trusting organizations that prioritize responsible disclosure practices and demonstrate a commitment to swift and effective remediation. These organizations play a vital role in maintaining the overall security of the digital landscape by focusing on solutions rather than simply highlighting problems.
Wordfence: The Leader in Discouraging Low-Risk Vulnerability Research
Wordfence considers low-risk vulnerabilities to be anything that requires high-level authentication, like administrator or editor level access, in order to successfully exploit or anything that requires user interaction to exploit. That is because these vulnerabilities are not easy to successfully exploit due to the fact that social engineering or an initial compromise needs to occur before the vulnerability can be successfully exploited.
Considering most WordPress threat actors are looking for easy to automate exploits that provide immediate backdoor access or malicious redirects, these will not be a target for the majority of WordPress threat actors, making them incredibly low risk for the vast majority of site owners. In addition, exploitation of these types of vulnerabilities can easily be prevented by following the principle of least privilege, enforcing strong password policies, and not clicking on links/attachments or other data, unless 100% certain from the source. These types of vulnerabilities are often protected by standard and generic WAF rules as well.
When vulnerability disclosure programs prioritize quantity over quality and incentivize researchers primarily based on the number of vulnerabilities discovered, it fosters an environment where the focus shifts towards identifying numerous low-hanging fruit. These easily discoverable vulnerabilities may boost a researcher’s position on a leaderboard but often pose minimal risk to WordPress site owners. We like to foster an environment where searching for the low-hanging fruit is rewarded substantially less so focus shifts towards the highest risk issues that may require a little more time and digging.
At Wordfence, we believe that the true measure of effective vulnerability intelligence lies not in the quantity of disclosures but in the severity and impact of the identified vulnerabilities. We prioritize vulnerabilities that bypass high-level authentication or require minimal user interaction to exploit, as these pose a significantly greater risk to WordPress sites.
Our commitment to quality over quantity stems from the understanding that a deluge of low-risk and low-impact disclosures creates unnecessary noise and diverts attention away from critical threats. By focusing on high-impact vulnerabilities, we can provide WordPress site owners with actionable intelligence that enables them to proactively address significant security risks while not diverting valuable resources.
Furthermore, our approach encourages researchers to delve deeper into complex security issues and uncover vulnerabilities that require advanced skills and expertise to identify. This fosters a community of skilled security researchers who are dedicated to improving the overall security posture of the WordPress ecosystem.
By maintaining a quality-first approach to vulnerability intelligence, we strive to provide WordPress site owners with the most relevant and impactful security information, enabling them to make informed decisions and effectively protect their online assets.
Wordfence Disclosed Fewer Low Risk Vulnerabilities Than Other CNAs in 2024 and Continues Through 2025
In 2024, there were 860 vulnerabilities published requiring high level authentication, such as admin or editor, in order to exploit. Wordfence only assigned 23.4% of all high-level authentication required vulnerabilities. This is due to the fact that these are considered out of scope for our program, and deprioritized over in-scope submissions in our queue.

Additionally, Wordfence disclosed substantially fewer Cross-Site Request Forgery and Reflected Cross-Site Scripting vulnerabilities than Patchstack, disclosing only 27.1% of all vulnerabilities of these types, while maintaining a higher disclosure percentage than WPScan.
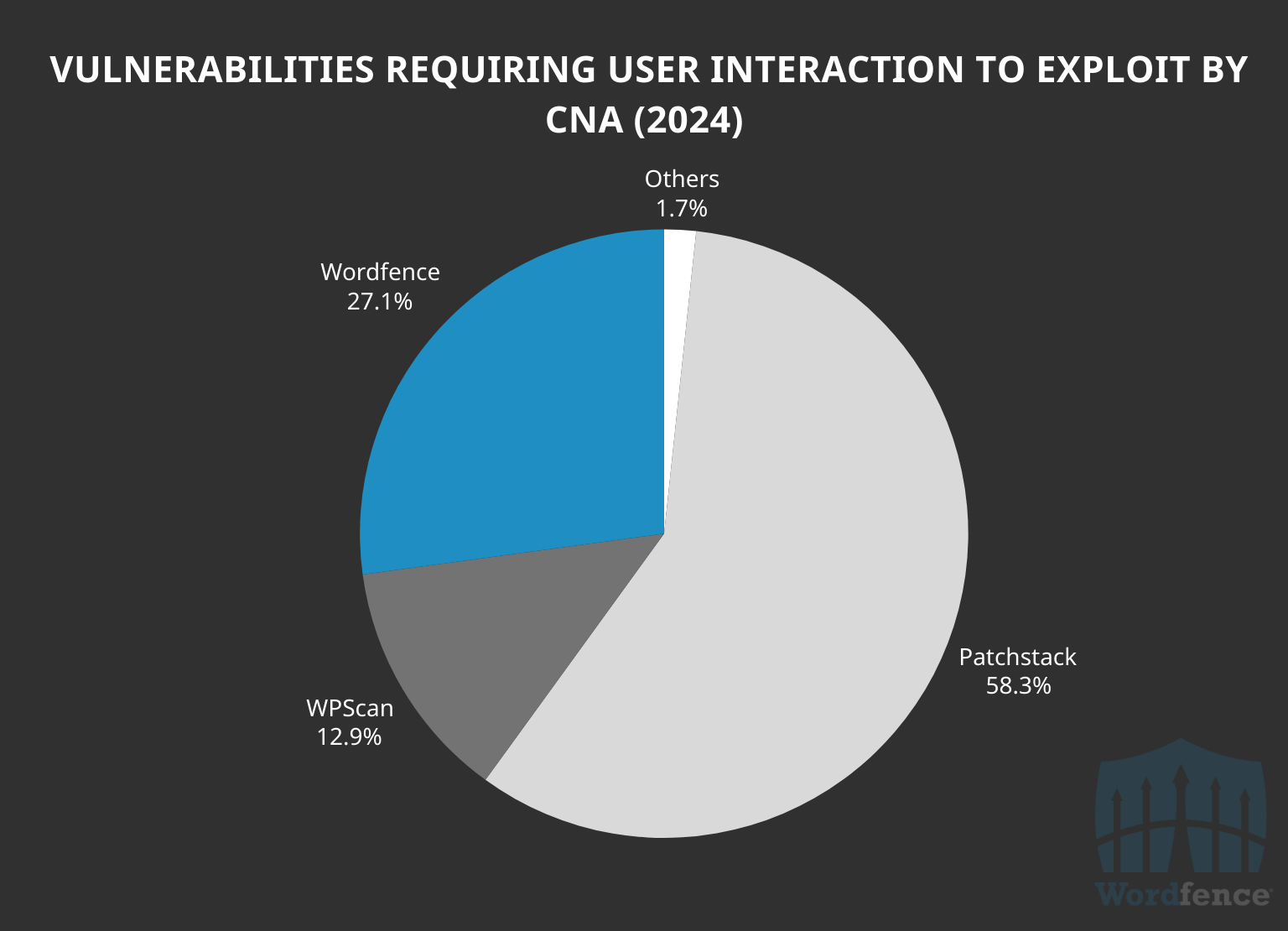
An interesting highlight here is that 32% of the vulnerabilities WPScan processed last year were for low-risk user interaction required to exploit vulnerabilities and 32.5% were for low risk high level authentication required vulnerabilities. This means that 64.5% of all the vulnerabilities that WPScan disclosed last year are not going to be a major risk to most WordPress sites.
The same trend is present so far in 2025. We have assigned fewer CVEs to high-level authenticated vulnerabilities in 2025 accounting for only 20.5% of the 386 vulnerabilities.
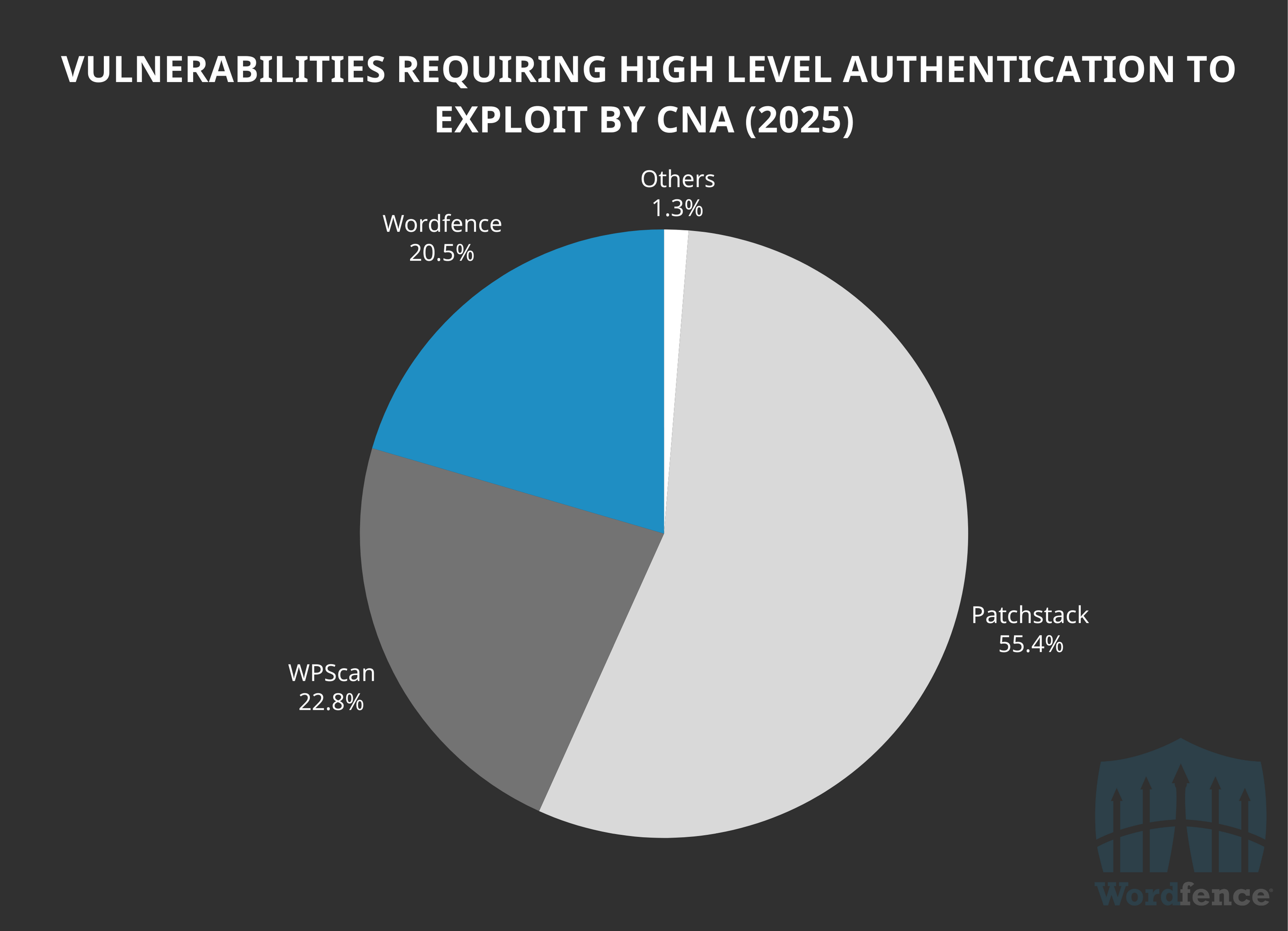
We have also processed and assigned fewer CVEs to Cross-Site Request Forgery and Reflected Cross-Site vulnerabilities than at least one other CNA with just 12.6% of the total 1,637 published so far this year.
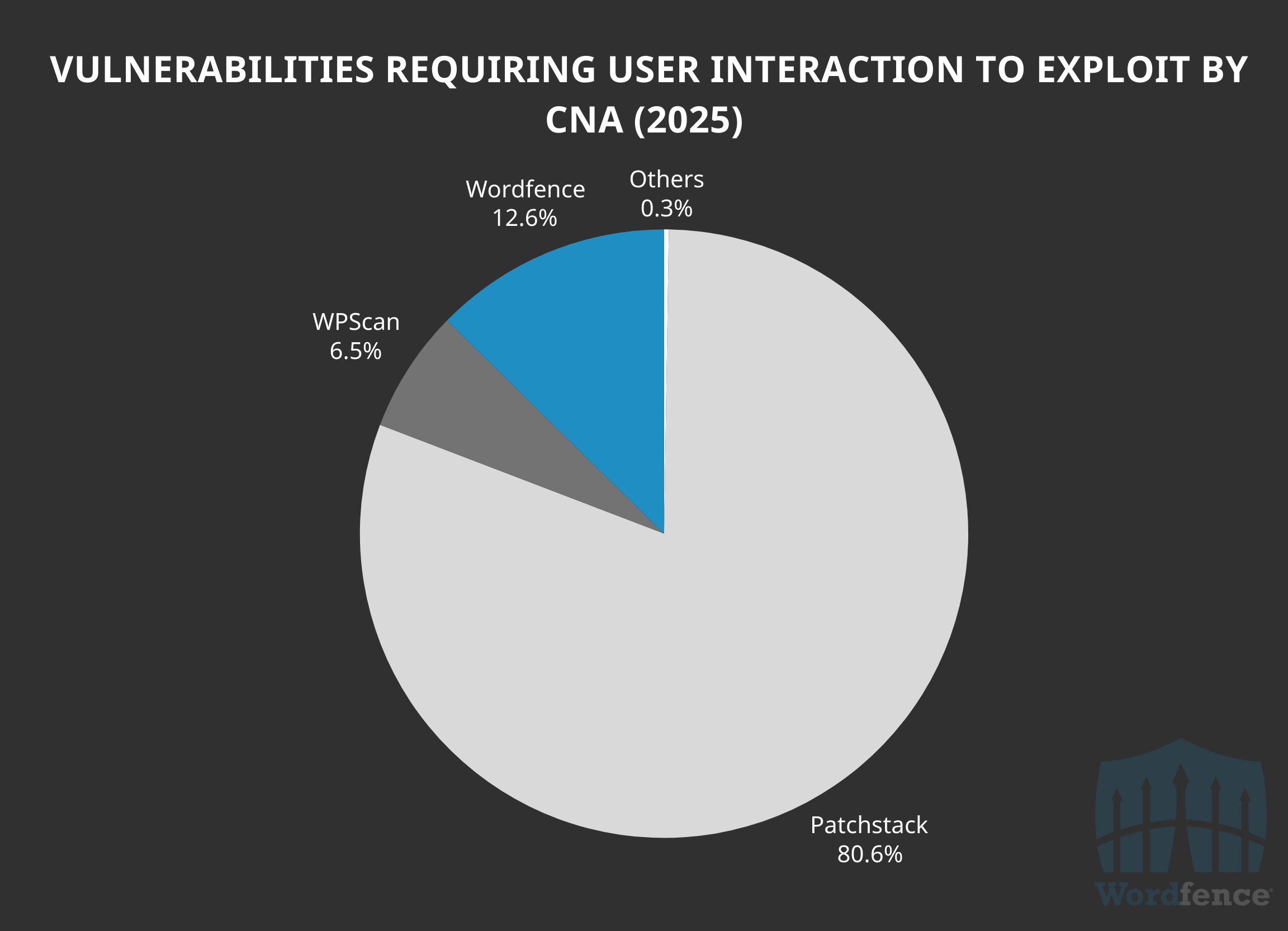
Interestingly, WPScan has only assigned 217 CVEs this year, and 107 of those were Reflected Cross-Site Scripting and Cross-Site Request Forgery, while the other 79 required administrator or editor-level permissions to exploit. This means 85.7% of the 217 CVEs WPScan published so far this year are low-risk issues that likely won’t be exploited, and the rest of their data comes from Wordfence or Patchstack.
Another interesting highlight is that Patchstack has already disclosed more Cross-Site Request Forgery and Reflected Cross-Site Scripting vulnerabilities this year than in 2024, representing 44.2% of their total disclosures in 2025. In contrast, these only constitute 15.8% of the total published vulnerabilities by Wordfence this year. This illustrates Patchstack’s focus on quantity rather than quality in vulnerability disclosures.
It’s Not Just The Data Either
While Wordfence clearly leads in actionable vulnerability intelligence, that’s not all that matters when determining the best vulnerability intelligence provider and security solution.
The Only Data Provider with Completely Free to Access API
Wordfence is the only WordPress vulnerability provider with a completely free to access vulnerability API that you can utilize as needed commercially or independently.
This means we’re not only the first to alert on the most threatening issues that most site owners will be affected by, but we also provide this information back to the community for free with all the details needed to prioritize site-level remediation like CVSS, a description, link to changeset, and more.
You can utilize our complete dump of vulnerabilities via the API documented here: https://www.wordfence.com/help/wordfence-intelligence/v2-accessing-and-consuming-the-vulnerability-data-feed/
Alternatively, you can utilize our webhooks to receive real-time notifications when a new vulnerability has been added, updated, or removed from our database: https://www.wordfence.com/help/wordfence-intelligence/wordfence-intelligence-webhook-notifications/
Industry Leading Bug Bounty Program Attracts the Best Researchers to WordPress
Our industry leading Bug Bounty Program rewards researchers for each and every in-scope vulnerability they find and report, and also provides bonus awards through our researcher referral program and monthly streak detector bonus. Wordfence also provides the highest bounties in the WordPress ecosystem for vulnerabilities with rewards all the way up to $31,200 for the most critical and impactful issues. It is possible for the most successful researchers to earn a living wage bug hunting in WordPress through our Bug Bounty Program, and that is what attracts the very best of the best bug bounty hunters to contribute to WordPress security. Last year, we had one researcher who earned just shy of $60,000 alone through their contributions of 242 vulnerabilities.
At Wordfence, we believe that researchers come first which is why we always take steps to positively improve the researcher experience so they will continue to contribute back to the WordPress ecosystem. Furthermore, we foster an active and vibrant community on Discord, allowing us to communicate directly and in real-time with our researchers. This dedication means that Wordfence is often the place researchers go to report the most impactful and critical security issues, which in turn means those using Wordfence will be the first to be protected and/or notified of a serious vulnerability on their site.
Comprehensive Vulnerability Coverage
Wordfence takes a comprehensive approach to maintaining its vulnerability database. Not only do we diligently add vulnerabilities discovered and processed by our own team, but we also keep a close watch on external sources and other WordPress CNAs. This ensures that any vulnerability disclosed by other providers is also included in our database.
Choosing Wordfence as your security solution doesn’t mean you’ll miss out on valuable vulnerability information reported elsewhere. In fact, it gives you a significant advantage. You’ll be among the first to know about high-impact and high-severity vulnerabilities that Wordfence discovers and discloses. Additionally, you’ll receive alerts about vulnerabilities reported by other organizations, all completely free of charge.
By integrating data from multiple sources, Wordfence provides a comprehensive and up-to-date vulnerability database. This ensures that you have access to the broadest possible range of vulnerability information, helping you stay ahead of potential threats and keep your systems secure.
A Company You Can Trust: 100% Founder Owned and Operated
Wordfence stands as a pillar of trust in the WordPress security landscape with over 5 million active installations. Our commitment to excellence is further underscored by our ISO 27001 certification, a testament to our stringent information security management practices.
Our team comprises seasoned security experts, analysts, and researchers, each equipped with a formidable arsenal of industry certifications, including CISSP, OSCP, and OSWE, among many others. These credentials signify a deep understanding of security protocols, penetration testing, and web application security, respectively which is used when designing and operating our Bug Bounty Program, maintaining our database, and protecting our users.
Furthermore, Wordfence remains proudly 100% founder owned and operated. This autonomy liberates us from the pressures of external stakeholders and profit-driven directives. Our focus remains unwaveringly on fortifying the WordPress ecosystem, strategically channeling our resources to where they can yield the most significant impact. We are driven by an unwavering commitment to security, not by the whims of a boardroom. This independence allows us to prioritize the long-term health and safety of the WordPress community over short-term gains.
Wordfence: The Clear Leader in WordPress Vulnerability Intelligence and WordPress Security
In this report, we have demonstrated that while Wordfence may not lead in the total number of disclosed vulnerabilities, Wordfence leads where it matters most: impactful vulnerabilities, high-threat issues, responsible disclosure practices, and common and dangerous vulnerabilities that pose real risks to real site owners. Our commitment lies in delivering high-quality, actionable vulnerability intelligence that directly benefits Wordfence users and the broader security community through the Wordfence Intelligence platform.
We believe the most effective vulnerability research strikes a balance between quality and quantity. A high volume of disclosures without sufficient vetting can generate noise, burden developers, and distract from serious threats. Conversely, an overly narrow focus on only a few issues can limit coverage. At Wordfence, we aim to maximize value by prioritizing research that delivers the greatest positive impact, while also driving broader discovery through initiatives like our Researcher Bug Detector Monthly Bonus, which still encourages in-depth, high-quality contributions but rewards consistent contributions.
Organizations must consider what they value most in a security provider: a vendor like Wordfence that receives early access to vulnerabilities and delivers proactive protection for the threats that will most likely be targeted and impact the largest number of sites, while still offering coverage for lower-risk issues, or an alternative one that has to react to critical vulnerabilities after disclosure, often racing to implement protections after the fact because they mainly process low risk low impact issues.
When evaluating a security partner or provider, it is essential to look beyond surface-level metrics such as the number of vulnerability disclosures. While volume can appear impressive, it does not necessarily correlate with improved security outcomes.
Wordfence takes a comprehensive and strategic approach to vulnerability intelligence. We assess each vulnerability in the context of its real-world impact, ensure responsible and effective disclosure, and actively support remediation efforts. This enables our users to proactively address risks and reduce the likelihood of exploitation, rather than reacting to threats after the damage is done. By doing so, we help organizations stay ahead of real threats, not just add to the noise.
By focusing on meaningful, high-impact vulnerabilities and maintaining a strong commitment to responsible practices, Wordfence helps organizations strengthen their security posture and allocate their resources where they matter most—protecting against the threats that are most likely to be weaponized in the wild. Our focus on impact, real-world threats, remediation, and proactive protection leads to a stronger, more efficient security posture—allowing you to spend less time sorting through low-risk issues, and more time addressing the threats that truly matter.
Wordfence is the world’s leading WordPress Vulnerability Intelligence provider, especially for truly actionable vulnerability intelligence.
Please note the data for 2025 in this report is accurate up to April 28th, 2025 and will continue to evolve over the year. In addition, there may be some premium software missing from the active install count range counts as it is not possible to accurately determine all premium software’s estimated install base.
The post Wordfence: The World’s Leading Quality WordPress Vulnerability Intelligence Provider appeared first on Wordfence.
